With recent advancements, proxies have served as intermediaries between clients and their destination websites by hiding information such as IP addresses and network ports. Alongside this advancement is the problem of logging and troubleshooting, as data is lost every time an account is proxied. This challenge can be fixed with proxy protocol, making your network communication easier while retaining privacy and security.
Keep reading this article to learn more about proxy protocol. This article explores all the benefits, versions, limitations, and types of proxy protocols.
Let’s dive right into proxy protocols and why they are important!
What Is A Proxy Protocol?
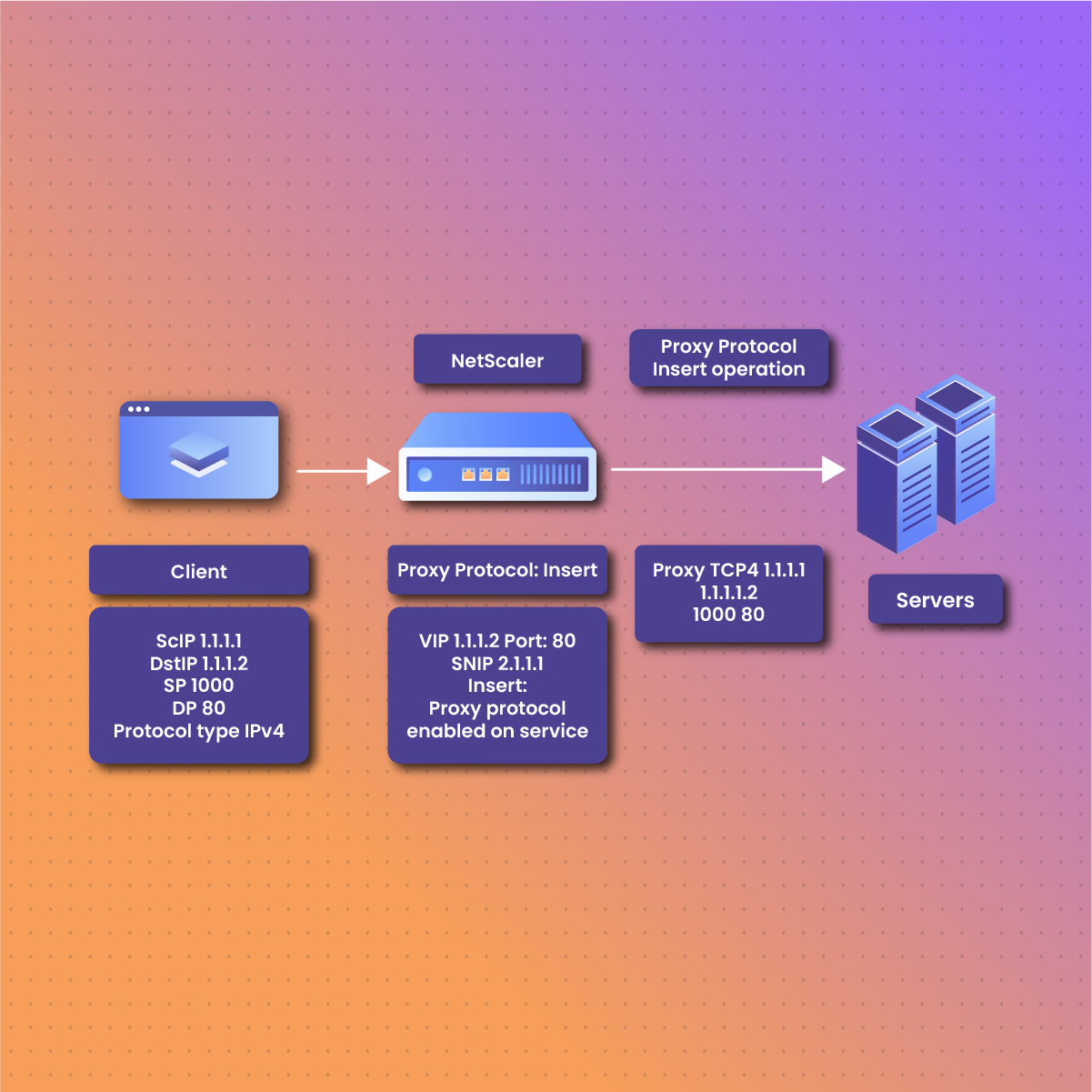
A proxy protocol is a communication protocol that connects users’ information to servers through a reverse protocol or load balancer. It allows servers to send information about the client, such as IP address and port number, to the designated server. With a proxy protocol, these pieces of information are preserved, aiding logging, troubleshooting, and security enforcement. This information typically includes the client’s IP address, port number, and protocol details, which are crucial for maintaining accurate client-server communication.
A proxy protocol is simply a way for a proxy server to communicate information about the original client and make a request to the destination server. It plays a crucial role in maintaining the transparency and integrity of your information while it moves through different servers. By preserving this data, proxy protocols enhance transparency, security, and efficiency in network operations. They are especially useful in scenarios involving load balancing, logging, and security monitoring, as they enable backend servers to have visibility of the original client’s information, ensuring better handling of requests and responses.
Why Do We Need A Proxy Protocol?
Clients’ information is exposed whenever a user account is accessed. A proxy protocol prevents this. These are some reasons why you need to use a proxy protocol.
Preservation Of Client’s Information
Usually, the original client’s information is hidden when a request passes through a proxy. The protocol helps preserve information such as IP address and network port, which enables the destination website to know the exact client details.
Security
Proxy protocol enhances security by ensuring the destination implements access control, performs IP-based filtering, and enforces security policies based on the original client’s IP address.
Transparency
It maintains the integrity of the client throughout the proxy journey by enhancing transparency in network communication. This aids regulatory requirements, compliance, and auditing.
Logging And Analysis
It helps log and analyze network traffic by providing the client’s original information. It helps identify potential threats, understand users’ behavior, and troubleshoot issues.
Versatility And Compatibility
These protocols are compatible with proxy servers and support IPv4 and IPv6 addresses. Due to its versatility, it is suitable for a wide range of networking environments. It ensures seamless integration and Compatibility.
Web Proxy Protocol Versions
The proxy protocol has grown to have two versions tailored to specific network conditions. The networks determine which is more effective, and thus, it is essential to know the difference between both versions to optimize the network framework.
Version 1 – The Human Reading Format
HAproxy introduced proxy protocol version 1, a simple non-binary protocol. Version 1 is well known for its human reading format, making it easier to understand and debug. It also adds readable headers at the beginning of a Transmission Control Protocol (TCP) connection, which includes the source and destination address and other information. It’s simple and easy to integrate into various network scenarios, especially those that don’t need high performance.
As a text-based proxy protocol, it is limited. For example, unlike binary format, it consumes more bandwidth, making it less efficient for high-throughput networks. It does not support IPv6 and lacks some extensibility features. It doesn’t support additional metadata or custom extensions. As such, it is not ideal for complex network configurations.
Proxy protocol version 1 is appropriate for modest-scale implementations or settings with little network traffic. It is perfect for configurations where network administrators prioritize effortless problem-solving and comprehensibility over efficiency. It is also employed in outdated systems that cannot be altered to accommodate binary protocols.
Version 2 – Designed for Performance and Scalability
Proxy protocol version 2 is an extension of version 1.
Unlike its predecessor, version 2 includes extra metadata and customizable extensions, enhancing its adaptability to various networking requirements.
It is suitable for high-performance networks such as data-centers and cloud infrastructure where efficiency and scalability are paramount.
It is also appropriate for intricate network configurations that need additional metadata to support advanced functionalities. It is preferred in environments experiencing heavy network traffic, where the overhead of a text-based protocol poses a bottleneck.
Despite its advantages, version 2 may lack backward compatibility with systems that solely support version 1, which warrants attention during network upgrades.
Comparing Version 1 and Version 2
When comparing the two versions, it’s essential to pay attention to the required features for each environment:
Balancing Performance and Readability
If your priority is high-performance and efficient traffic handling, Version 2 is the obvious choice, however, in simpler setups where clarity and ease of debugging matter more, Version 1 remains reliable.
Scaling for the Future
Version 2’s scalability positions it as the more future-proof option for networks expecting increased traffic and complexity.
Legacy System Integration
In environments dependent on legacy systems that support only Version 1, upgrading to Version 2 demands careful consideration of compatibility and potential upgrade necessities.
Meeting Custom Requirements
For a network setup that requires custom metadata or specific extensions, Version 2 is the best bet, as its extensibility renders it more adaptable to such demands.
Exploring The Different Kinds Of Proxy Protocols
Here are a few examples of proxy protocols used in various networking scenarios, each with strengths and limitations depending on factors such as type of traffic, security requirements, and architecture networks involved in their implementation.
HTTP Proxy Protocol
It is used for HTTP forwarding. It functions at the application level and is often used for web browsing and content filtering.
Socks Proxy Protocol
The SOCKS (Socket Secure) Proxy Protocol supports various types of network traffic, such as TCP, UDP, and ICMP. It operates at the transport layer, providing greater flexibility in managing different types of network traffic.
SSL/TLS Proxy Protocol
It intercepts and decrypts encrypted SSL/TLS traffic for inspection purposes while maintaining security protocols; it functions at the application level, allowing proxy servers to examine encrypted data without compromising safety measures.
Transparent Proxy Protocol
It works by intercepting network traffic without requiring client-side configuration; operating at the network layer provides an effective solution for content caching, filtering, and monitoring purposes.
PAC or “Proxy Auto-Configuration” Protocol
It automatically configures proxy settings within web browsers using a JavaScript file hosted on a server that instructs specific URLs or types of traffic on which proxy server to use.
How To Implement A Proxy Protocol
To implement the proxy protocol successfully, it’s crucial to begin carefully, understanding the prerequisites and the initial setup process. Configuring the protocol varies depending on the environment; for instance, settings in NGINX may differ from those in HAProxy. Following detailed guidance specific to your environment is germane for a smooth implementation. Additionally, being aware of common pitfalls and having troubleshooting strategies in place is essential to address any issues that may arise during the configuration process.
Load Balancing
Load balancing is a crucial aspect of network management, entailing the distribution of network or application traffic among numerous servers. The proxy protocol enriches load balancing by furnishing the load balancer with the original client IP addresses, thus facilitating better routing decisions. Real-world case studies demonstrate the substantial optimization potential of the protocol in enhancing the functionality and efficiency of load-balancing solutions.
Safety Issues
The connection between the proxy protocol and network security is intricate. While the protocol is vital for maintaining client information integrity, it can also present security challenges if not properly implemented. Establishing best practices for securing data transmission when utilizing this protocol is paramount. This involves verifying the authenticity of client information and safeguarding against potential vulnerabilities that may result from its mishandling.
Advanced Study In Proxy Protocol
Beyond fundamental setups, the proxy protocol can undergo customization and integration with various network technologies and protocols to accommodate intricate network landscapes. Delving into these advanced applications, such as integration with cloud services and the Internet of Things (IoT), unveils the adaptable character of the proxy protocol. Furthermore, keeping pace with forthcoming trends and advancements in this technology is imperative for network professionals aiming to harness its complete capabilities.
Industry Relevance
Numerous industries, from telecommunications to cloud computing, have successfully utilized the proxy protocol to bolster their network infrastructure. By analyzing case studies from tech powerhouses, one can glean how they have integrated the proxy protocol into their networks. These examinations provide invaluable insights and exemplary approaches that other enterprises seeking to implement this protocol in their network architecture can adopt.
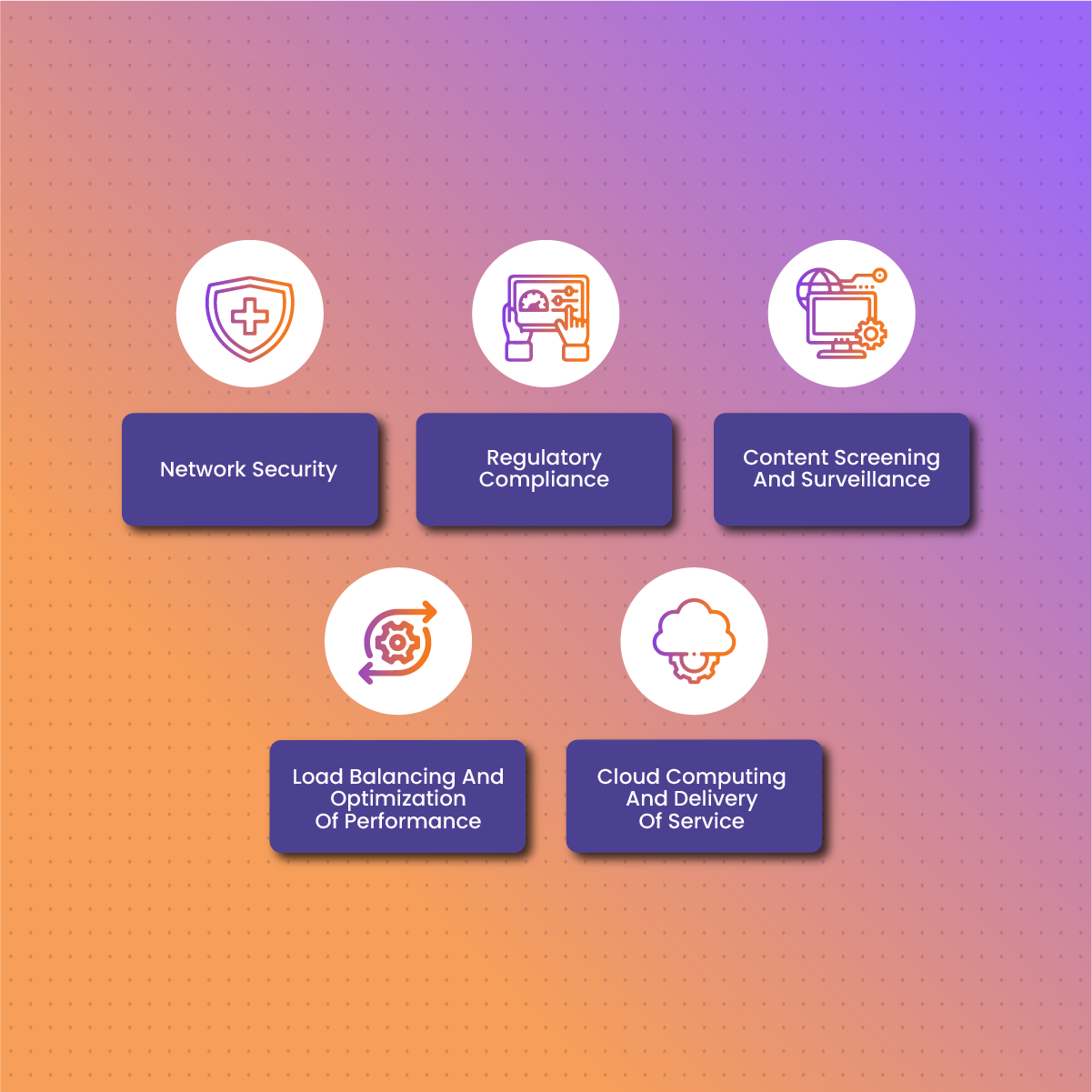
Network Security
The proxy protocol boosts network security in sectors handling sensitive data, such as finance, healthcare, and government, by furnishing precise client information to destination servers. This facilitates robust access controls, intrusion detection, and network traffic monitoring, fortifying defenses against cyber threats and unauthorized access.
Regulatory Compliance
Industries adhering to regulatory compliance standards, like banking, healthcare, and telecommunications, find value in the transparent communication upheld by the proxy protocol between clients and servers. It assists in meeting data protection regulations, audit demands, and industry benchmarks by preserving comprehensive client connection details for logging and analysis.
Content Screening And Surveillance
Organizations in education, corporate environments, and public institutions utilize this protocol to implement content filtering policies since it accurately identifies the origin of client requests. Therefore, administrators can enforce content restrictions and effectively monitor user activities while preventing unauthorized access to restricted content.
Load Balancing And Optimization Of Performance
In e-commerce media streaming or online gaming, where high availability is critical, proxy protocol facilitates load balancing across server clusters, enabling intelligent routing, optimized resource allocation, and enhanced scalability, ensuring seamless user experiences and efficient resource utilization.
Cloud Computing And Delivery Of Service
Proxy protocol plays a crucial role in cloud computing environments by enabling transparent communication between clients and proxy backend servers, benefiting industries leveraging cloud infrastructure software as a service (SaaS) and platform as a service (PaaS). The ability of this protocol to maintain consistent client information across distributed systems ensures seamless integration, efficient resource allocation, and centralized management of network traffic, promoting effective service delivery platforms for businesses using this technology.
Frequently Asked Questions About Proxy Protocols
What are the Benefits of Using Proxy Protocols?
A proxy protocol can improve network performance by providing transparent communication between the clients, proxies, and destination servers. It enables efficient resource allocation and optimization of traffic routes.
What Should You Consider When Implementing Proxy Protocol?
To implement the proxy protocol, you should understand the prerequisites, potential security risks, compatibility with the system network, and the impact on network performance.
What Industry Is A Proxy Protocol Of Great Benefit
It’s essential to industries dealing with network and security, regulatory compliance, cloud computing, etc. It’s highly beneficial to industries dealing with sensitive data.
Conclusion: What Does The Future Hold For Proxy Protocols?
With ongoing advancements in the digital sphere, applications and features will evolve accordingly. As network professionals, you must stay informed about these advancements to fully leverage proxy protocol’s potential in your network management approaches. Keeping up with the advancements could be easier if you get assistance from a professional. NetNut supports protocols like the SOCKS and HTTPs. See our full list here.
We understand the complexities of proxies and have provided services like rotating residential, ISPs, mobile, static, and US residential proxies to help you scale your businesses or personal needs.