Transparent Proxy – Exploring its Use Cases and Benefits
Proxies come in different types and classifications and it is important to know which one to use when exploring their diverse benefits and ascertaining the best fit for your needs.
They are crucial forms of technology that are employed in many scenarios for different reasons. As a frequent user of the web, it is possible that you have encountered or used a proxy even without knowing. In offices, firms, homes, public places, or networks, this innovation prides itself as one technology that guarantees a certain level of protection or privacy on the internet.
In this article, we will explore the concept of one of the proxy variants, the transparent proxy, and also how it functions. We will also discuss some use cases of the transparent proxy and why firms opt for it. Then we will proceed to outline the advantages and disadvantages of transparent proxies, a direct comparison between transparent proxies and non-transparent proxies, how to identify and possibly avoid transparent proxies, and factors to consider when enforcing transparent proxies.
What is a Transparent Proxy and How Does it Function?
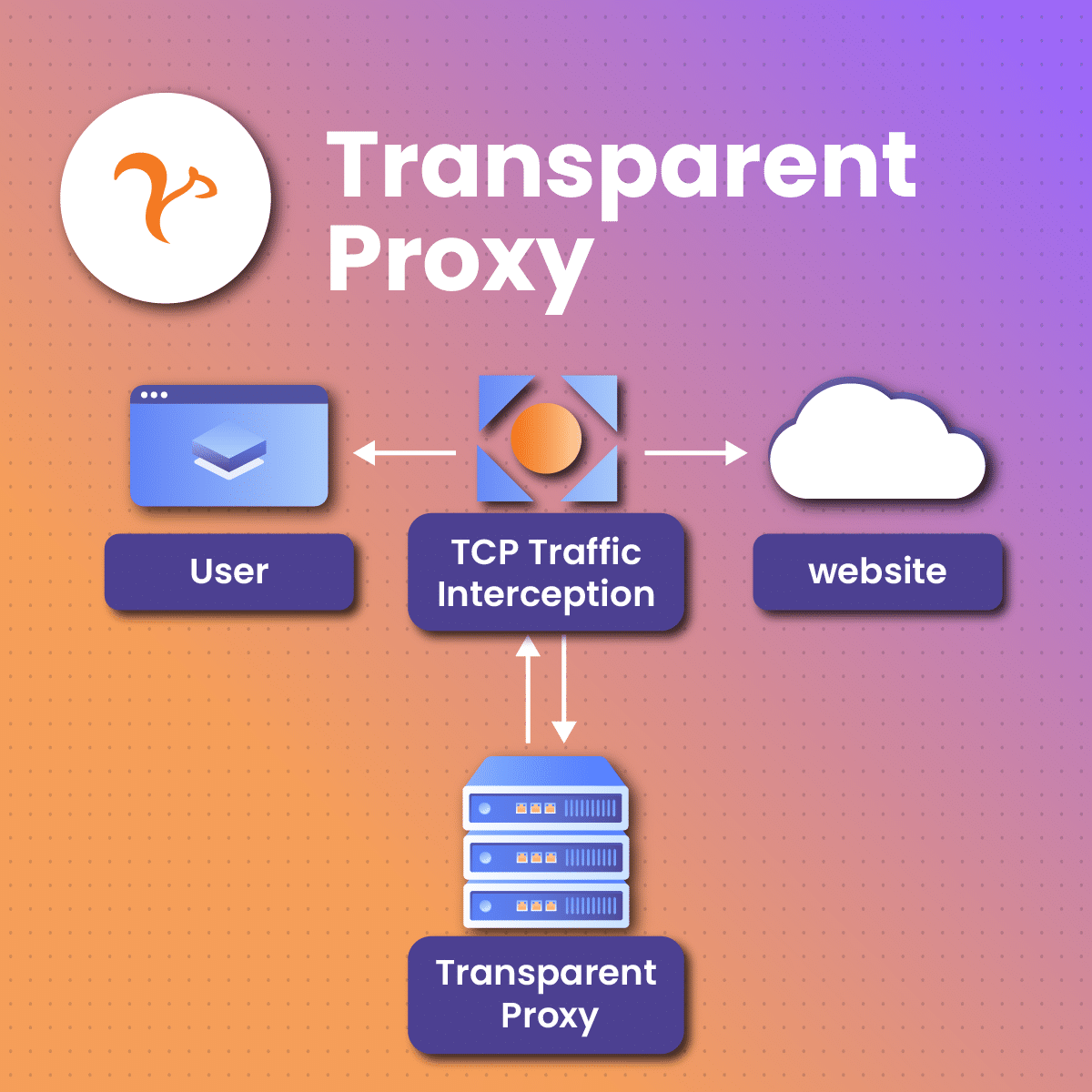
A transparent proxy is a simple type of proxy server that acts as an intermediary between user devices (clients) and target websites that they are trying to access. Oftentimes they do not require user setup and may not even be noticed by the users. As the name implies, a transparent proxy functions transparently. Because users are not aware of their presence, they keep interacting with the target server(s) as though there is no proxy present. Some functions of the transparent proxy include;
- Users launch a request. The user transmits a request to gain entry into a specific online site or content. This request is directed toward the target site server.
- Intercepts the request. The transparent proxy, which operates as a transparent middleman between the user and the target site server, intercepts the request from the user before it is transmitted to the site.
- The proxy then reviews the request and opts to review the blocked request to ascertain if it should respond to the request or transmit it to the target online site server.
- Caching. In a situation where the requested information has already been saved to the proxy’s server memory then the proxy can instantly offer the information to the user without having to transmit the request to the target site. Caching assists in enhancing feedback time and it also limits bandwidth utilization.
- Transmitting request. In a situation where the proxy server has no cached content to dish out as feedback for the transmitted request, it instantly transmits it to the target site server in the interest of the client.
- Obtaining the request. The target site server obtains the transmitted request and proceeds to review it to enable it to develop feedback.
- Obtaining feedback. The target server then transmits the developed feedback which first lands on the transparent proxy server. The proxy reviews the feedback and carries out certain tasks like filtering the data and alteration of the feedback.
- Transmitting the feedback. At last, the proxy server forwards the feedback to the user as though it were directly from the target site server. The user obtains this feedback, oblivious that it has passed through and has been altered by proxy.
Use Cases of Transparent Proxies and Why Firms Opt For its Use
Now that we are well acquainted with the concept of transparent proxies, highlighting the processes of how it functions, it is time to explore some of its use cases. Without delay, let us get right on to it.
-
Caching
Transparent proxies are useful to store frequently accessed contents as they always review this storage anytime a client requests to confirm if the requests can be sorted by them instead of being transmitted to the target site.
What this implies is that whenever a user requests data from a specific online site, the proxy will save it in its storage. In a case where the user or another user or any other user requests for that exact content, the proxy close to the user’s geo-location will transmit the stored content. This helps to curb delays in response.
-
Authentification
This variant of proxy is pretty handy for client authentication. Firms with open browsing networks usually apply this to inform clients of their set terms and conditions and validate guests through registration. A transparent proxy can also be useful to supervise traffic and restrict contacts that do not adhere to set network rules.
-
Load Adjusting
Transparent proxies function well as load adjusters for online sites with intense traffic. A frequently accessed site server may distribute inbound traffic among diverse background servers. This helps to facilitate the performance of an online site.
-
Data Filtering and Management
This is often enforced by firms to supervise their staff’s online activity on the network. They adopt transparent proxies as a filtering measure to block entries from the internal network to unwelcome data on the internet to maintain reasonable network utilization.
The Pros and Cons of Using Transparent Proxies
Like every other type of proxy, transparent proxies have diverse advantages and disadvantages. Let’s take a look at some of them.
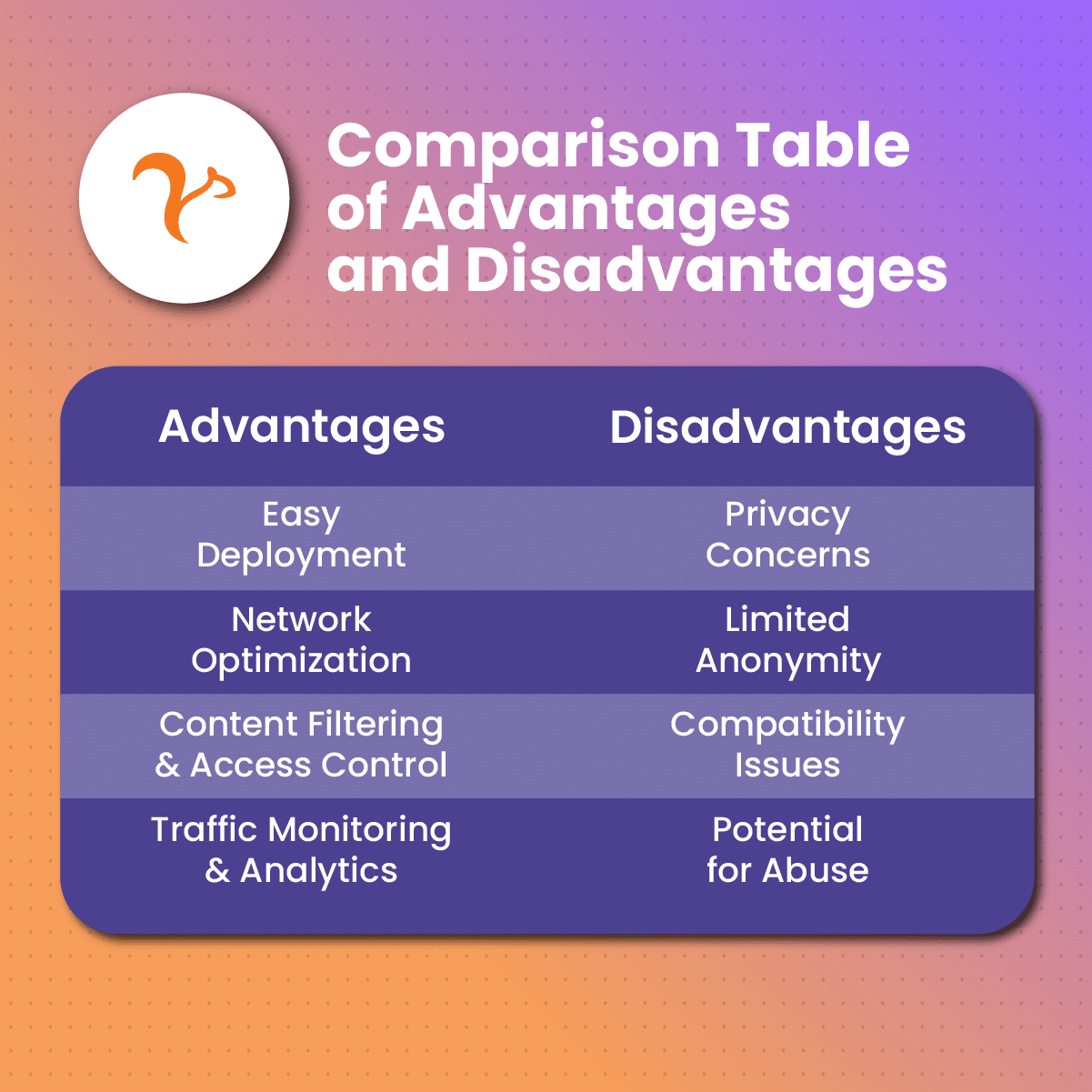
Pros
- It helps to improve surfing quality. Due to its ability to cache contents that are transmitted through it, transparent proxies can impressively help to improve internet surfing activities as it reduces the processing time for requests.
- Its setup is easy. An outstanding feature of the transparent proxy is that its setup for use is quite effortless. Since this proxy variant is network-based, it can forward diverse users without having to reconfigure its network. This makes them an excellent pick for internet accelerators.
- It effectively handles overloading. Compared to many other types of proxies, transparent proxies can handle network overload better. How do they achieve this? They possess an interception feature that allows them to monitor the performance ability of proxies and to correct faults swiftly.
- Their mediator function helps to improve security. Transparent proxies can help to enhance how secure a network is as they act as the middleman between users and the online web. This way, they can execute security guidelines such as filtering harmful or improper data, and can also offer an extra layer to secure the network against the likes of phishing invasion and viruses.
Cons
- Limited user control. Transparent proxies function without the user’s knowledge or setup, making it tough for users to supervise and manage the network traffic. This limitation in control is seen as a demerit for power clients or those with certain network conditions.
- Difficulty and compatibility. Enforcing transparent proxies is not an easy task. Also, the proxy variant may battle being compatible with specific apps that are not configured to function well with their likes, causing the need for more fixes and settings modification.
- Transparent proxies possess a sole point of failure. What this implies is that anytime the proxy encounters a downtime or crash, it can affect or restrict network traffic. Certain steps like introducing a backup proxy may be the way to salvage this setback.
- Privacy worries. Transparent proxies act to intercept and review requests and feedback of network traffic. Of course, this helps it to filter the content in the case where some of them are unwanted and to store it for easier access, subsequently. On the other hand, its ability to intercept can pose a great threat to privacy as client’s information and contact can be watched or recorded without permission.
- Performance concerns. While the transparent proxy is packed with a lot of benefits to enhance the speed of a network, it can also cause latency and delay in response time. This is because the proxy is required to review every transmitted request and that can cause a delay in general contact.
Transparent Proxies vs Non-Transparent Proxies: A Direct Comparison
Transparent proxies and explicit proxies, also tagged as non-transparent proxies, are two distinct categories of proxies with obvious differences. Let us take a look:
- Transparent proxies block network traffic with no need for any form of configuration on the user’s end. Contrastingly, explicit proxies demand that users configure the settings to transmit network traffic through the proxy. Users are required to modify the network settings or utilize a certain proxy setting application to use the proxy.
- Users are usually oblivious of the existence of a transparent proxy intercepting their request and they continue with their interaction with their target online server as though there is no proxy. On the other hand, explicit proxies are configured by users, implying that they are aware of the existence of a proxy acting as a link between them and online website servers.
- Since transparent proxies do not require any form of user interference, there may be privacy and control challenges. This is because the user’s information and contact may not get the supervision it need and this is likely to pave the way for information to be stored without permission. This is not so for explicit or non-transparent proxies. In this case, the users have more control as they are single-handedly required to set up the proxy to function with their device, so they have control over how traffic is transmitted through the proxy server.
- Transparent proxies are easy to integrate into broader networks as they do not need user setup. They can function at the network level to supervise and keep track of network traffic. Explicit proxies, on the other hand, provide a more flexible choice when it comes to user customization and setup. Users are at liberty to pick the specific apps or traffic that should be transmitted through the proxy server.
- Explicit proxies typically support a vast range of applications and software as they function with users’ ability to configure and modify their settings. This is not the same for transparent proxies that are prone to not being adaptable to specific applications that do not support intercepting proxies.
How to Discover Transparent Proxies and Avoid It?
If you are attempting to discover the use of a transparent proxy, then you may not want to ignore some of the enlisted information: Specific proxies may be instantly detected due to their configuration and some others may prove to be more complicated.
One of the easiest ways to discover the use of transparent proxies is to opt for a proxy detection website. All you have to do is tap on the search icon on your browser and find them. You can apply this to review an HTTP title received from an online site as well.
Also, an obvious signal that may indicate that your request is being transmitted past a transparent proxy is when the traffic is first forwarded to a distinct website before getting transmitted to your target site. Let’s illustrate this: if you attempt to gain entry into a website while connected to a free Wi-Fi and you are initially required to fill out login credentials, then you are most likely communicating with a transparent proxy.
To avoid this proxy, you may likely utilize a distinct network. For instance, if you attempt to gain entry to a website for a certain research objective utilizing your firm’s browsing WIFI, the network may restrict you due to the presence of a transparent proxy. However, you can find your way around it by opting for a different network to gain entry into your target website.
You must keep in mind that using a proxy detection tool or checking out for signs to indicate the use of a transparent proxy may not be accurate. These methods may signal the absence of a transparent proxy when, in fact, there is.
Factors to Look Out for Before Enforcing Transparent Proxies
There are diverse factors to tick out of your checklist before opting for the use of a transparent proxy. Let us review some of them.
- Understanding your network build-up. A transparent proxy is usually enforced at the network level so you must confirm that your network settings will permit the block and rerouting of traffic past a proxy server.
- Functionality factor. You may want to evaluate the likely effect a transparent proxy might have on your network speed while handling traffic. Although the proxy aids overall functionality by caching data and optimizing them, it can also cause intermission or lag in performance.
- Scalability factor. You must review the adaptability of the proxy. Assess elements like the number of coexisting clients, anticipated network rate and subsequent growth condition. Confirm that the transparent proxy server can deal with a certain level of overload and also enforce proper steps to avert a single point of failure.
- Safety and privacy factors. Transparent proxies act as alink to block and scrutinize traffic, which guarantees a certain level of security. However, you may want to assess the safety qualities contained in the proxy solution like data filtering and virus detection. Also, evaluate the effect the proxy’s interception/blocking can have on data privacy and confirm compliance with appropriate privacy rulings.
- Compatibility factor. You may also want to consider its compatibility nature as transparent proxies do not usually support a vast range of applications and software as compared to explicit or non-transparent proxies. This is because, unlike explicit proxies, they do not require any custom configurations done by the client. This implies that they are to be implemented as they come. Therefore, assessing its portability with the exact tasks to be used for is necessary.
Conclusion
There you have it, a guide filled with the necessary information you need to know about transparent proxies. Proxies remain an excellent solution to maintaining internet privacy and curb insecurity challenges significantly and the transparent proxy contributes its quota as it functions to intercept requests and handle all of the challenges that could arise from direct transmission of this data like filtering unwanted content such as viruses, among others. It is also a great pick for companies to monitor and supervise the data that passes through their network daily.
While this variant of proxy can be utilized beneficially, it is already worth noting that there are outlined downsides to its adoption. Knowing these downsides will help you weigh your options and decide if a transparent proxy is the perfect proxy that suits your needs. Also, such awareness would allow you to set up measures to minimize the possibilities of any negative impact that may arise from utilizing it.
Frequently Asked Questions and Answers
Is using a transparent proxy a safe option?
Transparent proxies are relatively safe to use so long as it has not been penetrated by internet invaders to risk the data that is transmitted through them. In the absence of such a challenge, you may need to weigh all of the proxy options to ascertain if this proxy is exactly what you need.
Are transparent proxies easy to use?
Yes, this proxy variant is comparably easy to integrate for use. Unlike non-transparent proxies that may require some settings configurations and adjustments, this proxy does not require any form of manual configuration by the client to begin its action of intercepting your network to assess, filter and cache contents. While this appears to be an app laudable feature, it also comes with its downsides as proxies that require client modification may be more compatible with other applications.
Can transparent proxies be utilized for malicious activities?
Like every other technological innovation, transparent proxies can be used for some forms of internet invasion. Intruders can offer transparent proxies to get access to data. How does this work? Transparent proxies intercept the network to review contents that are transmitted through it. A transparent proxy intended for malicious activities can be used to record some of these data without approval. This is why it is recommended to always opt for proxies that are made available by reputable sources as not every website is set up to offer solutions without ulterior motives.