Proxy Server – A Comprehensive Guide to Security and Anonymity
In today’s integrated virtual space, the idea of utilizing a proxy server appears beneficial as it functions to help maintain stable and safe communication across the internet. Whether you are surfing the net, attempting to gain access to diverse internet-based services, or supervising a network, knowing the exact response to questions like “What is a proxy server” is important.
This article presents you with answers to such a question about proxies, including the details about how they function, the different variants in which they exist as well as their use cases. We will also explore other proxy substitutes that have been adopted by many to achieve similar results over the years. Sit tight and let us explore all of these juicy contents together!
What is a Proxy?
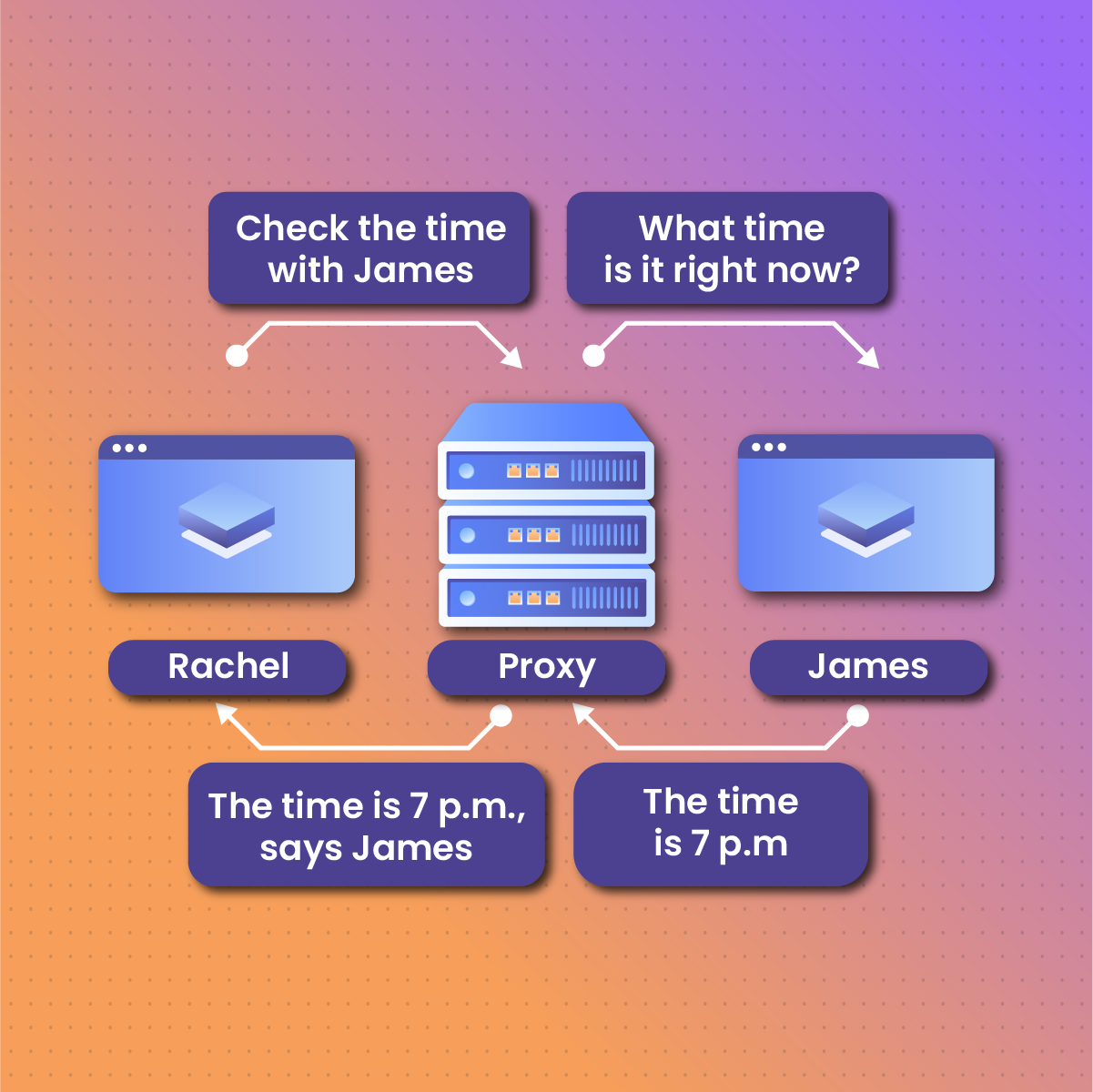
A proxy functions as a mediator between a user’s computer or cell phone and a targeted website server in the online space. Anytime a client transmits a request to gain entry into an online site or content on the web, the proxy’s aid which happens to be its server first gets a hold of the transmitted request before sending it across to the target server in the interest of the client.
A proxy’s mediation for a client is due to its ability to shield the original IP address of the user, replacing it with its generated IP. Assume that an online site places a ban on many IP addresses and only allows specific IPs to gain entry into accessing its content, thereby restricting your access as well. By utilizing a proxy, you can conceal your original IP, which may already be on the website’s blacklist, and gain access with the proxy-generated IP.
What is A Proxy Server?
A proxy server is a reliable protocol or software innovation that carries out the function of a proxy. It functions on a network, acting as an intermediate between a user’s computer or smartphone and the online space. By being a link that connects the user’s device and a targeted online server, the proxy server plays the role of an added layer to manage network contact.
Proxy servers are structured to provide diverse services like caching recurring access requests and feedback information, filtering internet traffic, increasing security and privacy by concealing its user’s main IP address, and many more. These servers also exist in different types, with each of them structured to function in different ways.
But before we get on to this detail, let us explore the step-by-step format of how the proxy server functions as a middleman between users and the online world.
How Does a Proxy Server Function?
For a better understanding of how the proxy server works to carry out the middleman role of the proxy, let us dissect its action from start to finish.
- User Request. As soon as a user establishes contact with the internet space by transmitting an entry request to a website or content source online, its contact is first made to reach the proxy server.
- Blocking the Request. The proxy server gets a hold of the user’s request instead of letting it move across to the target site directly. This request comprises data such as the uniform resource locator (URL) of the site to be explored and the intended action alongside other important information.
- Transmitting the access request. The proxy server later transmits this access request received from the user to the relevant target server. This server may be one of the servers housing the target website or content intended to be accessed, like a web server, an app server, or even a file transfer protocol server.
- Contact with Targeted server. As soon as the proxy server attempts to forward the access request in the interest of the user, it initiates a connection with the target site server. It transmits the user’s access requests and holds until feedback for the request is transmitted.
- Feedback from Target Server. The target server obtains the entry requests forwarded by the proxy and interprets it as a request that originated from the proxy server, oblivious of the presence of a user. It then reviews the request and develops feedback that comprises the access that is being requested for or otherwise.
- Transmitting the Feedback. The proxy server obtains the feedback transmitted from the target server. It reviews it and transmits it to the user who had initially initiated the access request.
- User Interaction. The user’s computer or smartphone obtains the feedback transmitted by the proxy server as though it has directly been transmitted from the target resource server. The user is, therefore, given access to the online site or the details of the feedback that he received.
The Role and Applications of Proxy Servers
Proxy servers are beneficial in diverse areas. Without much delay, let us review some of its standard roles and applications across various contexts.
Caching
Proxy servers are structured to cache regularly used internet data or information. How does this happen? Anytime a user initiates an access request to a website or content on the internet, the proxy server reviews if such content has already been transmitted past it before. If such content already passed through it before, then it would have a stored copy that will probably be utilized to resolve the user’s request. Such action is aimed at limiting the time used up in transmitting and waiting for feedback from the target website to be explored. Caching activities contribute to handling intense network traffic and aid performance.
Filtering and Data Management
Proxy servers can assist in filtering content that causes traffic on the web according to certain set rules. They can restrict entry into certain suspicious online it’s, block access to specific types of data or content, especially in an office setting, and impose information rules to guarantee adherence and effectiveness.
Privacy and Anonymity
Proxies, with the aid of their servers, can offer anonymity services to users by functioning as a mediator between that specific user and the online web. They shield the user’s original IP address, including certain details about the user, such as location, and then replace the IP with a proxy-generated IP, making it tough to track down the user through the transmitted request. This element is mostly useful for individuals or turns that aim to maintain a significant level of privacy while surfing the internet.
Bypassing Geo-Restrictions
As accessible as the online space can be for everyone, it is still home to websites that place blocks on specific access, especially from individuals who are not in the same geographical location. In such a case where a user is not allowed to gain access to geo-restricted content or a website, the proxy server becomes useful. This server can conceal the user’s original IP address which contains details of the user’s location. Then it moves to replace this concealed IP address with it’s server’s IP address which will enable the user to gain access to that restricted website or content.
Load Stabilizing
Proxy servers can allocate users’ requests across diverse servers to help stabilize the load, rather than overworking one server over another. Through such balancing action of inbound requests, there is the guarantee that no single server is overloaded, leading to enhanced speed and functional abilities of these servers.
Security and Supervision
A proxy server is one best bet when it comes to maintaining an applaudable level of security in the online space. This is because they function as a barrier between users and the web, offering security assistance. They are equipped to review traffic, disclose and restrict malicious actions, and filter suspicious content that may pose a great risk to user’s security. They also act as firewalls to supervise and monitor the network in case of any unwanted entry and dangers.
Access Management
Proxy servers function to control certain access actions by verifying clients before letting them access certain online sites or content. This is mostly utilized in an office setting where the network is being supervised to help limit access to certain sensitive apps, information, and public sites.
Bandwidth Boost
Proxy servers are useful to boost bandwidth utilization through the compression of information files before they are forwarded to users. This action helps to limit the logged amount of information sent across the network, leading to improved speed in downloads and bandwidth expenses.
Supervising and Recording
Proxies are helpful to record and review traffic in a network, delivering beneficial insights into utilization routines, speed metrics, and privacy events. Such data can be utilized for functionality strategies, security reviews, and troubleshooting.
Types of Proxy Servers and How They Function
Proxies exist in various types that have different functional abilities. This is why you must get acquainted with all of them to make the right choice at the time that you decide to utilize one.
In this section, we will be listing and explaining the different types of proxies in different categories like price, direction of use, source, anonymity, rotation, protocol, and so on. Let us give in already
-
Classification of Proxy Types by Price
Right before we get on to the main facts, it is worth noting that you can either decide to spend money in obtaining a proxy service or you can settle for a publicly accessible one that is cost-free. Under this category, we have the free and the paid proxy. Let us explore them.
Free Proxy
These types of proxies are often referred to as website-based proxies as they are mostly seen on diverse online sites. As their name implies, these categories of proxies can be obtained and utilized without any attached cost. What this means is that these proxy servers can help you mask your original IP address while they display the proxy-generated IP to keep your details private. While they sound good, they are not exactly your best bet due to certain constraints that confront their use. Free proxies are often legging in their abilities due to their number of uses. They are also quite risky to use as you can not be certain if the zero cost attached is at the detriment of your information being exploited. You must utilize such a variant of proxy with caution to avoid any form of cyber attack. If possible, ensure to utilize such proxies in cases where sensitive information is not involved.
Paid Proxy
This category of proxy, as their name indicates, is a type of proxy whose usage comes at a cost. This means that you must pay to obtain them and utilize their IPs as a shield to your original IP address. While their cost may be a setback factor, it is important to note that they are considered to be more useful as they offer better user experience and performance. This is because they do not always record a high number of users as compared to the free proxy variant. Nonetheless, it is always preferable that you obtain your paid proxy from a reliable source as that is the only assurance of getting the kind of privacy and security you aim for. Some of these proxies providers usually provide trial periods for their customers as well as a cash-back guarantee.
-
Classification of Proxy Types by Direction
The direction of a proxy determines which end gains from the presence of the proxy, the client that initiates an access request or the server that gets the requests and grants or denies them.
Forward proxy
A forward proxy is a type of proxy that functions in the interest of the user and transmits a request to a target site that is intended to be accessed online. Let us dissect it better.
When utilizing a forward proxy, the client is expected to initiate a request sent from his device, be it a computer or a smartphone. As soon as that request is initiated to be sent to the online site that he intends to gain access to, the forward proxy interests and gets a hold of the request before it is forwarded to its intended destination. At this point, the forward proxies carry out specific tasks like concealing the user’s IP address and replacing it with a proxy IP, caching the content of the request for future needs, and so on. After all this is completed, the forward proxy transmits the request down to the intended destination.
Also, as soon as the targeted site obtains the requests and generates feedback for it, it transmits it down to the forward proxy takes another action to cache and filter certain unwanted content before transmitting it back to the user’s device. With a forward proxy, you are assured of surfing the web with a significant level of privacy and anonymity as your location can not be detected with the proxy IP presented by the proxy.
Reverse Proxy
Reverse proxies are the exact opposite of forward proxies. These proxies function to handle traffic that is transmitted to an online site server. What this simply means is that they do not work on behalf of a user but a website. Let us illustrate how they function for better understanding.
When a user transmits an access request through a browser or device, it is usually obtained by a reverse proxy right before it reaches the background server of the website that is intended to be accessed. The user is often oblivious to the existence of a proxy, such as the reverse proxy. As soon as the reverse proxy obtains the forwarded request, it reviews it to ascertain the background server that is most suited to deal with it. Afterwards, the reverse proxy transmits the user’s request to the most suited server, thus, acting as a mediator between the background server and the user. The background server reviews the request and transmits generated feedback to the user, through the reverse proxy. Online sites often employ reverse proxies to enhance security, stabilize traffic, and shield themselves from likely DDoS invasions.
-
Classification of Proxy Types by Anonymity
For every request that you forward on the internet through HTTPS protocol, there are corresponding titles that comprise specific data about your computer or smartphone. Proxies assist in altering these titles, noticeably or otherwise. On this note, the types of proxies can be categorized into transparent, explicit, and high anonymity proxies.
Transparent Proxy
This is a type of proxy that functions as a mediator between a user and a target website, transmitting the user’s request to a specific target online site server and returning the feedback without altering it. Let us illustrate this for better understanding.
When a user sends an entry request from a device to a targeted online site, the request is first made to pass through the transparent proxy without the knowledge of the user. The proxy then transmits this sent-in request to its intended destination server without altering the details of the request. Afterward, the targeted resource or site obtains the request and analyzes it as though it came directly from the user. The destination server develops feedback for the request and forwards it to the user. Again, the feedback is transmitted through the transparent proxy before reaching the user’s device.
This proxy type is mainly useful for network supervision as well as caching regularly accessed data or even for implementing filtering strategies. As they are not equipped to alter requests or feedback, they provide a restricted level of security.
Explicit Proxy
This proxy variant, which is also referred to as a semi-transparent proxy, demands that user’s computers or smartphones be particularly set up to utilize it. Contrary to how the transparent proxy functions, explicit proxies depend on a specific set-up on the user’s computer to reroute traffic from across the proxy. What this means is that the client is fully aware of the presence of a proxy during mediation between his device and the online space. How does this proxy variant work?
Users are required to manually complete the set-up of the explicit proxy, connecting it to their device and noting the proxy’s IP and port code. Afterward, the user is set to send an access request to any target site. The request is first intercepted by the proxy based on its setup before being transmitted to the target site or resource server. Also, the feedback forwarded from the target site is transmitted through the proxy before it reaches the user’s device.
Explicit proxies shield your original IP address and location. However, they still include titles that imply the presence of a proxy while attempting to access an online site.
High-Anonymity Proxy
This type of proxy is on top of the chain when it comes to maintaining a significant level of anonymity while surfing the internet. These proxies, often referred to as elite proxies, provide the best level of anonymity to users. How do they do this? When a user transmits a request through a high anonymity proxy, it usually reflects that the request is sent directly from the proxy. What this means is that the targeted site to be accessed is unaware of the presence of a proxy as the user’s original IP address is completely concealed and replaced with a proxy IP. This variant of proxy is usually employed for tasks that demand top-level anonymity like getting passed restrictions. By concealing the user’s main IP address and location, high anonymity proxies can guarantee that the user’s identity is completely shielded and made private from any online site that is accessed.
-
Classification of Proxy Types by Source
Here is another necessary category in which proxy variants can be classified. Certain proxies utilize IPs that are logged in data-centers and others originate from existing residential clients. Let us take a look.
Data-center Proxy
This a a classification of proxy proxy that obtains it’s IP addresses from data-center servers. What this implies is that they are, in no way, affiliated with any ISP or outlet, causing them to be more vulnerable to getting detected and banned. To utilize this proxy variant, you are required to obtain a developed one from a data-center in which you can transmit your requests.
A major advantage of utilizing this variant is their cost-effective nature alongside the enhanced performance of their network which is powered by strong servers. Also, they offer a relatively significant degree of privacy and anonymity as they permit their clients to rotate the IPs at specific times.
Residential Proxy
This class of proxy incorporates IP addresses designated by specific ISPs. This proxy variant is often more useful for surfing many online sites, especially the ones with set-up measures to ban suspicious IP addresses. Why is that so? They are often detected as real users, rather than bots when used to access these online sites. Let’s explore some major facts about this proxy variant:
- They offer an increased level of anonymity and reliability when utilized to transmit traffic to the online space.
- These proxy variants may not function at high performance as compared to datacenter proxies. This is because they are fully dependent on the normal internet setup, which may not work at the best speed and stability.
- Specific residential proxies offer IP address switching as they permit individuals to rotate the use of different IPs to avert online recognition and to get through to geo-banned content and websites.
Mobile Proxy
This kind of proxy works better with mobile devices because they function with SIM cards rather than the usual Wi-Fi network connection. These proxies transmit requests through a mobile connection so that the request is perceived as though it came from a mobile. A mobile proxy is often more effective in maintaining an increased level of privacy as it utilizes IPs from mobile networks that are not regularly viewed to be linked with proxy-related actions. This proxy variant also has different IPs allocated to the smart device and can be alternated for internet privacy and anonymity.
Static Residential Proxy
This is a proxy variant comparable to the residential proxy, but with static IPs that are not subject to modifications. What this implies is that when a client employs such a proxy, there is no switching of IPs as there is just one fixed IP attached to the proxy. Such a feature is excellent for carrying out specific online tasks and online sites tend to view such variants of proxy as less suspicious due to their known static IP. Nonetheless, such a proxy may not offer that level of privacy and anonymity a user might need to get past certain online access limitations.
-
Classification of Proxy Types By Exclusivity
Proxies can be classified according to how exclusive they can be. Let us check it out:
Shared Proxy
As the name denotes, these are proxies that can accommodate diverse users at the same time. They are also referred to as public proxies because their IPs are collectively used by all of the clients that are connected to their servers. Utilizing such a proxy means incurring less expense as compared to the other proxies that will be explained below. On the other hand, they can experience a lag in network performance due to the number of people utilizing them.
Semi-Shared Proxy
These proxies are somewhat exclusive, that is, they stand between fully exclusive and public or shared proxies. Semi-shared proxies accommodate diverse users, but unlike the shared proxy, the numbers have a limit, paving the way for a more improved speed in all of its activities. Individuals connected to utilizing this proxy often have better management over the set-up of the proxy server as compared to that of the public or shared proxies.
Private Proxy
This proxy is often tagged as a dedicated proxy, indicating that it is a highly exclusive proxy whose IP is made available to a user, giving the user exclusive rights to management. Private proxies are mostly relied upon for their speed and ability to handle complex tasks like scraping and SEO supervision, among others.
-
Classification of Proxy Types by Protocol
The protocols are what determine how you can initiate contact with online sites and content. There exist major proxies under this classification: HTTP, HTTPS, and SOCKS5. Let us throw more light on them.
HTTP Proxy
This variant of proxy functions as a mediator between a user and a specific server. As soon as a user takes the step to initiate an access request to an online site, an HTTP-based request is first transmitted to the proxy, rather than forwarding it directly to the target online site. This proxy then transmits the request to the intended destination in the interest of the user while it also intercepts feedback from the destination server before sending it back to the user.
An HTTP proxy is mainly set up to take care of HTTP requests, implying that only traffic containing HTTP or HTTPS. They are beneficial in helping to filter requests and feedback, cache, and conceal a user’s original IP address.
HTTPS Proxy
An HTTPS proxy is focused on taking care of decoded HTTPS requests. The proxy is a form of the HTTP proxy that adopts SSL and TLS decoding techniques to improve the security of the interaction between users and a specific online server. Unlike the HTTP proxy, HTTPS proxies assist in decoding HTTPS-based requests, reviewing them, and re-encoding them before they are transmitted to the intended online server.
HTTPS proxies are your best bet when it comes to situations that require high-security interaction like entering an online site that utilizes HTTPS encoding measures or avoiding network monitoring. They offer extra security by functioning as a mediator to initiate secure interaction in the interest of the user.
SOCKS5 Proxy
While HTTP and its lookalike function handle online traffic, the Secure Socket 5 proxy assist with diverse kind of traffic, inclusive of those related and not related to the web. They function at a lower level, transmitting information from the user to other servers and back without altering or interfering with the data. This makes them the perfect fit for direct interactions with a target server.
-
Classification of Proxy Types by Rotation
Specific proxies tend to stick with utilizing one IP address while others are dynamic. Let us take a look:
Static Proxy
These are proxy variants that can be utilized to shield your original IP with a particular proxy-connected IP. This IP does not change with time. They are mostly helpful if you intend to stick with a particular identity, like in a case where you monitor some social accounts. This proxy variant is not exactly an excellent pick for complex tasks that may put it at risk.
Rotating Proxy
Rotating proxies incorporate diverse IP addresses that can be configured to change as different requests are being forwarded or at a specific time. It is an excellent pick for users who intend to carry out scraping activities or access geo-restricted content or online sites. None of the IPs connected to a rotating proxy can reflect your original identity or location. Also, adopting such a proxy means you do not have to get bothered when one IP gets restricted as others are waiting to be automatically used.
Proxies vs VPNs: Which is the Best For You?
Proxies and Virtual Private Networks (VPN) operate with different intents and the case of which is more useful is solely reliant on your exact need.
Proxies function as mediators between users and specific online servers, transmitting requests and feedback between both parties in the interest of the user. They are useful for caching contents, and filtering inbound and outbound data while shielding your original IP address from the online space. These innovations can be pretty easy to set up and prepare for use. Nonetheless, they cannot be that useful to offer encoding and decoding services between users and the targeted online site.
On the other hand, VPNs are higher protocols that offer encoded interactions between users and an online server, giving a better guarantee of security and privacy. Their ability to offer an increased level of security makes them beneficial for safeguarding sensitive information, especially when your device gets connected to a shared Wi-Fi.
If you aim for a top-notch security protocol that can let you access diverse areas of the internet with low risk, then you may just want to opt for a VPN. However, it is worth noting that if your main aim is to simply stay private in the online space with the capacity to explore sites without certain set restrictions, then you may just need a proxy with its ease of setup.
A Basic Guide To Choosing the Right Proxy For You
Opting for the most suitable proxy for you solely depends on your priorities and expectations of a proxy. Here is a brief outline to guide you through the process:
- Outline your requirements
You must specify the exact intent for wanting a proxy. Do you need it to maintain privacy while surfing the internet, to get past restrictions so you can access certain content or resources, or do you just want an improved speed? Having the answers to these questions will set you on the right path to choosing the proxy that will mostly satisfy your needs.
2. Review The Category of Proxies
The next vital step is to get acquainted with all of the existing kinds of proxies, most of which have been explained in the previous paragraphs of this article. Choosing the exact proxy type to suit your needs implies that you review their functional abilities as well as their setbacks. If you are particular about privacy or network performance, then there is a proxy variant that may just be perfect for you.
3. Proxy Geographical Location
If you aim to gain entry into an online site or resource with geo-restriction, then you may want to consider the location of the server that you should obtain. Diverse proxy vendors provide servers for different geographical locations, permitting you to decide the one with your intended location.
4. Trustworthiness and Provider’s Reliability
Opting for a proxy without reviewing the reputation of the proxy source is almost as good as blindly obtaining a proxy without reviewing the ones that are most suitable for your needs. You must scout for feedback from other customers to ensure that the source you are about to engage with is reliable with excellent attention to customer needs.
5. Budget and Cost
You must review the cost attached to obtaining a proxy and compare it with your budget. In such a case, you may want to single out your prioritized expectation of a proxy and analyze if all of it can be fulfilled by a paid proxy or a free or public proxy. Although paid proxies are more likely to offer better performance and functionality.
Conclusion
There you have it, all of the details to demystify your curiosity that may have paved the way for the question “What is a proxy server?”
A proxy, which exists in diverse categories, is an excellent innovation that helps to push for better user browsing experience as it helps to restore security and privacy that appears to have been fading away from the online space.
While it may be a useful resource for getting through certain restrictions and staying anonymous, it should not be exploited for the wrong reasons. Choosing to utilize a proxy to take advantage of the specific content or carrying out an internet attack defiles all of which the proxy was set up to fix on the web.
Frequently Asked Questions and Answers
Is a proxy better than a VPN?
VPNs are mostly utilized in the online space to conceal original IPs and get access to geo-restricted content or websites, which might mean that they are considerably better than a proxy. Regardless, proxies do well to perform some of these functions to a satisfactory level. It is recommended that you check out the features of both protocols and compare them with your needs to find out which is most suitable for you.
What is Proxy Chaining?
Proxy chaining is a concept that defines the process by which diverse proxies are utilized in a chain to transmit requests from a user down to a target online site. All of these proxy servers actively participate in the transmission process, forwarding requests from one to another until they get to the target site.
How do I confirm the kind of proxy that is connected to my device?
You can do this by employing an IP database such as the IP2Location which permits up to 200 IP reviews daily.