Forward Proxy vs Reverse Proxy: Exploring their Differences
Proxies act as singular points of access and control when surfing the internet. They are reference points when transmitting data online from users to servers and vice versa. Usually, it is not uncommon for firms to employ different types of proxies to efficiently direct traffic between networks. Yet, there still remains a large uncertainty on how this activity differs for each kind of proxy. This has resulted in many questions and mixups, especially pertaining to forward proxies and reverse proxies.
It is important to clarify that although these two kinds of proxies act primarily as mediators in facilitating data interactions between users and servers, they do so in distinct ways, each playing different roles in the routing process. Understanding the disparities in how these proxies function is crucial to building improved and secure website-based systems.
In this article, we will explore in detail the meaning of forward and reverse proxies, including how they are used. We will also outline their similarities and key differences, alongside if they need to work together. Finally we will answer some frequently asked questions on forward and reverse proxies.
What is a Forward Proxy?
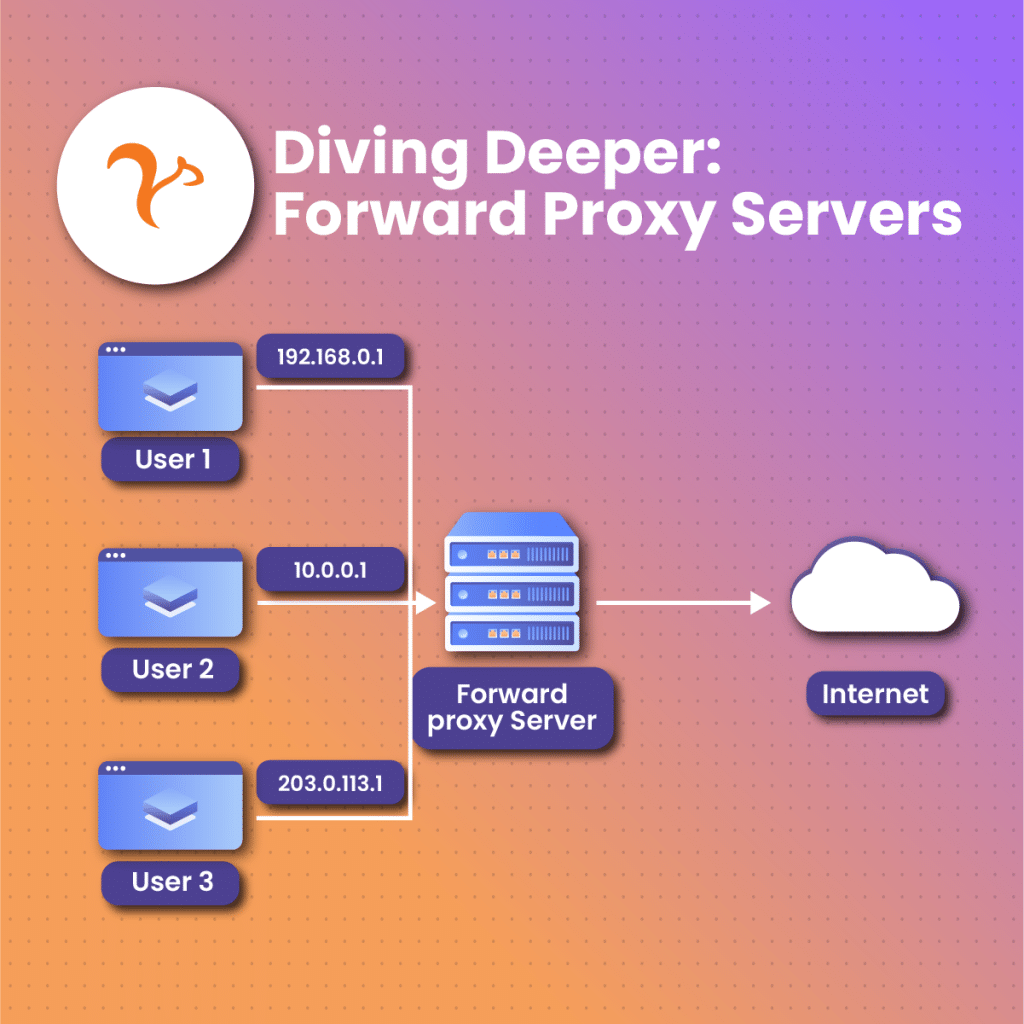
Forward proxies are types of proxies that render a “middleman” assistance to users that are often part of an internal network. As soon as a user establishes a contact activity to a data transmission server in the online space, its request is first made to be transmitted to a forward proxy. Usually working together in hand with firewalls, the request flows across the firewall right into an information transmission server.
The information transmission server then identifies the forward proxy server as the originating source of the sent-in request, without knowledge of a user behind it and gives feedback to the forward proxy.
The forward proxy which like other proxies is able to keep track of requests, responses, including their sources and destinations, then receives this feedback, recognizing that it is a request from a user, and transmits the response to the exact user. This helps them handle tons of user requests across different servers, mediating between them all.
Forward proxies are useful in activities like:
- Maintaining a user’s anonymity and privacy. Generally, they help to conceal your original identity from whatever source you intend to interact with. They are able to achieve this by keeping your IP address hidden while transmitting your requests with a substitute IP address which is then interpreted by the online site as your IP identity. This enables users to gain access to geo-restricted music applications, contents, or even movies.
- Caching data for later access. Forward proxies also aid in caching online content that has been detected, making them easy to be accessed. This drastically cuts down lags needed to search for the content.
- Requests, feedback transmission and translation. Forward proxies are the central unit to which users interact with when sending in requests. Users also depend on them to relay online feedback given to those requests.
- Create access to restricted online content and regions. Forward proxies allow users to boycott geographical location restrictions set up by certain sites on specific content. It does so by concealing the user’s original IP and presenting its attached IP which is tagged to be authorized for access.
- Data scraping. This is one of the most popular tasks that proxies are utilized for. The idea of data scraping is simply to compile as much necessary information from different areas of the web. Such information could be used in assisting with market competition analysis, or even information relating to how well a user’s online marketing campaign is performing.
What is a Reverse Proxy?
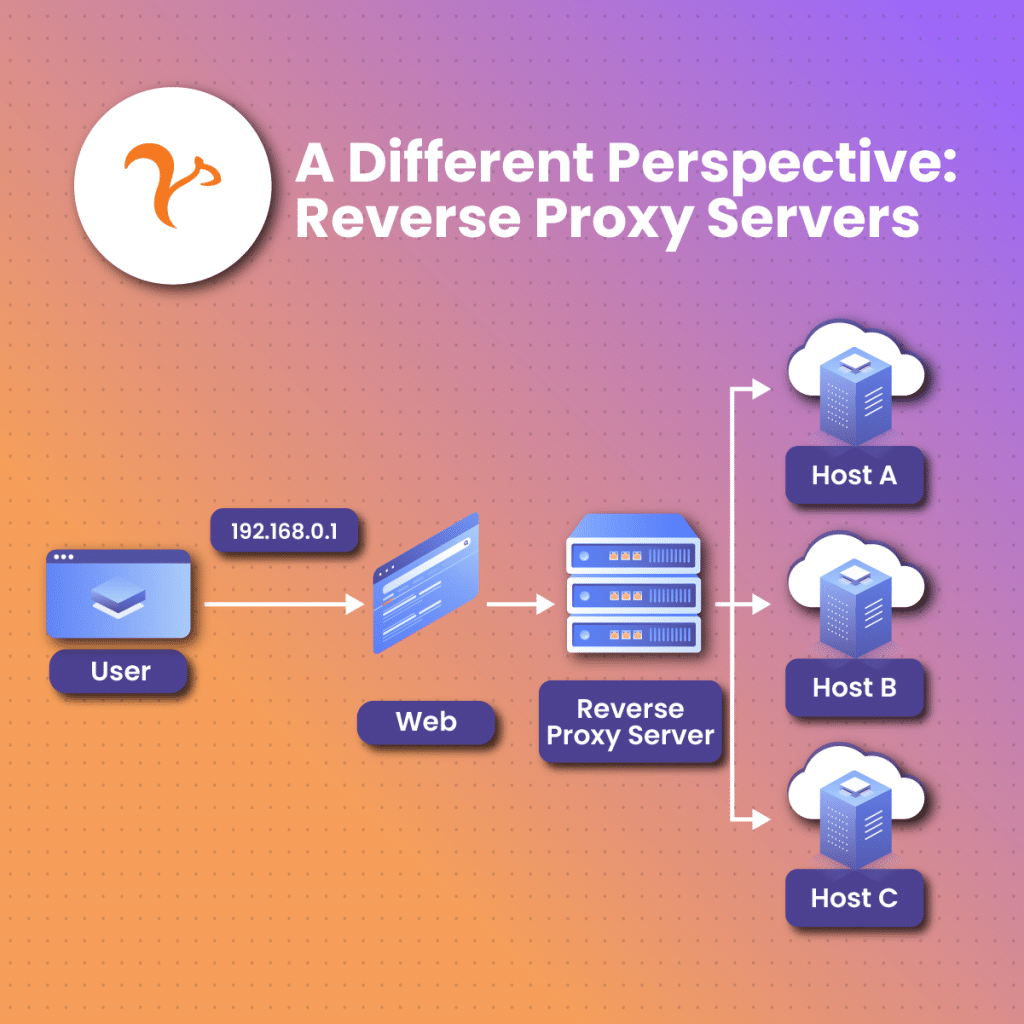
A reverse proxy functions majorly in a contrasting way to the forward proxy. While the forward proxy is stationed to perform its services in the interest of users, the reverse proxy acts at the forefront of a single or multiple internet server. Reverse proxies allow requests to pass through it into internet servers and also get a first-hand hold of feedback that is relayed from these public internet servers. Simply put, a reverse proxy works directly with servers of targeted websites in which a request is sent and feedback is expected.
Reverse proxies offer the uptight services of an information transmission server, and as such, online site intruders encounter more challenges attempting to obtain information in such a server than they would with another proxy.
Reverse proxies function efficiently for a variety of online activities as well. They can act to help maintain anonymity for the servers with which it has direct contact, just as the forward proxy helps to mask user’s identities and keep them anonymous. Reverse proxies also perform the activities of sending and receiving requests to web servers before transmitting feedback from these servers to where the requests originated from.
Similarly, reverse proxies are helpful when it comes to load-sharing or balancing activity. Load sharers are necessary in ensuring increased availability to online servers that record large numbers of requests. When reverse proxies carry out their load-sharing task, they evenly dispatch service requests that come in different groups of available network servers offering the exact same type of service.
It is important to note that both variants of proxies offer an exclusive path of entry and supervision. All that is required is for you to set up and attach firewalls to keep traffic in check, and support the request transmission process.
Similarities Between the Forward Proxy and the Reverse Proxies
Regardless of how the forward and reverse proxies may seem like two different kinds of proxies, both functioning in different areas for different servers. And however distinct they look, they have a fair share of similarities which we will discuss in this section.
- A major similarity that exists between these two proxies is the fact that they both function as a shield measure in safeguarding devices that interact with private networks from dangers in the online space. Also, they both can perform an anonymity feature, concealing their IPs and creating a complication to ensure that no one can travel their server’s geographical region or identity.
- Reverse proxies, also like forward proxies, are able to place restrictions on the category and size of data that is transmitted across them to any destination. This enables them to either allow requests from devices that are verified or deny requests from sources that are not authorized.
- Both proxies have a set-up that enables them to perform network switching activities. Simply means that both proxies are involved in data channeling from one port to another until the data gets to where it is requested.
- Both proxies are compatible with popular internet transfer protocols like the file transfer protocol (FTP), transmission control protocol (TCP) and even the hypertext transfer protocol (HTTP). Making it easy for their operators to get through to numerous services using their servers.
- Caching. A process whereby both the forward proxy and reverse proxy can effectively detect frequently accessed sites and content, keeping them closer to make the next search relatively easier.
Differences between Forward proxy and Reverse proxy
While both proxies may share some similarities, reality maintains that they are distinct and operate distinctively. Some differentiating factors between them include:
- Reverse proxies mostly act as helping hands in transmitting requests to and from different servers while forward proxies are usually used for scouting the internet for necessary resources.
- Forward proxies are generally set up manually on a device, usually a computer in the firm, to ensure that staff gain secure entry while accessing the internet whether remotely or otherwise. Furthermore, each device that requires information or data that is not present in the firm’s segmented network must go through a setup that binds it to be represented by the firm’s forward proxy IP address.
On the other hand, reverse proxies do not require pre-setup users. Their servers are enabled in such a way that they allow for free entry.
- Reverse proxies take the win when it comes to content modification as they can modify and change content before it is transmitted to where it is requested for. However, forward proxies are not well equipped to manipulate headers or compress files in that same way. This is why reverse proxy is mainly employed in content rewriting.
- Reverse proxies offer just one point of access for users to be able to get through to tons of servers behind it while forward proxies are helpful for users to explore large content and information online. The distinction here is that each request placed on a forward proxy has to be routed or transmitted differently.
- When users employ forward proxies for their online access requests, the other servers they interact with are always ignorant of the existence of a proxy being an intermediary. This is not the case for reverse proxies as other servers recognize the presence of a reverse proxy.
- A reverse proxy can supervise server performance and functionality. Allowing it to spontaneously transmit request entries to servers that have been confirmed to be more functional. Forward proxies on the other hand are ill-equipped to carry out such performance supervision tasks.
- Forward proxies are limited to the volume of load they can handle as their function is more centered around how to cache content, as well as filtering them while maintaining an increased level of user anonymity. Reverse proxies on the other hand are able to handle significant numbers of requests as they simply help to route these requests across various servers.
- Reverse proxies are always at the forefront of launching interactions with servers as it has to transmit users’ requests across to them. With forward proxies, users are the ones to commence or launch such interactions to signal the proxy that a request to be transmitted has been made.
- Reverse proxies are often deployed in cases where various servers need to be reached with a sole access point. For example, in the area of load sharing and taking care of hypertext transfer protocol secure (HTTP) requests. Forward proxy helps supervise internet entry for users.
Do Forward Proxies and Reverse Proxies Need To Work Side by Side?
While both proxy variants tend to give an assistive function on both ends of the internet, they can operate independently and do not need to be used together. Regardless, there are instances where their different functions could be employed to get better results. A couple of such instances include;
To improve security. By merging both the forward proxy and the reverse proxy, you can achieve an enhanced double-edged security. The former can assist with its ability to effectively filter information while upholding its anonymity feature to protect the user end. And the latter, which is the reverse proxy, with its ability to terminate the secure socket layer (SSL) and shield against distributed denial of service (DDoS) invasions for inbound user requests. A merge of both functions will help ensure maximum protection of user requests flowing into the online space and inbound requests getting across reverse servers.
To ease complicated network setup. In an extensive system comprising a complicated network setup, it is a norm to see diverse layers of proxies being employed at different levels and for different functions. In such an instance, a forward proxy might be employed at the user’s end, while a reverse proxy fills in at the boundary where devices interface with the internet. A third proxy, probably another reverse proxy, might be employed to manage incoming load within the private network. Such a multi-layered technique will help to ensure maximum supervision and security without excluding how optimized performance would be at various levels.
Conclusion
In summary, while the features of proxies are a gateway to multiple possibilities, it is advised that they are all put to good use to guarantee maximum user experience rather than pave the way to more vulnerabilities. Each point comparing and contrasting between the forward and reverse proxy helps to reiterate the necessary level of asset each proxy provides to the internet.
From ensuring all the basic tasks, like user anonymity, to ransacking the internet for sufficient data, similarly referred to as data caching, both forward and reverse proxies assist in contributing to ensure that a variety of tasks are carried out with ease.
Frequently Asked Questions and Answers
What category of proxy does VPN fall in?
You could classify a VPN as a forward proxy. Although, in contrast to the usual forward proxy, VPN encodes information that is transmitted across. VPN may operate like a proxy variant, helping to conceal clients’ IP addresses but it supersedes proxies as it covers a large-scale aspect in its protection function. VPNs also apply to all websites and applications, and it even covers remote geographical locations that clients have access to. Proxy functions halt at the app level, effectively handling access requests of a program.
What proxy variant would be most helpful to operating a business?
The proxy you decide to opt for is largely dependent on the major challenge you want to solve. If your priority is on improved anonymity, then the usual proxy may just be your best bet. Otherwise, you may want to consider other options. It is however, recommended that you focus your attention on choosing the right kind of proxy for your business, and also prioritize obtaining it from the right source as well. This is the only guaranteed way to ensure that you enjoy all the benefits attached to that proxy while being certain of maximum user protection.
Can reverse or forward proxies be substituted for one another?
No. Forward proxies may have certain similar functions as the reverse functions but it does not make them synonymous to each other. They are two distinct proxies that are required at the two distinct points of the internet. While they cannot be substituted for each other, both proxies can complement each other, in some cases, by performing distinct functions that aim at a similar goal.






