Using a Proxy with cURL Command Line: A Comprehensive Guide
As the digital landscape evolves, individuals and businesses are increasingly concerned about their safety while using the internet. Another challenge users face is restriction from websites and other vital applications due to geographical barriers. With proxies, end users now have the liberty to access any web page without worrying about their identities being exposed.
While they are beneficial, using a proxy with cURL command lines enhances its functionality.
In this comprehensive guide, we’ll be exploring cURL and proxies in their entirety, the use cases and benefits of a cURL-configured proxy, and how these protocols can be configured with command lines.
What is a cURL Command Line and How can it be Used?
The client URL (cURL) is a command line tool that enhances the transfer of data from an end user to a server. The URL in the command line is the location of the server or web page where the data is usually transferred.
cURL is an open-source cross-library (libcurl) that can transfer data across several servers on different operating systems. This command is compatible with different protocols such as FTP, HTTP, HTTPS, DNS, and over 20 others.
The history of cURL dates back to the late 90s when HTTPget, a protocol consisting of hundreds of sidelines, was built, giving rise to cURL HTTPS called HTTP GET 1.0). The name soon changed to urlget 2.0 when FTP support was developed. After several upgrades, the name was finally changed to cURL 3.0.
While cURL, in itself, enhances the transfer of data from a device to a server through internet protocols, it isn’t capable of handling the data. It only undertakes the assignment. cURL can perform numerous functions as several command options exist.
Let’s see how this command line can be used in GET requests to generate the internet protocol (IP) of a particular website.
curl https:ip.website
Here,
- curl https is a GET command for the https protocol.
- Website is the name of the site whose IP address you’re interested in.
Assume this website is NetNut Networks, the command line will appear this way:
curl https:ip.netnutnwtworks.com
How can cURL be Used?
With curl being a notable tool for transferring data through several internal protocols, it follows the command can be vastly used.
Below, we’ll take a look at three ways the cURL command line is used in transferring data.
-
Saving URL-based content to a file
With cURL, files can be downloaded and uploaded to local storage. Even though the process may appear simple, some extra parameters need to be added. Let’s assume we want to store the IP address of NetNut Networks.com in a text file format. To do this, we’ll need to run this command line:
curl -O response.txt https://ip.netnutnetworks.com.
A closer look at the command line shows we added a new augment -O, designating output. Response.txt represents a file name. Should the command be launched, curl visits the website, retrieves the IP address, downloads it to the folder, and creates a new response.txt file. Any preexisting file will be overwritten with this new content.
-
Following Redirects
curl https://google.com
With this command line above, you can have access to the Google search engine to make requests. When you visit some websites, you may be redirected to a different site for further information. Your browser does this automatically.
But with cURL, redirection isn’t automatic. You may be notified that the document that you need to access has been moved.
To get access, a flag – “L” will need to be added to the command. In this case, we should have something like this:
curl -L https://google.com
You will then be redirected to the site.
-
Proxy Connection
With cURL, you connect to any server via a proxy. The command line, however, is nothing different from what we have above except for the introduction of a few flags and attributes. To do this, the command below will come in handy:
curl – – proxy proxyaddress:port https://placeholder:typicode.com/
You may choose to enter the proxy and port number after -proxy, as well as authentication details. The new U-flag will also be introduced.
The command will then appear this way:
curl – – proxy proxy:port -U “username:password” https://placeholder.typicode.com/
Let’s see what proxies are and how they can be set up using cURL.
What is a Proxy Server and How Does it Work?
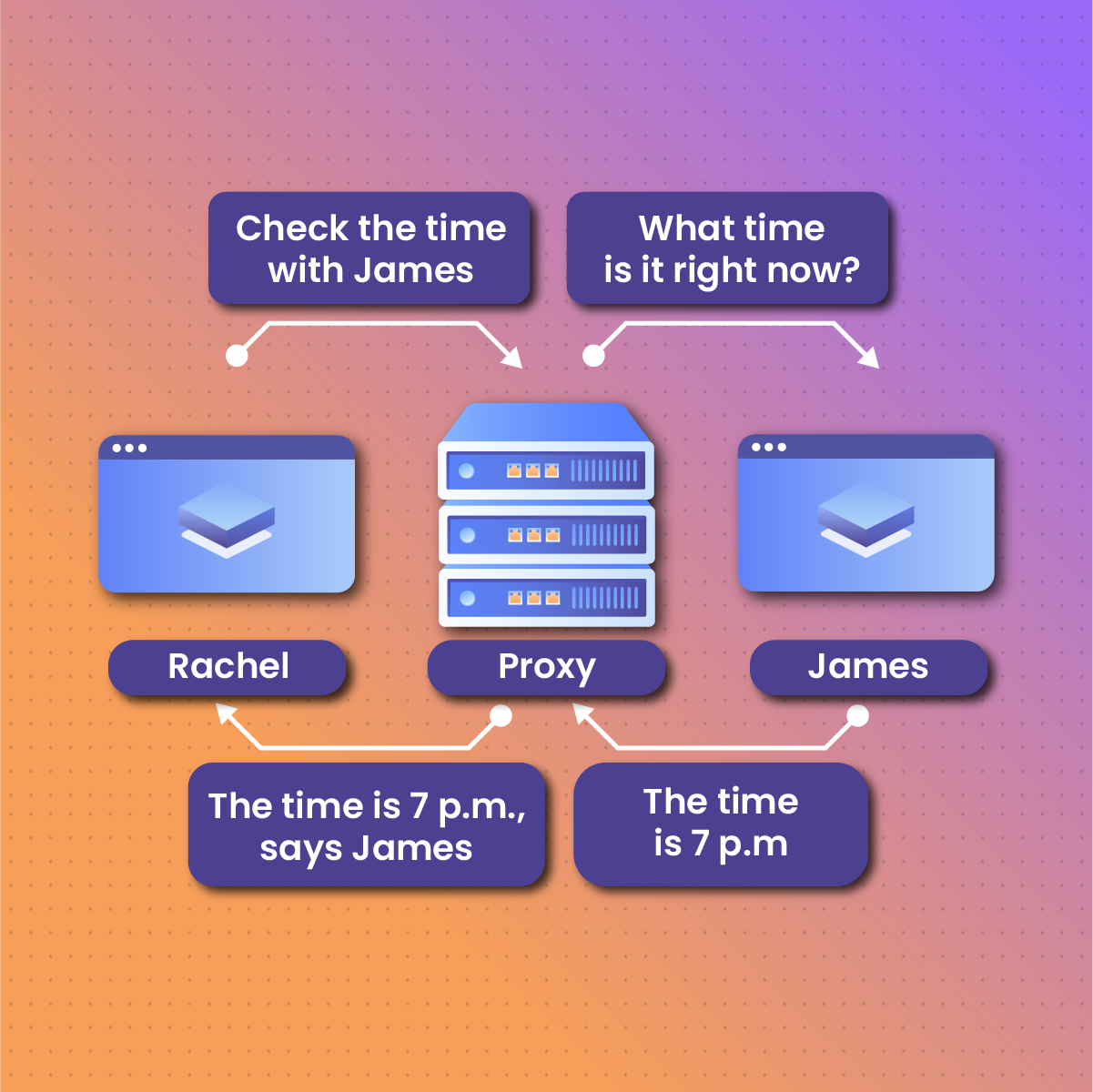
Understanding how a proxy works is quite simple. Every user that has access to the internet has an internet protocol (IP) address. Before a user accesses any website or application, a request is sent from the IP address and the web server, which sends a response together with the website’s data back to the end user.
As a result, a user’s device or location can be tracked from the IP address. Introducing a proxy server enhances anonymity by shielding the user’s IP address and assigning a different address to the user. Additionally, it can help a user access websites with firewalls or geo-blockers. If a website is restricted to a particular region, someone in that same region will be able to access it with the help of a residential proxy.
Proxies are of different types and categorized based on functionality, access, IP server, and anonymity. Read more about proxy types here.
Proxy with cURL – Benefits for the End User
We’ve seen what the cURL command line is and how it can be used. We’ve also explored proxy servers. Using a proxy server with the cURL command isn’t done for formality. It comes with significant benefits.
Below, we’ll explore the benefits end users stand to gain from using their proxies with cURL.
-
Enhanced Anonymity
End users can hide their IP addresses by using a proxy with an aURL command. When they interact with web servers, their identities are hidden completely. Should a user decide to retrieve pieces of information from online domains without anyone knowing, their requests will go through the cURL-configured proxy server before getting to the web server.
Essentially, the proxy conveys the request and response between the user and the internet. Several proxy protocols such as HTTPS, HTTP, FTP, and SOCKS ensure a user stays anonymous when using the internet.
-
Removal of IP Blocker
Due to security or authorization issues, a user’s IP address may be blocked on certain websites or applications. Should they come in contact with such web pages again, they will be denied access. However, a proxy server configured with a cURL command line prevents such by shielding the user’s IP address and allowing them access to the website.
Once the proxy routes the user’s IP address, the website fails to recognize the user’s device. Instead, it considers it to be that of a new visitor.
-
Enhanced Web Scraping
Web scraping generally refers to the collection of pieces of information from online sources. The process may appear simple with many thinking it be manually done. This, however, is different with big corporations that require large volumes of data to be sourced from the internet. These data can be financial, global product pricing, keyword, or marketing data.
Using a proxy typically enhances the process, making large amounts of data to be scraped off the internet within the shortest possible time. Rotation residential proxies that periodically change a user’s IP address will come in handy during web scraping.
-
Bypassing Restrictions and Firewalls
Certain websites and applications can’t be accessed by just anyone due to geographical or centralized restrictions. This means a user who resides in a location different from where the website is hosted wouldn’t be able to access such a site or application. On the other hand, some websites have inbuilt firewalls that serve as a barrier, granting access to only certain groups of users.
With proxies such as residential or SOCKS, a user can have access to any website even if it has any form of restriction. These proxies mask a user’s IP address to bypass the blockers or cloud clusters behind the firewall.
-
Controlled Access and Filtering
Companies can keep their data private by using certain proxies that filter who has access to their intranet. What this means is employees should have access to their company’s intranet but only while using a proxy with credentials unique to them. The company does this to mitigate data leaks and should a leak occur, it can be traced to the origin. A particular category of proxy used in this scenario is known as a transparent proxy. Even though the employees can only access the data with a proxy, their identities and IP addresses aren’t concealed.
-
Security Testing and Ethical Hacking
Cyber security professionals often use proxies with cURL to conduct network testing and ethical hacking. The process of ethical hacking is advanced and involves an offensive form of security testing to obtain technical insight into the vulnerability of a network to prevent possible exploitation by bad actors. With these proxies, security experts can filter and block IP addresses considered high-risk.
Configuring Proxy with cURL Command Line – Step-by-Step Approach
Configuring your proxy with cURL command is quite technical depending on your experience level. However, we’ve simplified the process and will explore it step by step.
It is worth noting that several proxy protocols exist and their configuration with cURL may vary. We’ll be looking at a general Syntax base and see how the code should appear with different proxies.
The Syntax base
Using a proxy server with the cURL command should have this Syntax base:
curl -x <proxy_type>://<proxy_ip>:<proxy_port> <Webpage URL>
Filling the Gaps
If you look at the Syntax base above, you’ll notice that it’s just a skeletal representation of what a proxy with the cURL command line should be. When you purchase a proxy, you’ll be issued details such as the proxy’s IP address, port number, and authentication details, especially if it’s private or to be shared among a close circle of people.
Depending on the proxy, you’ll need to replace the Syntax base as follows:
- The proxy type: Replace the <proxy_type> with the name of the proxy server you’re using. This could be SOCKS4, SOCKS5, HTTP, HTTPS, or FTP. Try to know the name of the proxy protocol you’re using.
- The proxy IP address: Replace this section of the Syntax base <proxy_ip> with the IP address of the proxy.
- The port number: Every proxy protocol comes with a port number. Replace this portion of the Syntax <proxy_port> with the port number. This number may vary with protocols. Ensure you input the correct number.
Authentication Details
When configuring your proxy with cURL commands, you may need your authentication details to complete the process. These details include your username and password. If your proxy requires this, the Syntax baseline will be changed. The code will be similar to what we have above, just that username and password tags will be added and a U-flag will be introduced.
We’ll have something like this:
curl -U <username>:<password> -x<proxy_type>://<proxy_ip>:<proxy_port> <Webpage URL>
Simply go ahead and enter your username and password in their respective tags.
Examples of Protocols in the Syntax Base
Below, we’ll see how different proxy protocols can fit into the Syntax and how the codes will appear. Let’s try just SOCKS5 and HTTP protocols.
- SOCKS5: The proxy’s IP address depends on the provider and the port number is commonly 1080. Let’s fill these details into the Syntax.
curl -x socks5://proxy_ip:1080 http://website URL
- HTTP: Overall, the IP address varies and the port number is usually 8080. Let’s now fill in the details in the Syntax.
curl -x http://proxy_ip:8080 http://website URL
Proxy with cURL in Action
We’ve explored the cURL command line, proxies, use cases, and configuring proxies with the cURL command. How can we then see the proxy with the cURL command play out?
Using a proxy with cURL has use cases such as enhanced anonymity, enhanced data scraping, bypassing blockers, network testing, and so on. But how do the execution codes appear?
In this section, we’ll look at how to execute certain functions using proxies with the cURL command.
-
Bypassing Geo-Blockers
Several people use proxies to visit websites they ordinarily wouldn’t have access to. Let’s assume you’ve always had your HTTP proxy set up on your device but choose to use it with the curl command this time. How can you execute the function?
Simply launch this line of code:
curl -x http://proxy_ip:8080 http://geo-blocked-site.com
Once this function is launched, your request is routed through the proxy, giving access to the site blocked in your region.
-
Enhanced Anonymity
Proxies help an end user stay anonymous during online activities. Here is how the user can launch this function using the code below:
curl -x socks5://proxy_ip:1080 https://websiteurl
This particular function is launched with the SOCKS5 proxy.
-
Web Scraping
Web scraping involves retrieving large amounts of data from online resources. Below is the perfect command line to launch if you’re using a SOCKS5 protocol with a cURL:
curl -x socks5://proxy_ip:1080 https://target-site.com/data.
Once the command is launched, you can retrieve the data without wasting much time.
-
Network Testing
In Network testing, cybersecurity experts conduct technical analysis to determine the extent to which a site is vulnerable. Let’s assume an HTTP protocol that requires an authentication code to be used. The code line will be:
curl -U username:password -x https://proxy_ip:8080 https://vulnerable-site.com
Factors to Consider When Choosing a Proxy Service Provider
Proxies have proven to be beneficial to both businesses and individuals. Choosing the right proxy provider depends on your needs and budget. To streamline the selection process, let’s explore some factors to guide you in choosing a proxy provider.
-
The Purpose of the Proxy
Before purchasing that proxy server, you should know what results you desire from it, and how it fits your needs. Generally, there are proxies for anonymity, bypassing firewalls, accessing online gaming, web and data scraping, SEO, and marketing. Choose the one that aligns with your goals.
-
Size of the IP pools and Infrastructure
The number of IP addresses a provider controls is evident in the size of the IP pool. While some providers have limited addresses, others control over 52 million IP addresses from ISPs, Data Centers, and residential sources. It’s likely a provider with vast IP pools will have robust security infrastructures. Ensure to do your research.
-
Customer Reviews
Before choosing a proxy provider, ensure to check what customers are saying about the platform on either Trustpilot or the website. The star rating is also an indicator of how well the provider performs and the level of customer satisfaction.
-
Budget
Your budget is another factor you shouldn’t overlook when choosing a service provider. The prices of proxies depend on the functionality. Try to compare prices and you might want to check if the platform offers a free trial period.
-
Customer Support
Before purchasing a proxy, ensure the provider has a reputable record of customer support. Check that you can reach out to them using various means at any time of the day. Some providers operate 24/7 while others stick to an 8-hour cycle.
Bottom Lines
Using a proxy with cURL is essential for diverse online activities. We explored the cURL command line and went on to see what proxies are. Furthermore, we highlighted some use cases of using a proxy with cURL to include enhanced anonymity, network testing, removing blocked IP addresses, and bypassing geo-restriction blockers.
We examined the configuration of proxies using the cURL command line in a step-by-step manner and highlighted some examples with SOCKS5 and HTTP protocols.
We concluded by exploring several factors you should consider when choosing a proxy service provider.
Frequently Asked Questions and Answers (FAQs)
What is a residential proxy?
A residential proxy is a pool of inter-woven and real IP addresses that can be used to access websites or applications blocked due to location. These IP addresses are linked to ISPs and are useful in online activities such as torrenting, video games, web scraping, and corporate data extraction.
What are the two major types of residential proxies?
Residential proxies are of two types – static or rotation. With static proxies, the end-user is assigned just one IP address for use during online activities. In the case of rotation proxies, the user’s IP address is periodically changed during online activities, making it difficult to link an IP address to a particular user.
What are ISP proxies?
Also referred to as static proxies, they are usually purchased from internet service providers (ISPs). The IP addresses in these proxies are hosted by servers in Data Centers. Compared to residential proxies, there are fewer hops in the request process and this makes communication between clients and the internet faster.
Usually, rotational residential proxies randomly change the IP addresses of a client while ISP proxies do not. As such, the latter only handles a few requests at a time.
How can you tell if a residential proxy is good for your business?
A residential proxy is good if it suits your business needs. It should be compatible with tools that track growth and marketing efforts, competitor analysis, analyze global product product pricing, and enhance privacy and security.