Every internet user has used an HTTP proxy so long they’ve searched for a website on their web browser. With an HTTP proxy, your web browser can send and receive data from the client-side server, allowing you to access the requested information.
If all of these sound too confusing, don’t worry because we will explain how HTTP proxies work, the different types of HTTP proxies that exist, as well as the overall benefits of HTTP proxy.
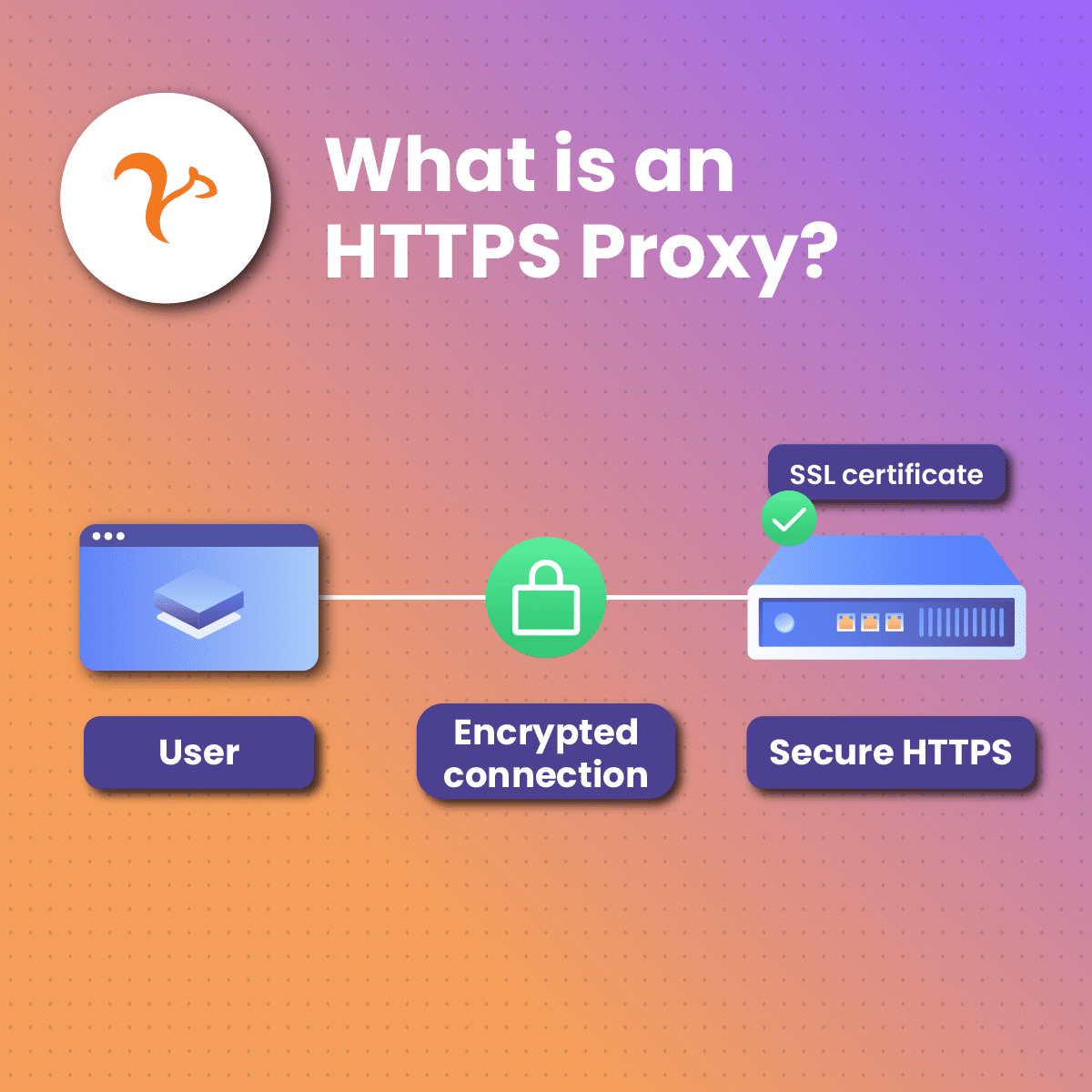
What is HTTP Proxy?
An HTTP Proxy acts as a gateway between you and the internet. It’s a server that separates end users from the websites they browse. By handling your requests, it ensures anonymity, facilitates security measures, and even accelerates access to resources by caching. Proxies are versatile tools for both individuals and organizations, aiming to enhance online privacy, bypass geo-restrictions, and optimize internet performance.
Brief History Of HTTP Proxy
The history of HTTP proxy is chaotic because there was no defined timeline for when it started. However, the earliest history of HTTP proxies dates back to the 1970s when BOLT, Beranek, and Newman built the first internet network.
The network served as the intermediary between external and local area networks, offering several functionalities. The earliest HTTP Proxies could accept and forward commands to bar, control, and sanction communications within the client app and the external networks.
Over time, the network was developed into the Network Address Translation (NAT). NAT translates private IP addresses into public IP addresses before transferring the information onto the internet. With NAT, some form of security protects the communication between external and internal network borders.
Another great advantage of NAT was that it simplified network administration, making it easier to manage a network with multiple devices.
But as technology improved, HTTP Proxy has evolved from only protecting network communications to content authentication and caching abilities, making for smoother and sometimes restricted communication between networks.
We have given you a brief history of HTTP Proxy, but it still doesn’t explain what this ‘intermediary’ actually does.
What is a Proxy?
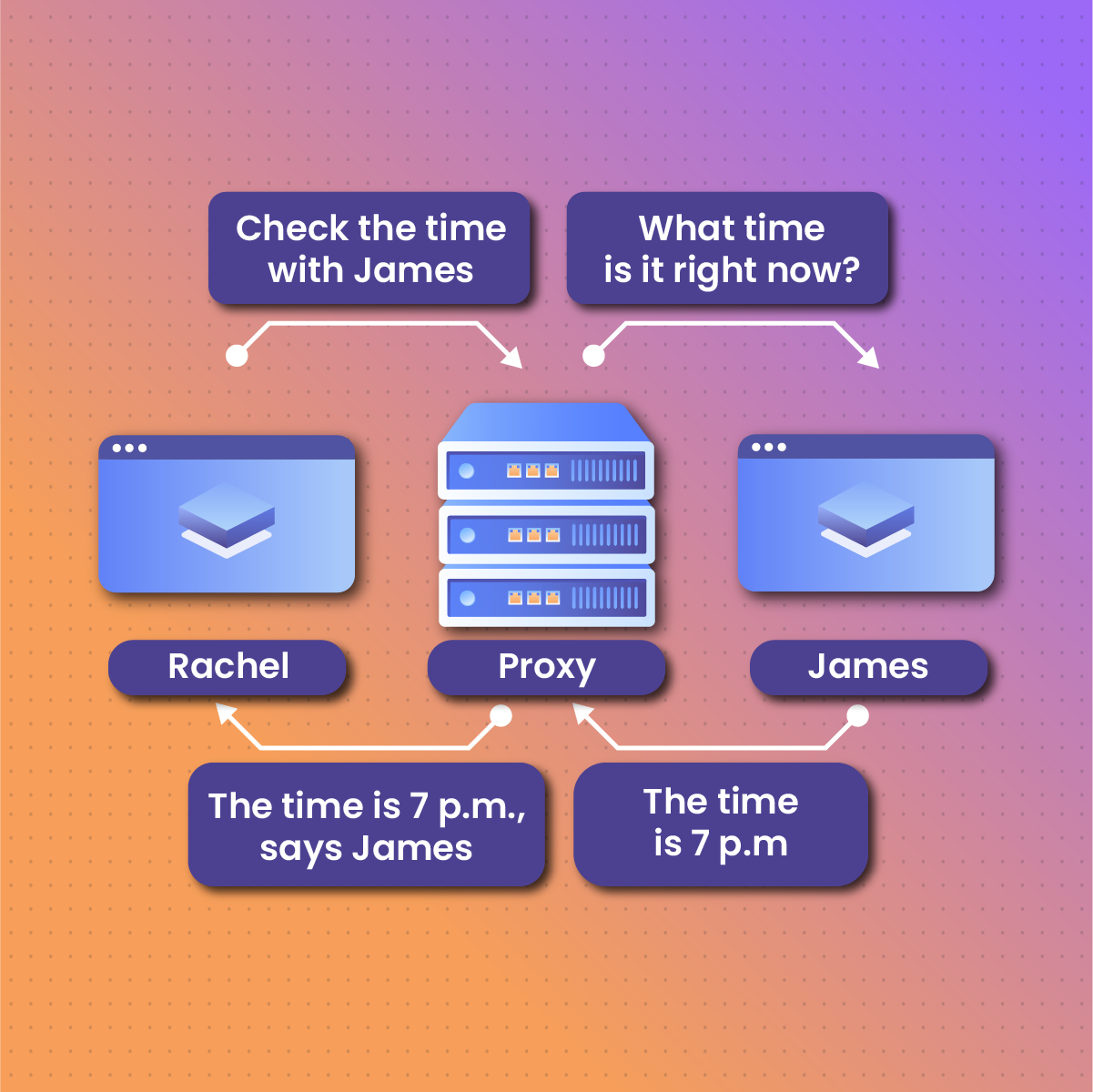
Proxies are like representatives of people or things. They are not the real person or thing, but they can stand in for the real person. HTTP proxies are like that: servers acting as middlemen between your device (phone or computer) and the website you’re visiting.
When you type an address into your phone browser, the browser sends a request to the HTTP proxy.
The proxy then sends the request to the website’s server. After the website’s server receives the request and has gotten the document the proxy demands, it sends it back to the HTTP proxy. The proxy then gives you the information you requested, in this case, the website’s content, back to you.
The workings of the HTTP proxy are important in internet connections because it allows your device to request information from another server and then process the delivered information from the server.
But the next question you’re probably asking is, what’s the use of an HTTP proxy? Isn’t it possible to access a website’s server without a proxy?
Yes, it is possible to access websites without an HTTP proxy, but there are so many advantages of using a proxy network that it’s dangerous for your safety if you don’t.
An HTTP Proxy is like a middleman, but in this case, we’ll call it a content filter that sits between an HTTP client and a server, helping with requesting and responding to queries from the user.
Advantages Of Using HTTP Proxy
Being on the internet can be very risky, given the high level of cyber-attacks online. Therefore, using a secure HTTP proxy is a sure way to ensure you enjoy your online experience. And in the case of companies, their data are protected from malware and cyber-attacks when they use HTTP Proxies.
There are some awesome advantages of using an HTTP Proxy, whether as an individual or an organization.
Provides you with Anonymity:
Your IP address is masked when using proxies, providing anonymity online. For example, some websites don’t allow users from certain regions to get access. With an elite HTTP proxy, your IP address is covered, making it difficult for the website server to detect the geolocation of your IP address.
Content filtering and access control:
Businesses that have designed their network use HTTP proxy to prevent some types of content from gaining access to their server. Malicious and unwholesome content is filtered away. Content filtering helps companies protect their server and ensure employees use the network for only work purposes. And for parents, it helps protect their children from accessing unwholesome websites.
Caching and Bandwidth Saving:
When you visit a website, there are ‘crumbs’ of that website that stay on your device. These ‘crumbs’ are called caches.
With caches saved, you can access the website again, saving you bandwidth and increasing the website loading time.
Bypassing geographical restrictions:
Some websites have geo-restrictions, preventing people from certain places from accessing the website’s server. But with an HTTP proxy, you can bypass those restrictions.
Load Balancing:
HTTP proxies can share the load with different servers, increasing a website’s loading speed. Load balancing prevents individual servers from getting overloaded with requests.
Security enhancement:
HTTP proxies are a buffer between the client (your browser) and the internet. It protects your browser from accepting malicious threats, protecting you from cyber threats and attacks.
Different Types Of HTTP Proxy
The different types of HTTP proxies are classified based on how they protect IP addresses and the functions they carry between the client and the web server.
Forward Proxy:
The forward proxy is in front of the client, taking in the request from the client side. For example, when you type a web address on your browser, the browser sends it to an HTTP proxy. This proxy that receives the request is called the forward proxy. The proxy then decides whether the request from the browser is safe and good.
However, this proxy type doesn’t cater to many end users because there’s only one entry point. Organizations use Forward proxies to cache or filter web traffic. And it allows for straightforward administrative control.
Reverse proxy:
While the forward proxy sits in front of the client, the reverse proxy sits on the server side. It receives requests from the client and sends them to the appropriate servers. Reverse servers are used to simplify access to the server side and for load balancing. When the proxy receives the information from the server it had sent the request to, it sends it to the client.
Reverse servers improve websites’ security, making them the top choice for organizations.
Open Proxy:
Open Proxy is among the most popular HTTP proxies for everyday internet users. If you’ve ever wanted to bypass a geo-restrictive website, you must have used open proxies.
They’re accessible to every internet user without restrictions to a specific network or user.
With open proxies, authentication is unnecessary even though it works like the forward proxy we discussed earlier. When a user connects to an open proxy and then tries to access geo-restricted websites, the server sees the request as coming from the proxy’s location, not the client’s.
Transparent Proxy:
Your IP address isn’t hidden when using transparent proxies. With transparent proxies, the people on whom the proxy was enforced won’t know they’re using a proxy. Companies use it to cache website traffic.
The major disadvantage of Transparent Proxy is its high vulnerability to security threats such as SYN flood denial of service attacks.
Elite or High Anonymity proxy:
These proxies mask the client’s IP address and don’t show the server that the IP address is from a Proxy.
Unlike transparent Proxies, which show that the IP address is from a proxy, elite proxies make the IP address look like it is from a regular server.
How HTTP Proxy Handles Client Requests and Server Responses
Request Handling
The proxy receiving requests from the client, sending them to the server, and the server responding to the request is integral in understanding how HTTP proxy works.
The client request process goes through the following:
Request Initiation:
The client sends an HTTP request to the proxy server. That request contains the URL you want to visit, such as Forbes.
Proxy Validation:
The proxy then receives the request and validates whether the request is valid, i.e., authorized or restricted.
Request Routing:
If the request is authorized, the proxy would determine whether to send it to a different server that’ll handle the request or it’ll handle it directly. When handling it directly, the proxy server fetches the cache files it had saved (if it has the cache files) and responds to the request.
Forwarding Request:
If the proxy doesn’t have the cached file, it sends the request to the web server. But before it does that, it changes the client’s IP address. Afterward, it sends the request to the destination server.
Response Handling
After the client has sent the request, the destination server would have to respond to the request.
Response Generation:
The destination server generates the response message after receiving the request; this includes the response headers, content, and requested status code.
Interception by Proxy:
The proxy server intercepts the request and analyses the request codes, headers, and content
Response modification:
Now, the Proxy searches to know if it already has the cached file of the request. If it has, it updates it. Then, it modifies the response headers before sending it back to the request proxy, which then sends it to the client.
Use cases of HTTP Proxy
HTTP proxies are used in different industries for different reasons. HTTP proxy is essential for different reasons, from enhancing security and privacy to improving performance.
In the Corporate Environment:
Used for security reasons:
Organizations that have data they want to protect use HTTP proxy as a barrier between their Internal users and the internet.
Companies understand that cyber attacks are becoming rampant, and their server can be breached without proper cyber security. HTTP proxy is needed to filter against malicious content, malware, and viruses.
Content Filtering:
Some companies have policies restricting the type of content employees can access from the workplace. Content filtering through HTTP Proxy allows the company to monitor the website traffic of its employees.
Content Delivery Networks (CDNs)
CDNs work best when efficient. CDNs’ efficiency requires delivering content to the end user as fast as possible. To do this, HTTP proxy caches content, thereby speeding the delivery process to the end user.
Web Scraping
Web scraping crawls the web to retrieve specific website data. The “masking” properties of proxies make it easy for scrapers to go through websites without revealing the client’s IP address. Some websites might restrict access to their data if they know the client’s IP address. But with proxies, such issues are surpassed.
Also, when e-commerce companies want to monitor the prices of their competitors, they use proxies in their web scraping, making it difficult for the competition to know where the IP address emanates from.
Digital Marketing:
Content marketers use HTTP Proxy to check the ranking of keywords on search engines and perform keyword research without facing IP blocking or rate limitations.
Things To Consider When Choosing HTTP Proxy
In selecting an HTTP Proxy to use, you must consider several factors. These factors are not cast in stone but will help you decide which HTTP proxy to buy.
Purpose:
When getting an HTTP proxy, your reason for getting the proxy will determine what you’ll get. For example, if an organization wants to filter the type of content its employees can access, it would not get an elite HTTP proxy. In the same way, a random internet user who just wants to access some content that has been geo-restricted won’t be looking for reverse Proxies. The purpose of needing a proxy determines which proxy types you’ll get. Level of anonymity:
The level of anonymity you want would play a big role in the type of HTTP proxy you get.
If whatever you do with a proxy requires great privacy, you’re better off going for elite proxies. But you can use transparent proxies if you don’t need too much privacy.
Speed and uptime:
One of the advantages of proxies is that they increase the load time of a website. When getting a proxy, search for the ones with great speed and a high uptime rate, so your internet connection isn’t slowed down because you’re using the proxy.
Security features:
A company that wants to protect important data knows better than using public proxies. So also individuals who work on highly sensitive materials. When using a proxy, be certain of the security level you want so your device isn’t attacked and your data infiltrated.
Logging Policies:
Check for proxies that permit only minimal logs. Proxies with minimal logs are best for protecting your privacy as a user.
Budget consideration:
Budget consideration is critical in selecting proxies because it’ll affect the quality of privacy, security, and service you’ll get. It is also important to consider the cost because sometimes what you want costs more than you can pay for. If there are subscription-based proxies that’ll meet your defined needs, then go for them because they are often more affordable.
Management tools:
People often forget that management tools are integral when fixing issues, such as rebooting, troubleshooting, configuration, etc. Look for an HTTP proxy with great management tools so that these issues can be handled when they arise.
Reputation and Reviews:
You know you’re handing over some control when getting an HTTP proxy. So, before you make that decision, ensure you have done due diligence to see what other users say about the provider and whether they live up to their promises.
Testing Period:
Some HTTP proxies give you a free testing period. Use such ones to know the quality of the service and whether it satisfies the tasks you’re getting it for.
How To Configure HTTP Proxy On Different Devices
Following these processes, you can set up your HTTP proxy on different devices.
On Google Chrome
- Go to your browser and click the three dots in the upper left menu.
- Then go to settings.
- In Settings, scroll down to Advanced. Click on the advanced settings, and it’ll reveal some options.
- Among the options, you’ll see a systems section. Click on it. Then click on “Open Your computer’s proxy settings.”
- You’ll see a tab called “Internet Properties.” Click on it, and you’ll have the option to click on “LAN Settings.”
- Enter the proxy server address you want to use before clicking OK.
On Microsoft Edge
- Click on the three dots at the top left-hand corner of your Edge browser
- Select settings and click “Privacy & Security.”
- After you’ve clicked that, scroll down to the “Proxy Settings” section
- Click on Open Proxy Settings
- You’ll see a “Manual Proxy Setup” tab. Enable the use of a proxy server option.
- When enabled, you’ll be asked for the proxy server’s address and port number for SOCKS.
- After you’ve added the number, click on Save.
Privacy and Data Bridge Concerns with HTTP Proxy
The advantages of proxies should be considered. From privacy to security and speed, HTTP proxy is integral in today’s internet age. However, despite its many advantages, some ethical issues are raised about its usage.
Data Collection and Privacy Concerns:
Over the last few years, ethical debates have been raised on people’s data collection and use. Proxies allow for data scraping and eventual usage without knowing the users’ and website administrators’ knowledge. However, some people argue that online users are responsible for their privacy.
Some of the unethical ways data scraping, enabled by HTTP Proxy, are being used include:
- Digital marketers who use proxies for targeted ads have also come under serious fire because of the intrusive nature of these ads.
- In masking IP addresses, fraudulent users can use it to hack into private accounts and even defraud financial institutions and private individuals.
- Some HTTP proxies, although they promise tight security, are compromised, leading to data leakages, which may cause a load of damage to organizations, people, or even projects.
How to Troubleshoot HTTP Proxy Issues
You might have trouble using your HTTP proxy. When you run into an issue, here is how to troubleshoot your proxy:
Check if your internet connection is stable.
A stable internet connection is paramount when using proxies. The client and the web server can communicate on the back of the internet’s strength. Therefore, the internet’s strength determines whether the proxy would receive and transfer requests and responses from the client and server.
Check your antivirus.
Antivirus can be good or bad, depending on its use and settings. Some third-party antivirus can interfere with your browser, making it hard for the proxy to connect. Check if the antivirus setting is preventing you from connecting to your proxy.
Check the setting in your proxy.
There’s the possibility that you’ve not configured a proxy in your web browser setting. As we explained earlier, confirm if you followed the process. If you did all of that, then do something else.
Clear your cache.
Clearing cache and cookies helps you start all over again, cleaning every ‘residue’ of former websites visited.
Try a different proxy.
Try something else if the methods still don’t get your proxy working.
How Artificial Intelligence and Machine Learning Are Revolutionising HTTP Proxy
As Artificial Intelligence and Machine Learning continue to evolve and change how we see and interact with technology, their effect on HTTP Proxies is also revolutionary.
Some ways AI and ML positively affect HTTP Proxy are
Smarter Proxies coaching
Machine learning can better understand and analyse the web traffic pattern a proxy gets and predict future patterns, thus decreasing the load time, decreasing bandwidth, and increasing content delivery speed.
Dynamic Proxy Management
Although HTTP Proxy manages proxy usage well, spreading it across, with AI, the rotation process becomes faster, personalized to people’s location, website access requirements, and potential geoblocking rotations. With AI, proxy management will be more effective, and users can enjoy faster content delivery.
More personalised
With a great predictive model that continues to learn how to optimize itself, proxies will start fitting people’s needs even before they verbalize it. With AI, HTTP proxy will be better optimized to give users wholesome experiences.
As lofty as these advantages are, one can’t pretend that proxies, like earlier mentioned, can be a huge security threat if ethical measures aren’t taken.
HTTP Proxy Frequently Asked Questions
Is HTTP Proxy compulsory?
No. Having an HTTP Proxy is not compulsory, but it is important because it helps you with privacy, bypasses censorship, and improves your web browsing speed. HTTP proxies are typically highly recommended for users who prioritize privacy and security online. It serves as a shield, masking your IP address and providing an extra layer of encryption, thus making your internet activities less transparent to external observers.
What are some of the common issues with HTTP Proxy?
Some of the common issues you’ll encounter with HTTPS Proxies include:
- Slow speed
- Data leakages
- Privacy concerns
- Some proxies might not work on all websites
What is the best HTTP Proxy?
There is a ‘best’ HTTP Proxy; it depends on what you want and how much you will pay. Factors to consider include reliability, speed, security features, and the ability to bypass geo-restrictions. Researching and comparing services based on these criteria will guide you to the most suitable option.
Should I have HTTP proxy on or off?
Deciding whether to have your HTTP proxy on or off hinges on your online goals. If enhancing privacy, accessing geo-restricted content, or securing your data is a priority, turning it on is beneficial. However, if speed is a concern and security is not as critical, you might opt to keep it off.
What is my HTTP proxy address?
Your HTTP proxy address is a unique identifier assigned by your proxy service provider. It consists of a server address and a port number, both of which are necessary to configure your device’s network settings to connect to the proxy server.
Can I Use HTTP Proxy on iPhones?
To utilize an HTTP Proxy on an iPhone, you’ll need to manually configure it through the Wi-Fi settings. This involves selecting your connected Wi-Fi network, navigating to its settings, and entering the proxy address and port provided by your proxy service in the HTTP Proxy section.
HTTP Proxy: Final Thoughts
Protecting your activities online and increasing content delivery speed are two of the most important advantages of HTTP Proxies. As the world continues to evolve and emerging technologies like AI and ML change how we interact, HTTP Proxies will continue to grow, and the services will improve. The myriad ethical issues using HTTP Proxies have not in any way removed from its usefulness in today’s cyber-dangerous world. HTTP Proxies will continue to be integral in the technological age. Hopefully, AI and ML will make it more affordable for the regular user.