What is a Bot? Here’s Everything You Should Know About It
Bots are now predominant in the online space. They are being used by several businesses to perform repetitive tasks just like human employees but in an automated way. Everywhere you go online you will be interacting with different types of bots without even realizing it. In this article you will learn what a bot is, the different types, as well as what their different functions are.
While some are good, others can be exploited by hackers to cause malware and data breaches. Astra Security reported 5.5 billion cases of malware attacks in 2022 alone.
Let’s learn what bots are, how they work, as well as their setup and configuration process.
What Is A Bot?
A bot, short for “robot,” is a software application that has been configured to carry out certain tasks in an automated manner that would typically require human intervention. Bots are usually configured using a range of programming languages, machine learning, predictive analysis, and artificial intelligence to imitate humans and perform repetitive tasks. Bots operate over the internet, interacting with websites, applications, and users to perform a wide range of functions, from simple repetitive tasks to complex operations. They are programmed to execute these tasks quickly and efficiently, often much faster and more accurately than humans.
Even though a bot would perform repetitive tasks just like humans do, they are engineered to be prompt and faster. They can work by themselves based on programmed codes without needing humans to direct them or start the process. Many businesses and industries use bots to carry out several tasks, relieving employees from unwarranted stress and making the tasks faster.
On the flip side, some bots are engineered to harm computers and cause malware. Malware is the process where a device is exposed to malicious software that is capable of spying on and stealing personal information and passing it on to a bad actor. Malware is caused by bad bots and should be avoided at all costs.
As we go further, we will look at how bots work and how you can protect your devices from malware.
What are the Different Types of Bots?
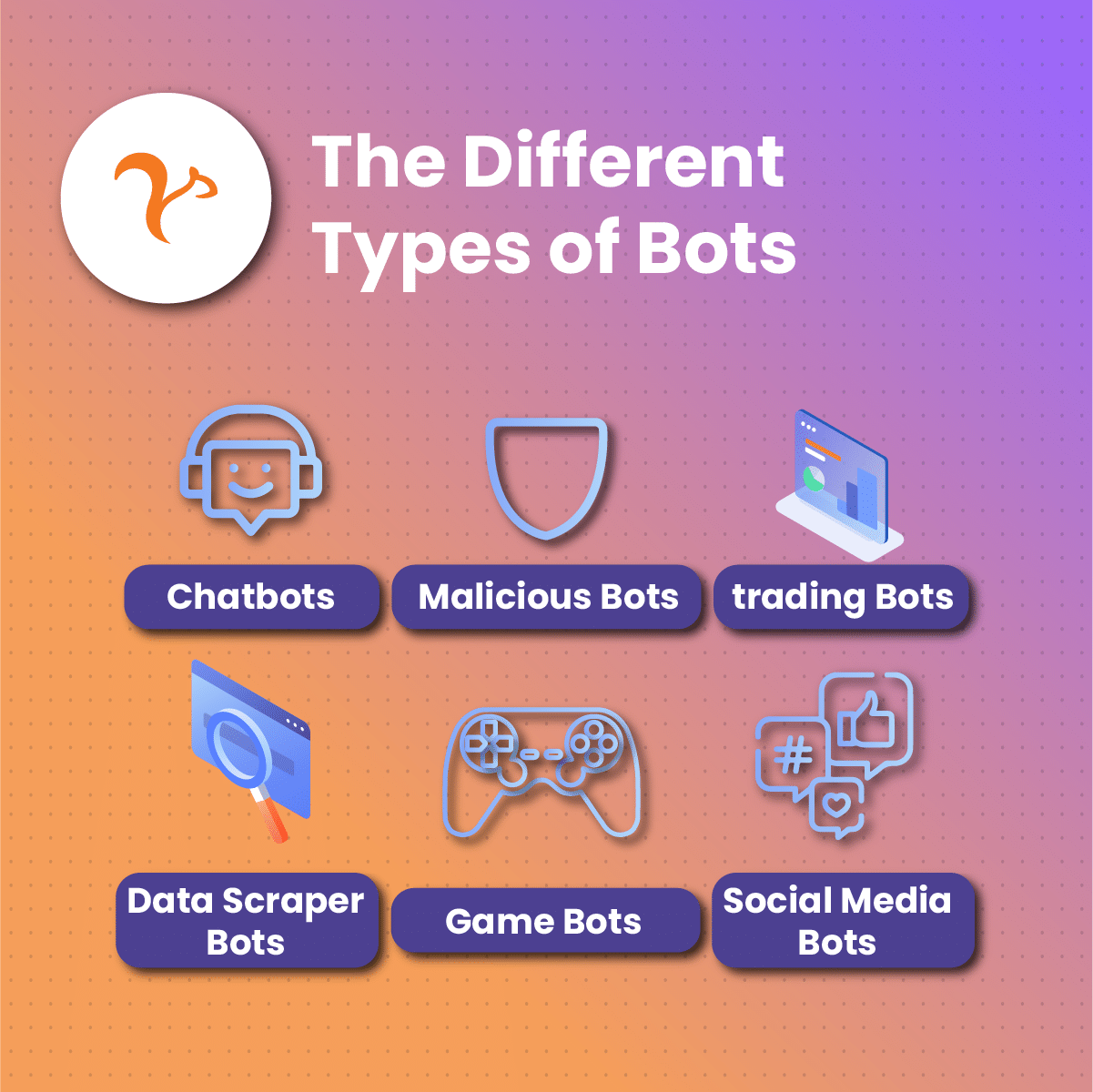
Bots can be categorized based on their functions and the tasks they perform. Below, we’ll explore six different bot types.
Chatbots
Chatbots are the most popular bot types we have out there. They work following a rule-based approach and can interact with people through written conversations based on predetermined prompts. These bots learn from human requests using machine learning and provide answers to search questions by tracking specific keywords. This ultimately fosters an interaction between them and humans.
Many businesses use chatbots for customer service operations. This allows them to extend operational hours because when customer service personnel close for the day, chatbots can still solve customer complaints. By automating customer interactions, chatbots improve efficiency and enhance the user experience.
Web Scraping Bots
Scraping bots are used to extract data from websites. They can gather information such as product prices, reviews, and contact details, which businesses use for competitive analysis, market research, and data aggregation. While scraping can be beneficial, it must be done responsibly to avoid violating terms of service and data privacy regulations.
These kinds of bots are notorious for driving traffic to different websites. They don’t only create content but also track global market prices, product reviews, and inventory data.
Have you ever tried to shop for an item online by simply searching on Google? You find the perfect site but after the page loads, you see yourself in a different environment. These are scraping bots at work. They redirect important data to entirely wrong sites.
Spider Bots or Web Crawlers
An alternative name for a spider bot is a web crawler. They are particularly used by search engines such as Bing, Google, and Opera to index and rank websites based on predetermined keywords and content. Search engines like Google use web crawlers to update their databases and ensure that search results are current and relevant. These bots scan web pages for content, links, and metadata, playing a crucial role in the functionality of search engines.
If you run a business and invest in search engine optimization, web crawlers are the bots that analyze your keywords and website content.
Spam Bots or Malicious Bots
These types of bots are notorious for bugging your device with unwanted content, otherwise called spam. When you interface directly with the internet, your IP address is exposed and these bots purposely scrape your information to start sending you unwanted content in the form of emails or text messages.
They can also use these pieces of information to create email addresses or run social media accounts that were previously stolen.
Unfortunately, not all bots are used for legitimate purposes. Malicious bots can be programmed to carry out harmful activities, such as spamming, phishing, and launching distributed denial-of-service (DDoS) attacks. These bots can overwhelm websites with traffic, steal sensitive information, and compromise security, posing significant threats to online safety.
Social Media Bots
This bot predominantly exists on social media to augment business and marketing efforts, especially if it has to do with influencing engagement or impressions.
They can imitate humans to churn out content on social media, and like, and repost several posts at a time.
Ticketing Bots
These bots are mainly used as money-making tools. They can buy high-demand shows or conference tickets. The user of the bot capitalizes on the high demand and then resells these tickets at outrageous prices.
How Do Bots Work?
Bots work in a way that isn’t as complicated as they seem. They’re usually designed to imitate humans but in an automated manner. Bots can use either natural language processing or a rules-based approach to perform tasks. What this means is that a bot can be still and can only start performing tasks the moment it’s triggered by request.
Bots, especially chatbots, will be set into action the moment there’s user interaction, and the process continues until an output is made.
Let’s assume you’ve patronized a business and you experience some hurdles that you want their customer service to fix. You head over to the live chat and start interfacing with a bot. Let’s use this scenario to further explain how a bot works.
- You start interacting with the chatbot by typing in a request. Note that for other bots, it may be some kind of a command that depends on their functionality. The bot sees this request as a likely trigger.
- The chatbot is now activated. Based on certain keywords, the bot starts processing your request using the algorithm it was built on. It could be the rules-based approach or the natural language processing. Once it’s done processing the information, it starts bringing points together to churn out content that will answer your questions in the best possible way.
- Once the points have been gathered, the bot creates constructive sentences and sends them out to you as a response. This response may be a single text message or one with options that you can select from to ensure all questions are answered.
Because these bots are repetitive, you can ask as many questions as you want. The cycle explained above will be repeated.
Good Bots On The Internet
A bot is good when it’s programmed and automated to be valuable to businesses or individuals. As the name suggests, they should be able to solve problems, make processes faster, and not cause harm.
Good bots enhance business processes and are of several kinds. They include:
Chatbots
These help to augment customer service processes by attending to requests and generating output based on predetermined keywords.
Web crawlers
They support search engines such as Google and Bing to index websites based on certain keywords and content and rank them on the platform.
E-commerce Bot
This is particularly useful in online shopping, helping buyers search through thousands of products, take orders, and track delivery.
Transactional bots
These are common among online traders, particularly stock and crypto traders. These bots are designed to buy shares and crypto assets when the prices are low to be resold at a higher price.
Social media bots
These are mainly used by businesses to augment growth and marketing. They help in generating more engagement and impressions.
Malicious Bots on The Internet
Generally, malicious bots are software programs that have been engineered to hack, spy, or steal sensitive information. Millions of people browse the internet daily without using a residential proxy and this exposes their IP addresses. These malicious bots leverage this to scan sensitive pieces of information and contact details through which spam messages and phishing links are sent.
Once videos or images are downloaded or phishing links are clicked on, a person’s device becomes infected with a virus. In other cases, funds may be lost by disclosing your account or bank information.
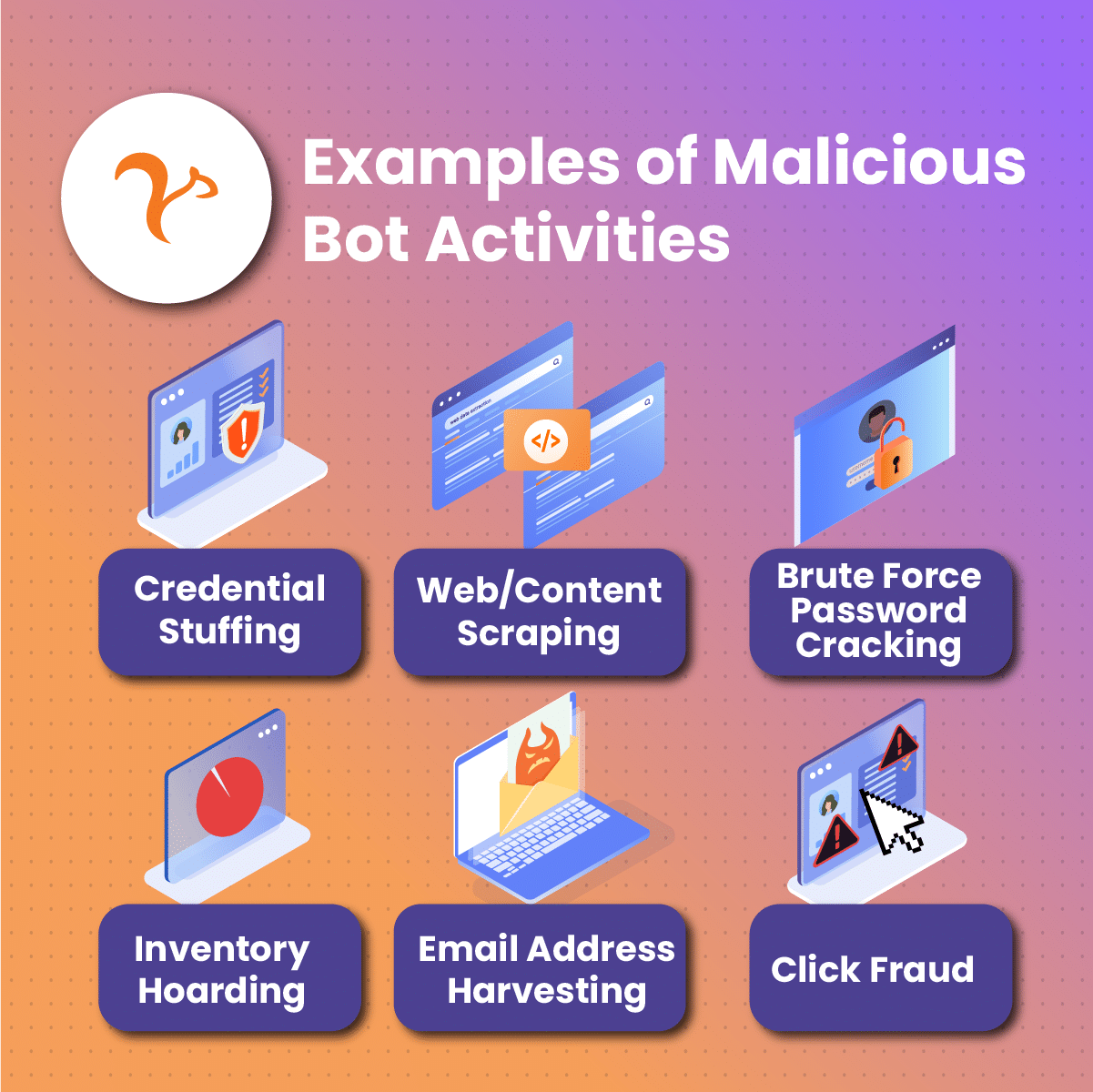
Several malicious bots exist and they include:
Spam Bots
These malicious software are designed to harvest personal information, especially email addresses, from public forums, booking sheets, conference sign-ups, or even job marketplaces. The bots then curate messages and randomly send them to these addresses. The results are usually a bunch of unwanted messages, phishing, or malware attacks.
File-Sharing Bots
These bots are strategically positioned to respond to online queries for movies or album downloads. The bot responds with a link which when clicked and downloaded, can infect the user’s device.
DDoS Bots
These bots are intentionally used to overwhelm the traffic of a targeted website, preventing it from carrying out normal service delivery. DDoS attacks can cost businesses large sums because customers won’t be able to access their services until the traffic is suppressed.
Other malicious bots include:
-
Traffic monitors
-
Download bots
-
Credential stuffing
Setting Up and Configuring Bots
Setting up and configuring a bot is quite technical. The process of creating a bot starts by listing some factors that need to be considered.
These factors include why this particular bot, the platforms it will be compatible with, the programming language to use (Python, JavaScript, or Node.js), user interaction, and request processing frameworks which could be a natural language processing or rules-based approach.
The Bot Setup and Configuration Process
One thing you should understand is that you don’t need to build a bot from scratch. Several software firms have bots that can be downloaded either for free or at a cost. However, it’s ideal to patronize a reputable service provider.
The steps outlined below explore how you can set up and configure your desired bot.
Download and Install the Bot Software
Once you’ve identified a reputable bot service provider, you can go ahead and download the application. Once done, navigate to your file explorer to find the downloaded bot software and install it. Then go ahead to set up your login details.
Navigate to the Dashboard and Personalize
When your login details have been set, you can sign in and head over to the bot’s dashboard. Proceed to personalize the bot’s details by using parameters that suit your business or personal needs. The details to customize include the name of the bot, a description of how it solves problems, and most probably an avatar that can be used to identify the bot.
Set up Query and Response Action
In this segment, you set up several frequently asked questions and possible answers. You should also input possible keywords that if contained in a user’s query, they should get answers.
Additionally, the response action can be configured to come as a single text message or further options users can click on to get answers to their questions.
Integration
Integrating your bot software is the last step. You can set it up as an Application Program Interface (API) or a web server, or directly integrate it into your business platform or community such as Telegram or Discord.
Final Thoughts on Internet Bots
Bots are software programs that are engineered to perform automated tasks. They can be beneficial to individuals and businesses or configured to maliciously cause harm.
In this comprehensive guide, we explored what a bot is, the types of bots, and how they work. We went on to see the differences between good and bad bots and how they operate.
We concluded with the steps to set up and configure bots for beneficial users.
Frequently Asked Questions (FAQs)
How can you protect your device from malicious bots?
As we saw earlier, malicious bots can be engineered to cause grave damage – from having virus-infected computers to data leaks, and possible loss of funds.
To prevent any of these from happening, you can protect your device with one or a combination of the strategies below:
- Regularly updating your device’s software
- Using ad blockers
- Avoid clicking random links
- Using rotational residential proxies to verify ads
- Using strong passwords with a combination of alphabets, numbers, and characters
Are there any legal concerns with bots?
While malicious bots are considered illegal due to the exploitative intent their developers have in mind, good bots, more than ever before, now raise legal concerns which is the possibility of deception.
For instance, when customers communicate with a business via a live chat feature controlled by a bot, there’s a tendency for them to feel comfortable thinking they’re iterating with humans. This, however, is considered a deceptive act.
Are residential proxies useful in protecting against malware bots?
Residential proxies are networks of inter-connected IP addresses that can mask a user’s original IP address, and enhance their privacy and anonymity online. With residential proxies from a trusted service provider, a user is protected from scam ads, malicious bots, spam bots, identity theft, and several others.
Even if a user unknowingly downloads malicious software, a rotation residential proxy can spot and ease it before the download is complete.