Introduction
A proxy acts as a bridge between the client and the server. It works by masking your IP address, which is crucial to maintain anonymity. When a proxy is deployed close to the client, it is described as a forward proxy. Meanwhile if the proxy is deployed closer to the server so that the clients cannot determine its origin is a reverse proxy.
There are several other proxy classifications based on different factors. Before the adoption of highly distributed data repositories, a database proxy provides connection pooling to the backend data repositories which ensures high availability by routing requests to a healthy data backend (standby when the primary fails) and reduces fall over time.
Therefore, this guide will focus on what a database proxy is, how it works, its advantages, choosing the best provider, and other FAQs.
What is a Database Proxy?
A database proxy is a type of reverse proxy designed for databases. It works by taking requests from clients like web applications and forwarding them to a database server via configurations specific to databases. A database proxy is different from traditional reverse proxies that primarily handle HTTP(s) traffic. Instead, it interacts with and manipulates database communication protocols. Subsequently, a database proxy acts as an intermediary which receives client requests then processes them based on predefined rules and forwards them to the appropriate database server.
How Does a Data Proxy Work?
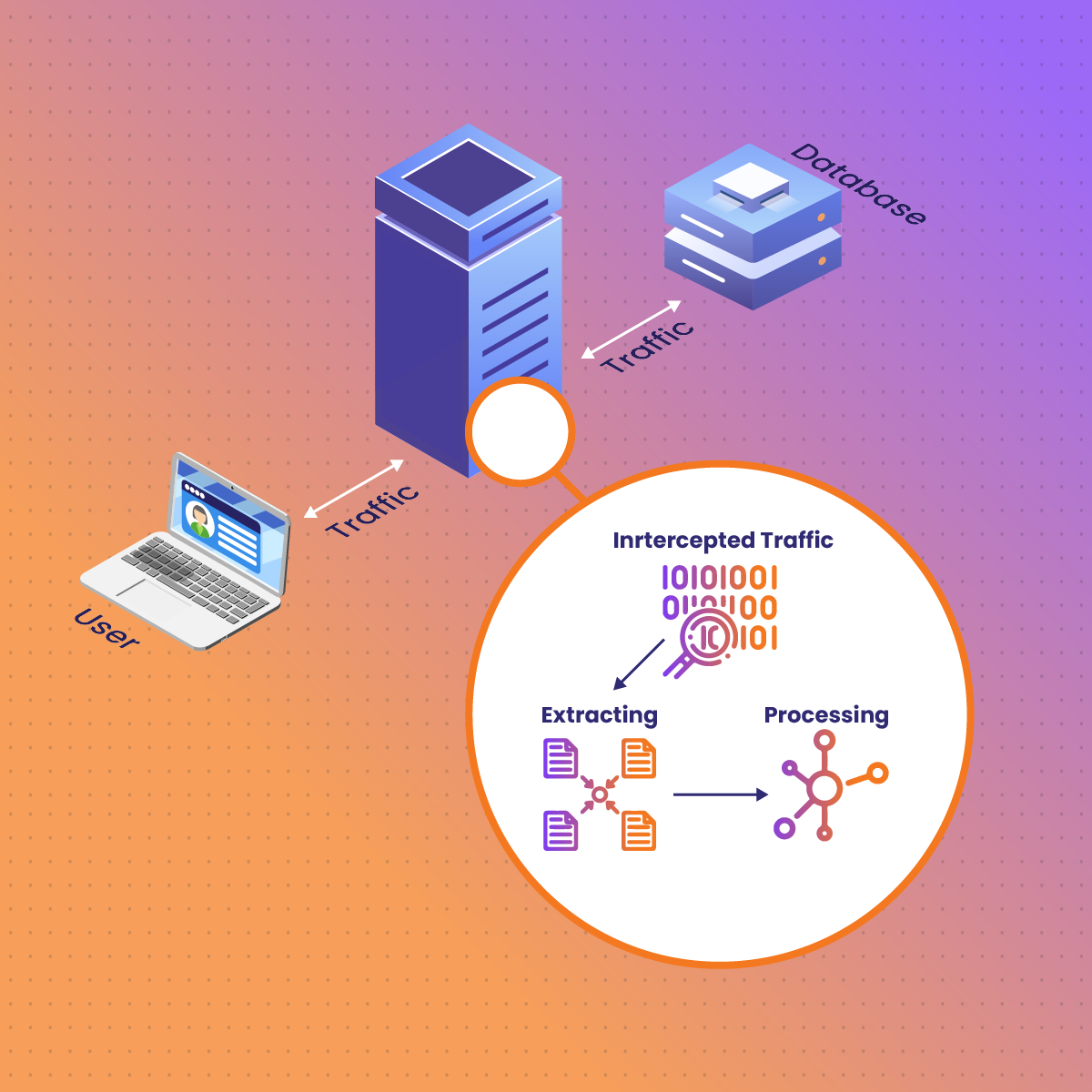
Database proxies are integrated into the system architecture as a middle layer between client applications and database servers. When a client sends a query, it is first intercepted by the proxy, which determines the most effective way to handle the request- reusing an existing connection, load balancing the query to an appropriate server, or caching the result. Subsequently, this process not only optimizes database performance but also enhances its scalability and reliability. The main components of a database proxy include:
- Connection manager: This handles the pooling and reuse of database connections.
- Query Router: Directs queries to the appropriate database server or cache
- Security layer: It monitors and filters incoming queries to prevent unauthorized access.
- Caching mechanism: The database proxy stores the result of frequent queries to reduce database load.
Popular examples of database proxy software include ProxySQL for MySQL and PgBouncer for PostgreSQL, both of which are widely used in production environments to optimize database performance. There are several benefits to using a database proxy and they include performance optimization, enhanced security, and scalability. In addition, database proxies offer failover capabilities that automatically reroute queries to a backup server if the primary server fails. Subsequently, this ensures high availability and reduces the risk of downtime. Be sure to read a recent guide on how a Cloud proxy works and its significance to your business.
Features of Database Proxy
Here are some of the features of a database proxy:
Intelligent request handling
One of the primary features of a database proxy is its ability to intelligently handle Structured Query Language (SQL) requests. This intelligence comes from the proxy’s deep understanding of database languages and protocols, which allows it to perform various tasks that extend beyond simple forwarding. For example, a database proxy can:
- Analyze SQL queries: It can determine the type of request and decide how best to process it.
- Route queries: A database proxy can direct specific queries to particular database instances, such as routing, writing queries to the primary database, and reading queries to read replicas.
- Rewrite queries: Database proxies can modify incoming queries before forwarding them to the database, and this optimizes them for performance with the server.
High availability
High availability is critical for database-dependent applications, which can be achieved with database proxies. These proxies can implement an automatic failover mechanism – if the primary database server fails, the database proxy can automatically redirect traffic to a backup server without any obvious downtime. In addition, database proxies play a crucial role in transaction replay- uncommitted transactions are replayed on a new server in case of a failure to protect data.
Scalability
Another crucial feature of a database proxy is scalability. They offer dynamic scaling of database clusters by adding or removing nodes without the need for reconfiguration or restarting client applications. Scalability provided by database proxies is particularly useful in environments where demand can fluctuate. Subsequently, the proxy handles the distribution of queries across the available database nodes, which balances the load and ensures optimized performance.
Security
Security is crucial in database management, and database proxies come with features to handle such concerns. A database proxy can enforce query and result limits to prevent misuse or overloading the database. In addition, these proxies can mask your data, which is crucial to hiding sensitive information in query results so that only authorized individuals can access it. Subsequently, this adds an additional layer of security, ensuring data is secured from both internal and external threats.
Integrations
A database proxy is equipped to integrate databases with other systems or applications. It can facilitate the real-time import or export of data between a database and other systems. This is crucial for applications that demand real-time data analysis. In addition, a database proxy can connect applications developed with NoSQL connectors to SQL backends which allows for better flexibility in database management.
Use Cases of A Database Proxy
This section will explore the various ways a database proxy can empower your development teams while optimizing database performance and data security.
Intercept SQL queries
A database proxy can interrupt SQL queries from applications and dynamically route them to the appropriate database. This is particularly useful in environments with custom sharding strategies where data is distributed across multiple databases. Big companies like Figma use their internal Postgres proxy for smart query routing to ensure each query reaches the right destination without interrupting the application.
SQL queries parsing, analysis, and validation
Another significant use case of a database proxy is to parse, analyze, and validate SQL queries and enrich the response with additional information. This is particularly useful in situations where applications need to be informed about impending changes, like identifying tables to be deprecated. Subsequently, when this is integrated into the development workflow, teams can actively manage changes in the database to avoid confusion.
Scalability and Schema Management
A significant challenge associated with managing large-scale applications is ensuring that changes to the database schema do not affect its operations. Therefore, database proxies allow the database teams to independently modify the schema without needing to rewrite microservices. In addition, they play a significant role in the addition and removal of nodes in the database cluster without the need to reconfigure or restart the application. A database proxy plays a significant role in ensuring scalability and optimal management of schema without affecting the applications.
Security
Database proxies play a crucial role in ensuring the security of the database. It performs authentication and authorization checks as a way to enforce security policies. Since it acts as an intermediary between the client and the database, the proxy ensures that only authorized persons can access the information on the database. In some cases, direct access to the database can be restricted as all interactions are directed through the proxy server, which adds an additional layer of security.
Optimizes performance
A database proxy plays a crucial role in optimizing the performance of the database communication. It can centrally manage the pool of connections to the database, which reduces the overhead associated with establishing and closing connections. In addition, database proxies use the cache technique to store frequently accessed data, thereby reducing the load on the database as well as improving the response time.
Centralized observability
Another application of database proxies is centralized observability, as they provide a central point for monitoring all database interactions. Subsequently, every member of the team receives a notification when an application uses a deprecated table. In addition, centralized observation ensures prompt identification and resolution of issues so that applications can run effectively as intended.
Choosing the Best Proxy Provider- NetNut
NetNut is an industry-leading proxy expert with an extensive network of over 85 million rotating residential proxies in 190+ countries and 5 million+ mobile IPS. Hence, they offer extensive coverage that allows users to access content that would otherwise be unavailable in their location.
NetNut boasts of one of the biggest IP proxy pools in the industry. Subsequently, users can access websites in various locations, which is necessary for exceptional data collection services.
These proxies offer excellent performance, anonymity, security, and high speed. Say goodbye to latency, as you are guaranteed 99.9% uptime. NetNut private proxies provide an additional layer of privacy as they mask your IP address to prevent passive fingerprinting.
Moreover, NetNut stands out as the best database proxies because they offer competitive and transparent pricing. If you need unbiased data for machine learning training data, NetNut proxies give you access to real-time data from all over the world to ensure your algorithm can make accurate predictions.
In addition, NetNut proxies come with an advanced AI-CAPTCHA solver. Therefore, you can leverage this powerful machine-learning algorithm regarding how to bypass a CAPTCHA. Bypassing CAPTCHA is necessary to avoid IP block and blacklisting, which are the top challenges associated with some of the use of proxies.
Furthermore, NetNut offers comprehensive documentation as well as integration tutorials for seamless user experience. You can also leverage our mobile proxies for automation and testing of mobile-based apps.
Conclusion
This guide has examined a database proxy and how it facilitates connection between clients and a database. It also plays a significant role in the performance, scalability, integration capabilities, and security of databases. Some of the use cases of database proxies include intercepting SQL queries, providing security, optimizing performance, and providing a central point of observation for all members of the team. Therefore, integrating a database proxy into your infrastructure plays a significant role in optimizing your ability to manage, scale, and secure your database.
Since a database proxy can intelligently manage traffic, it ensures that applications run securely and smoothly, even in a distributed environment. Choosing a reliable proxy provider like NetNut makes a significant difference in performance, scalability, and security.
Contact us today to get started and enjoy a 7-day free trial!
Frequently Asked Questions
What is the difference between a database proxy and a web proxy?
A database proxy is designed to handle database queries, while a web proxy handles HTTP requests between a client and a target server. In addition, a database proxy optimizes and secures database interactions, while web proxies play a crucial role in content filtering, access control, and anonymity. Therefore, you can use a database proxy if you want to optimize database access to improve performance and security. On the other hand, a web proxy is an ideal option when you need to bypass geographical restrictions, access blocked content, and protect privacy.
What are the advantages of using a database proxy?
There are several benefits of using a database proxy, but the chief one is that it isolates the database topology from the application configuration. Other advantages include:
- A database proxy eliminates the need for developers to create new connections or retry requests.
- It involves fewer codes, hence greater reliability, faster development, and less maintenance.
- Developers no longer have to worry about replicas or cluster nodes.
- Database proxies completely hide failures.
- They are transparent and hidden from application configuration.
- A database proxy can make crucial changes without interrupting application operation.
- It eradicates the need for developers to implement measures like data masking and load balancing as it automatically handles them.
- Database proxies can add or remove replicas and cluster nodes when necessary.
When should you use a database proxy?
It is crucial to mention that not all systems require a database proxy. Since a database proxy is a new element in your infrastructure, it could be a point of failure. In addition, it could cause additional network latency. Therefore, it has to be tested in several stages to ensure it is reliable and stable. Here are some instances where a database proxy is a necessity:
- You are operating a data-intensive system;
- Your system is distributed, and you maintain many databases.
- Multiple development teams (each with their specialty) make up the team like frontend teams, backend teams, data engineering team, etc.
- Your operation requires better security.