In the realm of digital shadows, where anonymity dances a precarious tango with exposure, lies a powerful technique known as “passive fingerprint.” Unlike its flashier counterpart, active fingerprint, which bombards systems with probes and queries, a passive fingerprint works like a skilled observer, gleaning insights from the mere echoes a system leaves behind. But what exactly is this hidden art of identification, and how does it shape our online landscape?
Imagine a bustling marketplace where individuals move about, leaving subtle traces with every step. A keen observer, armed with knowledge of gait, mannerisms, and even the scuff marks on shoes, can identify specific individuals without ever directly interacting with them. This analogy mirrors the essence of a passive fingerprint, where analysts deduce the characteristics of a system, like its operating system, browser, or even geographical location, by meticulously examining its digital footprints. These footprints encompass a vast array of data, from the headers of network packets to the way a system interacts with specific protocols.
What Is A Passive Fingerprint?

Browser And System Information
Operating system, browser type and version, installed fonts, screen resolution, language preferences, system plugins, etc.
Hardware Fingerprints
Graphics card details, CPU information, memory configuration, available storage space, etc.
Network Fingerprints
IP address, network configuration, time zone, internet service provider (ISP), geolocation data, etc.
Canvas Fingerprinting
Analyzing the unique patterns generated by a user’s browser’s canvas element when rendering graphics.
WebRTC Fingerprinting
Exploiting the Web Real-Time Communication (WebRTC) API to reveal internal IP addresses and network configurations.
Audio And Video Fingerprinting
Analyzing the unique characteristics of a user’s microphone and webcam, such as background noise or camera distortion.
Decoding The Data Trails Of A Passive Fingerprint
The tools of a passive fingerprint analyst resemble those of a seasoned detective. Network sniffers capture the digital whispers of data packets while specialized software dissects their contents, searching for telltale clues. The time a packet took to traverse the network (Time-to-Live), the size of data it can handle (TCP window size), and even the flags it carries (like the “Don’t Fragment” flag) all become pieces in the puzzle, revealing glimpses into the system’s inner workings.
But a passive fingerprint extends beyond mere network traffic. The way a browser renders web pages, the fonts it supports, and even the subtle nuances of its JavaScript execution can contribute to the digital profile. Even seemingly innocuous details like screen resolution and time zone settings can be woven into the tapestry of identification.
Applications Of A Passive Fingerprint
Mentioned below are some of the applications of a passive fingerprint that make it a valuable tool across various domains:
Network Management And Security:
Identifying And Tracking Devices
A passive fingerprint helps network administrators discover and understand the devices connected to their network. By analyzing traffic patterns, operating system fingerprints (OS fingerprinting), and other identifiers, they can detect unauthorized devices, track device movements, and ensure proper resource allocation.
Intrusion Detection And Prevention
By recognizing anomalous traffic patterns or inconsistencies in device fingerprints, passive fingerprints can raise alerts about potential intrusions or malware infections. This allows for faster mitigation efforts and protection against network vulnerabilities.
Web Analytics And Content Targeting
Websites can leverage passive fingerprints to gather information about their visitors, such as their operating system, browser, and language preferences. This enables them to personalize content, deliver targeted advertising, and improve user experience.
Anomaly Detection
A passive fingerprint is instrumental in anomaly detection within a network. By establishing baseline behavior for devices and users, any deviations from these patterns can be flagged as potential security threats. This proactive approach enables rapid response to anomalies, minimizing the risk of security breaches.
Cybersecurity And Threat Intelligence:
Attribution Of Cyber Attacks
By analyzing traffic originating from suspected attackers, passive fingerprints can help identify the type of devices and operating systems used, potentially providing clues about the attacker’s origin or affiliation. This information can be valuable for cybersecurity investigations and attribution efforts.
Botnet Detection And Mitigation
Botnets, networks of compromised devices, often leave distinct behavioral and traffic patterns. A passive fingerprint can detect these patterns and identify botnet-infected devices, allowing for targeted takedown attempts or mitigation strategies.
Malware Analysis And Research
Analyzing the network traffic generated by known malware samples can reveal vulnerabilities and communication protocols used by attackers. This information can be crucial for developing defenses against future malware variants and improving network security overall.
Location-Based Services And Marketing:
Indoor Localization And Tracking
By analyzing Bluetooth Low Energy (BLE) beacons or Wi-Fi signals, a passive fingerprint can track the movement of devices within a building or specific area. This technology has applications in retail stores, malls, and airports for personalized advertising, wayfinding assistance, and crowd analysis.
Targeted Advertising And Marketing
Fingerprinting mobile devices based on their network behavior and app usage can reveal valuable insights into user preferences and demographics. This information can be used by advertisers to deliver targeted promotions and marketing campaigns with higher conversion rates.
Fraud Prevention And Risk Management
Analyzing traffic patterns and device fingerprints associated with known fraudulent activities can help identify suspicious transactions and prevent financial losses. This application is particularly relevant for online banking, e-commerce, and payment processing systems.
Passive Fingerprint: Applications In Various Other Fields
Forensic Analysis
In cybersecurity forensics, a passive fingerprint aids investigators in reconstructing events and understanding the behavior of devices involved in security incidents. By examining passive fingerprints, forensic experts can trace the activities of malicious actors and gain insights into the methods used during an attack.
Threat Intelligence
A passive fingerprint contributes to threat intelligence by providing valuable data on the tactics, techniques, and procedures (TTPs) employed by cyber adversaries. This information is crucial for developing effective cybersecurity strategies, including the identification of emerging threats and vulnerabilities.
IoT Security
With the proliferation of Internet of Things (IoT) devices, securing these interconnected devices becomes paramount. A passive fingerprint assists in identifying and monitoring IoT devices on a network, ensuring that only authorized devices are connected and detecting any suspicious activities associated with IoT devices.
Incident Response
In the event of a security incident, a passive fingerprint is valuable for incident response teams. It aids in quickly identifying compromised devices, understanding the extent of the breach, and implementing effective countermeasures to mitigate the impact of the incident.
Traffic Analysis
A passive fingerprint is utilized in traffic analysis to identify and categorize different types of network traffic. This includes distinguishing between normal user activity, suspicious behavior, and potential malicious activities. Traffic analysis based on passive fingerprints contributes to a more granular understanding of network dynamics.
Compliance And Regulatory Requirements
Many industries and organizations are subject to compliance standards and regulatory requirements. A passive fingerprint helps in meeting these standards by providing a comprehensive understanding of the devices and users on a network. This information is crucial for demonstrating compliance with security regulations.
Proactive Security Measures
By continuously monitoring and analyzing a passive fingerprint, organizations can take proactive security measures. This involves identifying potential vulnerabilities, addressing security weaknesses, and staying ahead of evolving cybersecurity threats before they can impact the network.
Insider Threat Detection
A passive fingerprint aids in detecting insider threats by analyzing the behavior of authorized users. Unusual or unauthorized activities by internal users can be identified through a passive fingerprint, helping organizations prevent or mitigate the risks associated with insider threats.
Best Practices For Implementing A Passive Fingerprint
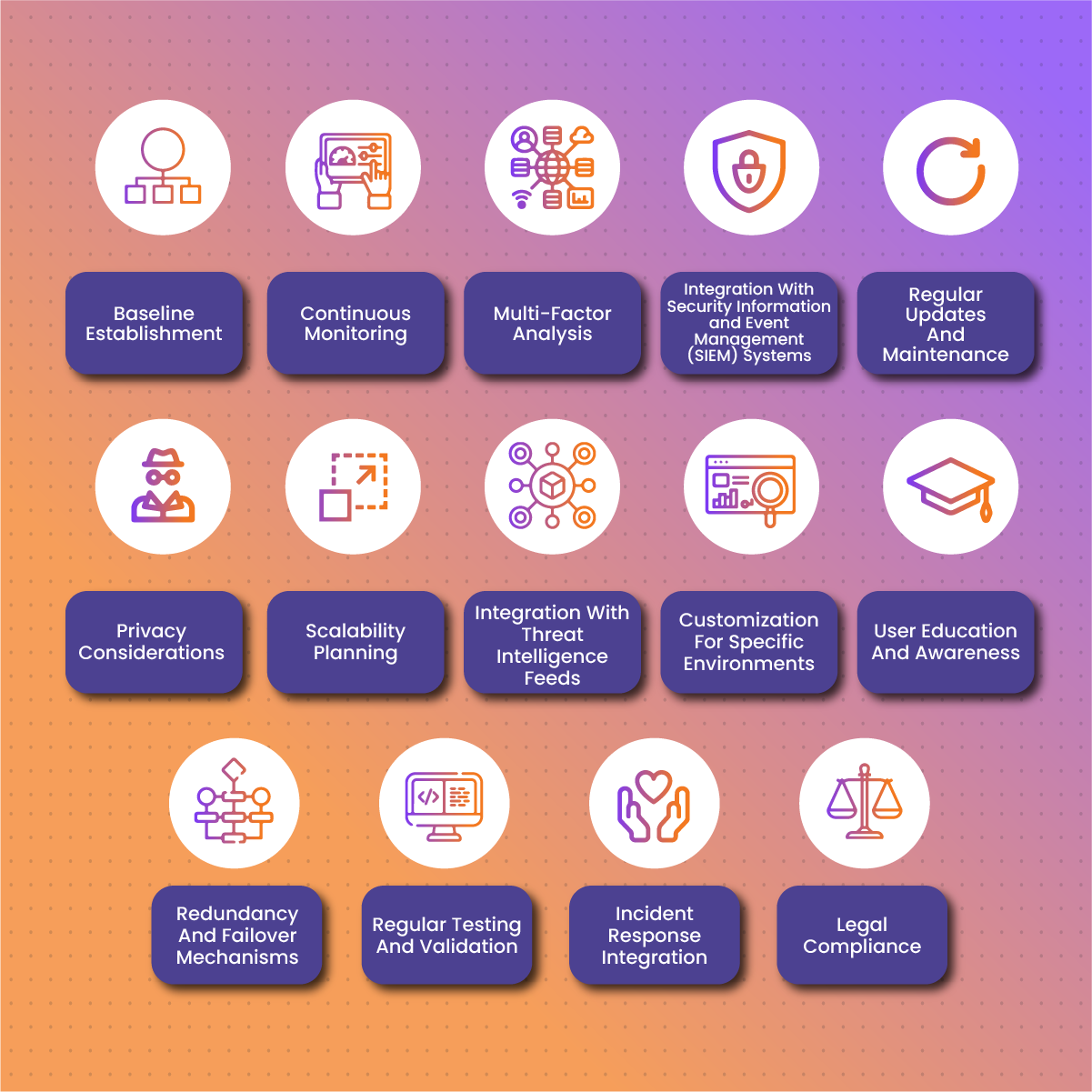
Baseline Establishment
Establish a baseline of normal behavior for devices and users on the network. This baseline serves as a reference point for identifying anomalies and potential security threats. Regularly update the baseline to adapt to changes in the network environment.
Continuous Monitoring
Implement continuous monitoring of network traffic and device behavior. A passive fingerprint is most effective when it operates in real-time, allowing for immediate detection of deviations from established baselines.
Multi-Factor Analysis
Utilize a multi-factor analysis approach, considering various attributes such as device type, operating system, network behavior, and application usage. This comprehensive analysis enhances the accuracy of a passive fingerprint and reduces the likelihood of false positives.
Integration With Security Information and Event Management (SIEM) Systems
Integrate passive fingerprint solutions with SIEM systems for centralized monitoring and analysis. This integration enables correlation of passive fingerprint data with other security events, providing a holistic view of the network security landscape.
Regular Updates And Maintenance
Keep passive fingerprint databases and algorithms up-to-date. Regularly update device and user profiles to account for changes in hardware, software, or user behavior. This ensures that the passive fingerprint system remains effective against evolving threats.
Privacy Considerations
Adhere to privacy regulations and ethical considerations. A passive fingerprint involves collecting data about devices and users, and it’s crucial to implement measures that protect individual privacy while still achieving the security objectives.
Scalability Planning
Design passive fingerprint solutions with scalability in mind. As networks grow and evolve, the passive fingerprint system should be able to handle increased traffic and device diversity without sacrificing performance.
Integration With Threat Intelligence Feeds
Integrate passive fingerprint with threat intelligence feeds to enhance the system’s capability to identify known malicious entities. This integration provides timely information about emerging threats and improves the proactive security posture of the organization.
Customization For Specific Environments
Customize passive fingerprint algorithms and parameters based on the specific characteristics of the environment. Different organizations may have unique network architectures, and tailoring passive fingerprint solutions to these specifics improves accuracy.
User Education And Awareness
Educate users about the passive fingerprint measures in place and how they contribute to overall security. User awareness helps in preventing false positives and fosters a collaborative approach to cybersecurity within the organization.
Redundancy And Failover Mechanisms
Implement redundancy and failover mechanisms to ensure the availability of passive fingerprint systems. In the event of system failures or disruptions, having backup measures in place helps maintain continuous monitoring and threat detection.
Regular Testing And Validation
Conduct regular testing and validation of passive fingerprint accuracy. This involves comparing the passive fingerprint results against known devices and user profiles to identify any discrepancies or areas for improvement.
Incident Response Integration
Integrate passive fingerprint data into incident response processes. This facilitates swift and effective responses to security incidents by providing valuable information about compromised devices or unusual user activities.
Legal Compliance
Ensure that passive fingerprint practices comply with legal and regulatory requirements. Understand and adhere to data protection laws and regulations to avoid potential legal consequences.
Passive Fingerprint: Frequently Asked Questions
Is Passive Fingerprint Secure?
A passive fingerprint enhances security by continuously adapting to user behavior, but proper implementation and encryption are crucial for robust protection.
Can A Passive Fingerprint Be Used For Malicious Purposes?
While the passive fingerprint itself is neutral, its misuse can lead to privacy concerns. Regulations and ethical guidelines are necessary to prevent abuse.
How Does Passive Fingerprint Differ From Active Fingerprint?
A passive fingerprint operates in the background without active user participation, while active fingerprint involves explicit user actions for identification.
How Does Passive Fingerprint Impact User Privacy?
A Passive fingerprint raises privacy concerns, and it’s essential to strike a balance between security measures and user privacy rights through transparent policies.
Can I Avoid A Passive Fingerprint Altogether?
While complete anonymity is difficult to achieve, certain measures like using privacy-focused browsers and anonymization tools can help obfuscate your digital footprint.
Is Passive Fingerprint Illegal?
The legality of a passive fingerprint depends on the context and intent. When used for legitimate purposes and with appropriate safeguards, it may not be illegal. However, using it for malicious purposes or infringing on individual privacy could raise legal concerns.
Passive Fingerprint: Final Thoughts
Passive fingerprint technology represents a paradigm shift in the way we approach digital identification and authentication. Its unobtrusive nature, coupled with the power of machine learning, positions it as a valuable asset in securing our digital landscape.
However, the ethical implications must be carefully navigated to ensure a harmonious integration that respects user privacy while safeguarding against evolving cyber threats. In this rapidly evolving digital age, a passive fingerprint stands as a testament to innovation in the quest for robust cybersecurity solutions.