Introduction
A cloud proxy is a cloud-based system that connects a client to a server, data center, or SaaS application. Many modern applications work with multiple distributed parts like serverless functions, databases, servers, message queues, and more. Therefore, it becomes necessary to have a standard way to access the components through a client. In other words, a cloud proxy is a system that handles communication between a client and server resources while providing secure access to a resource.
Do you want to know more about how a cloud proxy works, its benefits, and use cases? This article covers the basic areas of the concept.
Let us dive in!
What is Cloud Proxy?
The introduction of the intermediary provides a central point of communication between the client and the resources that exist in the backend. Subsequently, this ensures the client and server do not interact directly but through the cloud proxy.
Benefits of Cloud Proxy
Proxies provide several benefits to businesses and individuals looking to ensure optimal data security and privacy. Here are some benefits of using a cloud proxy:
Optimized scalability
Many organizations are favoring distributed work environments. Therefore, workers often operate from remote locations away from the traditional enterprise network. Subsequently, cloud-based proxies are designed to optimize scalability so that they accommodate the dynamic needs of users. As a result, users can access the required resources with consistent performance and reliability despite location.
Cloud proxy can leverage the global network and be available worldwide so that users can access their resources with a minimal round trip, which reduces latency. Therefore, a cloud proxy can easily scale up and down based on the demand, which seamlessly accommodates spikes in traffic without manual intervention and optimizes the proxy functions.
Enhanced user experience
Cloud proxy focuses on providing a smooth and optimized user experience. It ensures that the client does not experience any significant latency regardless of the decryption and encryption that takes place to ensure the security of the network. Therefore, this becomes crucial as users can perform their tasks effectively without unnecessary delays or interruptions.
Increased privacy and security
Another benefit of using cloud proxy is optimized security and privacy. Like other types of proxies, it provides an additional layer of security that ensures your network traffic is not exposed to others. Subsequently, this protects your business’s sensitive data from potential cyber theft.
Improved caching
A significant benefit of cloud caching is that it can cache content closer to the user. Subs equently, this reduces the loading time, which ultimately optimizes user satisfaction. In addition, it can use advanced routing techniques like geo-location, latency-based routing, or geo proximity to optimize the user experience.
Cost-effective
Hardware-based proxies often demand high upfront and maintenance costs. Therefore, a cloud-based proxy serves as a cost-effective alternative, especially for big organizations. Subsequently, it reduces the need to invest in hardware appliances, the cost of IT personnel, which allows for more efficient resource allocation. In addition, big businesses can reduce the cost of operations because they do not need to maintain cooling mechanisms, server rooms, or power backups.
Use Cases of Cloud Proxy
Cloud proxies can be applied in different cases as they play crucial roles in privacy and security. Here are some use cases of cloud proxy:
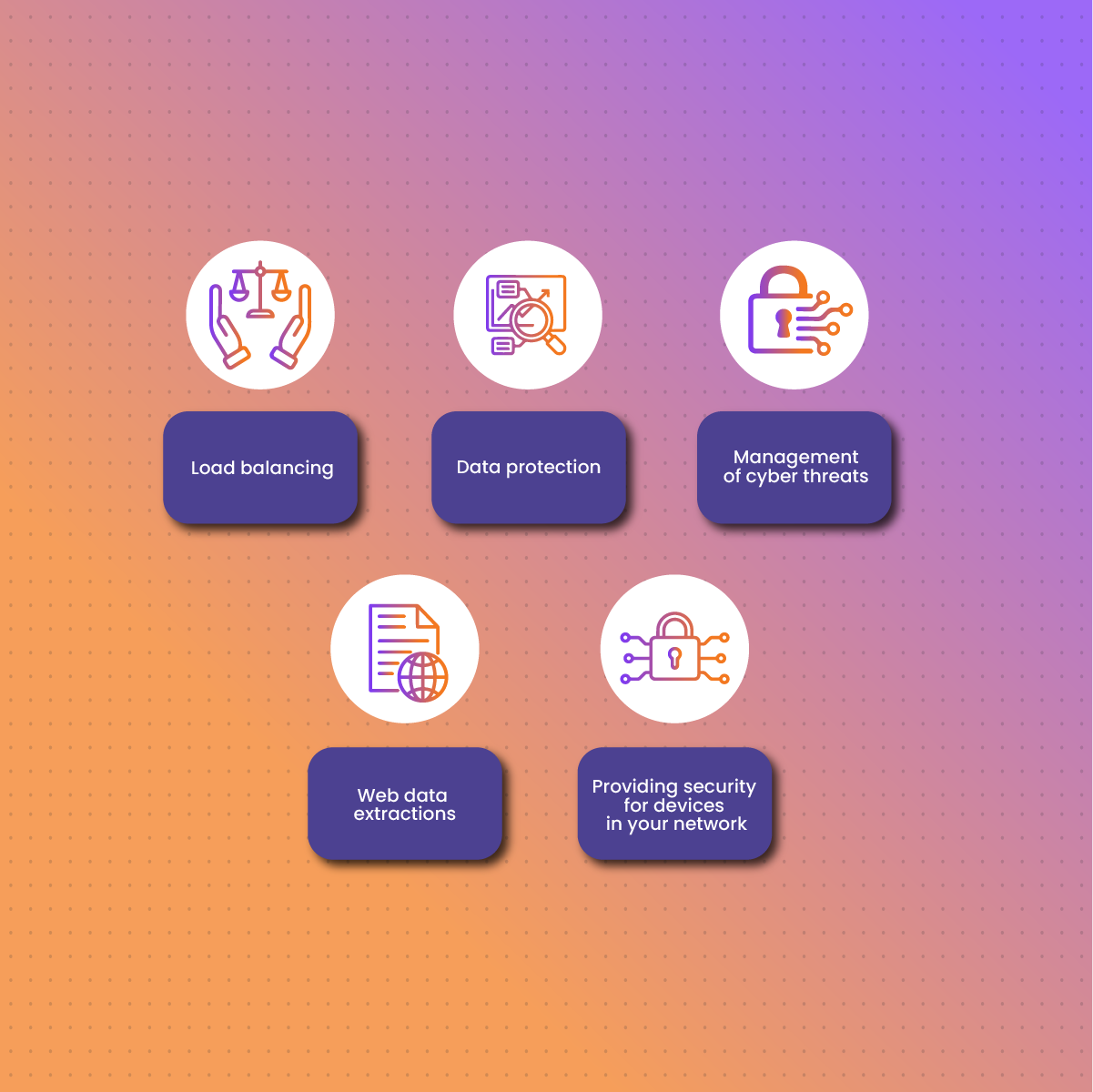
Load balancing
Load balancing is a crucial application of a cloud proxy. Web servers are prone to lagging or crashing when they receive excessive requests in a short time. However, proxies handle this challenge by evenly distributing the high load among servers closer to the clients. Subsequently, the cloud proxy prevents the server from being overwhelmed, which guarantees its efficiency and availability. Since it ensures a balanced workload, it optimizes the load time without sacrificing anonymity and security from potential cyber threats.
Data protection
Another significant application of cloud proxy is data protection. This proxy can ensure data protection by enforcing data loss prevention policies that disallow downloads or uploads (either intentional or accidental) of sensitive data to or from flagged cloud apps. Since the cloud proxy operates online and inspects all the network traffic, it ensures that the data uploaded or downloaded adheres to your policy.
Management of cyber threats
Cloud proxy plays a crucial role in the management of cyber threats to your network. If a file is infected with a virus or malware on the cloud service, it can quickly spread to connected devices and apps. However, cloud proxy prevents this disaster by preventing downloads or uploads of infected resources to or from cloud resources. In addition, the proxy also masks your server’s actual IP address from clients, which provides an additional layer of anonymity and protection from threats like DDoS (distributed denial of service) attacks.
Web data extractions
In recent years, many decision-makers have been largely influenced by data. However, they need access to large volumes of data from the past as well as current data to make predictions that determine their business operations. Therefore, storing data in the cloud becomes a more efficient option as it allows for easy access and sharing with the members of the team. Subsequently, businesses need to understand the best practices and tools for collecting web data.
A cloud proxy plays a crucial role in market research as it ensures uninterrupted and high-speed web data extraction. In addition, it hides your actual IP address to avoid IP bans so you can get updated data in real time.
Providing security for devices in your network
Many big organizations provide a central source of internet traffic for the workers. Subsequently, the employees use multiple devices, including personal ones, on the network. In addition, some suppliers, customers, or partners may need access to your internal applications on their devices, which can be a potential risk to the security of your network.
While you can manage devices owned by employees who physically work at the organization, managing devices outside your network can be challenging. This is because you may be unable to install agents to manage devices of these third-party devices that have access to your network. Therefore, a cloud proxy offers agentless protection against malware and data theft, especially from unmanaged devices that have access to your resources and cloud applications.
Choosing a Reliable Proxy Provider- NetNut

NetNut residential proxies are ethically sourced and automatically rotate your IP address at timely intervals to mimic human activities. In addition, they provide excellent protection against IP bans, which allows you to perform your tasks without limitations.
However, if you need an automated IP rotation system, our rotating residential proxies are the best solution for you. They offer the highest level of anonymity, security, and privacy that you can get. In addition, you can leverage ISP proxies to bypass captcha and geo-restrictions. Furthermore, NetNut proxies come with a guarantee of 99.9% uptime, which eliminates the chances of lag that can affect user experience.
Conclusion
We have examined the significance of a cloud proxy and how it protects your network from malware and data theft. Cloud proxies allow users to leverage the power of cloud infrastructure to enjoy scalable and efficient services, especially for businesses. Some of the applications of a cloud proxy include web scraping, load balancing, security, and data protection.
Are you looking for premium proxy services? Contact us today to get started and enjoy a free trial period.
Frequently Asked Questions
Is cloud proxy compatible with HTTP and HTTPS traffic?
Yes, a cloud proxy is compatible with HTTP and HTTPS traffic. Subsequently, it acts as a middleman between the server and the client, which allows for secure communication between both types of traffic. In addition, the cloud proxy can handle HTTPS traffic’s encryption and decryption process. As a result, this ensures the confidentiality and privacy of the data transmitted.
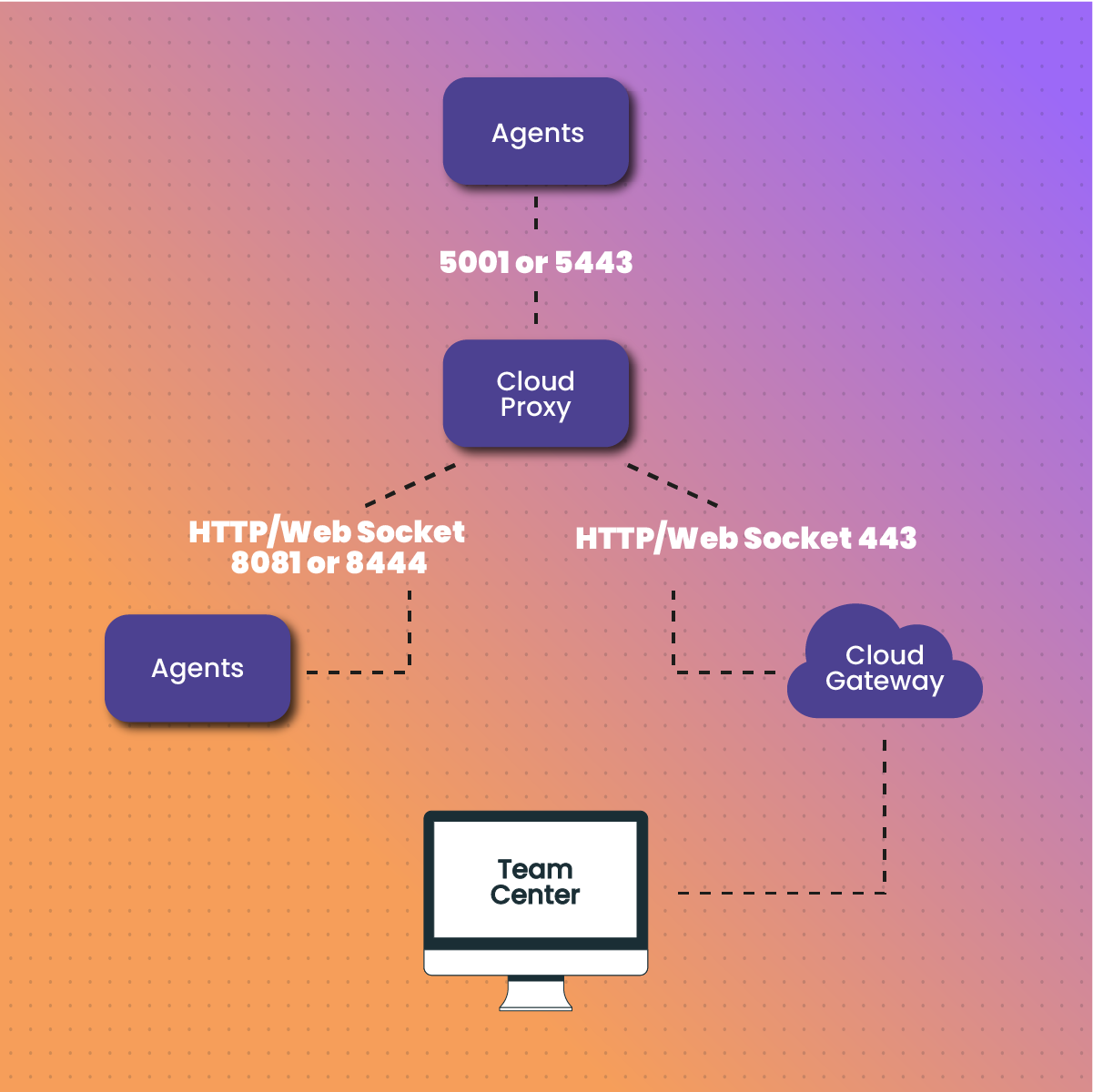
How does a cloud proxy work?
Here is a breakdown of how a cloud proxy works:
- The client sends a request, but it is received by the cloud proxy.
- Subsequently, the cloud proxy transmits the request to a firewall if applicable.
- The firewall can either block the request or pass it to the target server.
- Then, the target server processes the request and sends the response via the firewall to the proxy.
- Finally, the cloud proxy forwards the response to the client, which provides indirect communication between the client and server.
What are the limitations associated with traditional appliance-based proxies?
- Latency and slower internet speeds
- An expensive option for small businesses with limited budgets
- These proxies have compatibility limitations with certain network protocols.
- Appliance-based proxies present a single point of failure in the network architecture. Therefore, this vulnerability can result in downtime, security risks, and loss of productivity.