Introduction
Making a choice between HTTPS proxy vs SOCKS5 requires a comprehensive understanding of how each of them works. Subsequently, you can leverage the information to find the best option between HTTPS proxy vs SOCKS5.
As the world is evolving, the need for proxies becomes more significant. They act as an intermediary between your device and the web. Individuals, researchers and businesses need proxies for various purposes. One of the prominent challenges to surfing the internet is geographical restrictions. This happens when a website has been customized to block IPs coming from outside the accepted region. Before you can view a web page, your browser sends a request, which is accompanied by the IP address. Subsequently, the website can interact with your IP address to identify your location and other identifying information. As a result, using proxies ensures the website can only access the proxy IP. Consequently, this increases anonymity, privacy and data security of online activities.
In addition, proxies provide an extra layer of cybersecurity against cyber attackers attempting to steal your personal information. Moreover, the use of proxies can reduce the load of network traffic. Subsequently, this helps you save a lot on bandwidth as well as the time and resources required for websites to load.
Therefore, this guide will examine HTTPS proxy vs SOCKS5, how they work, the benefits they provide and some differences between them.
What is HTTPS?
HTTP (Hypertext Transfer Protocol) is a popular protocol used on the internet. However, it has a major drawback- all information is transmitted as normal text. Subsequently, anyone, including cybercriminals, can see them. Meanwhile, the text may contain private information, including usernames, passwords, phone numbers, addresses, credit card details, social security numbers, and more. As a result, HTTPS was introduced to mitigate the security risks associated with using HTTP.
HTTPS- Hypertext Transfer Protocol Secure, as the name suggests, is a secure HTTP protocol that encrypts all the transmitted data. In addition, HTTPS uses Transport Layer Security (TLS) or Secure Sockets Layer (SSL) protocols to verify the identity of the web server.
The TLS uses cryptography to secure data while the SSL leverages on keys- private and public keys as well as digital certificates to encrypt the data. HTTPS was created in 1994, and it worked with SSL. However, by the beginning of the 20th century, the use of TLS became the standard practice. The adoption of TLS took a while because the certificates were expensive and required additional technical knowledge.
HTTPS Proxy vs SOCKS5: What are HTTPS Proxy?
To understand HTTPS Proxy vs SOCKS5, we need to examine them. HTTPS proxy is a form of HTTP proxy that is secure as indicated by the “S”. Regarding the HTTPS proxy vs SOCKS5, the former uses an SSL connection to provide an additional layer of security for private information such as username and password.
Subsequently, it is often preferred to the HTTP proxy, where data, including sensitive ones, can be intercepted. When you access the internet, the internet service provider usually intercepts all your activity. This can be a way of generating a browser fingerprint that can be used to identify your browsing behavior. Subsequently, they store these logs of data as proof of your online activities. Therefore, the HTTPS proxy helps safeguard personal data. In addition, the HTTPS proxy encrypts your network traffic to avoid interception by these algorithms.
HTTPS proxy, also known as SSL proxy, are intermediaries that only listen to HTTPS traffic on port 443. Subsequently, all the elements of the HTTPS requests are encrypted so they can only be viewed at the endpoint.
How Does the HTTPS Proxy Work?
Regarding HTTPS Proxy vs SOCKS5, we need to examine how the latter works. First, the HTTPS proxy connects to your network and encrypts your traffic. Subsequently, using HTTPS proxy minimizes the possibility of others finding out the kind of information that is transmitted via the proxy server.
Usually, the process of encrypting and decrypting data involves the browser and the target website. Therefore, the HTTPS proxy is involved in the passive transfer of the encrypted data. As a result, you can use the HTTPS proxy to transfer any TCP protocol. In other words, the HTTPS proxy can be used as an IMAP(Internet Message Access Protocol), POP3(Post Office Protocol Version 3), NNTP(Network News Transfer Protocol), and SMTP(Simple Mail Transfer Protocol) proxy.
Benefits of using the HTTPS proxy
Here are some of the advantages of using the HTTPS proxy:
Protect private data
One of the primary advantages of using the HTTPS proxy is that it safeguards user data by not storing the data on the client system (browser). HTTPS proxy stands out for its data encryption, which ensures your data is secure even in transit.
Therefore, the data is not vulnerable to attacks by cybercriminals. In other words, your sensitive information cannot be misused because it is encrypted.
Data validation
Another advantage of using an HTTPS proxy is it assures the correctness of the data transmitted. Subsequently, the policy of a certificate must align with the policy of the website. Therefore, HTTPS proxy ensures that user data is sent securely to the correct website, which is necessary to build trust.
In addition, HTTPS proxy uses a handshake to validate. Subsequently, all the components of data transfer, including the sender and receiver, are validated. Therefore, if validations are unsuccessful, the operation will be terminated.
SEO
HTTPS proxy is an excellent choice for SEO activities. It is an indication to Google to rank a website higher. In other words, a website with HTTPS certificates ranks higher in Google search engine results.
Reliable and efficient
When considering the HTTPS proxy, it is important to keep in mind that they are reliable and efficient. Subsequently, they give visitors confidence that the website they are visiting is secure and free from malware.
Limitations associated with HTTPS proxy
Despite the benefits of using the HTTPS proxy, there are a few limitations. They include:
HTTPS proxy is expensive
Using HTTPS proxy requires SSL certificates, which can be expensive. Usually, the website hosting provider charges a fee at some intervals to renew the SSL certificate. Although there are various methods of obtaining a free SSL certificate, they are not recommended because they can pose security issues.
Speed of performance
The speed of performance may be inhibited when using HTTPS proxy because it requires a lot of computation. As a result, the response time may be slower, which causes the website to be slow.
HTTPS Proxy vs SOCKS5: What are SOCKS5? 
Understanding HTTPS proxy vs SOCKS5 involves a comprehensive knowledge of how the latter works. SOCKS5 stands for Socket Secure version 5, which is the latest version of the internet protocol. It works with a TCP- Transmission Control Protocol connection, which sends and receives data packets across the internet.
Moreover, the SOCKS5 proxy can hide your actual IP address and bypass geographic restrictions. This version of SOCKS is usually preferred because it comes with advanced features and broader support for different protocols.
How SOCKS5 proxies work
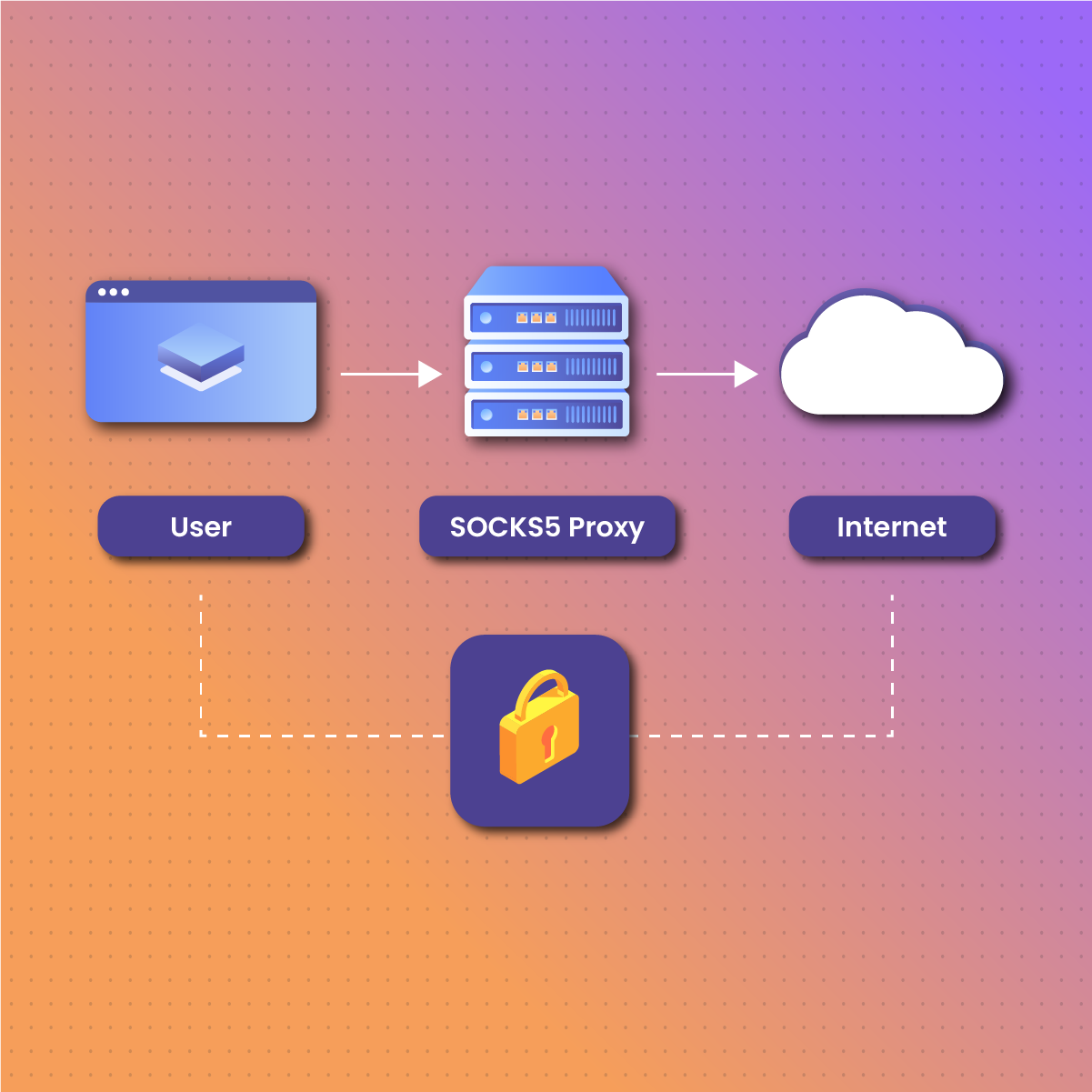
SOCKS5 proxies work by transmitting data between a browser and web server via TCP- Transmission Control Panel. The TCP establishes a connection between the client and the server to ensure that data reaches its target destination. Once the connection is established, the SOCKS5 transmits incoming and outgoing data between the browser and the target website.
SOCKS5 is the updated version of SOCKS4 that encrypts data in traffic via the Secure Shell (SSH) encrypted tunneling method. In addition, SOCKS5 proxies can handle various protocols such as HTTP, SMTP, and FTP.
Benefits of using SOCKS5
Here are some benefits of using SOCKS5 proxies:
Compatibility with any network protocol
One of the benefits of using a SOCKS5 proxy is that it can establish a TCP connection. In addition, SOCKS5 can use UDP- User Datagram Protocol connection to deliver datagrams over a network. This is necessary to ensure the efficiency of performance.
Bypass online blocks
Online blocks are very common as many websites are optimizing their security. However, SOCKS5 proxies can be used to bypass these blocks easily. For example, if your IP is blocked due to geographical restrictions, you can still access the content via the SOCKS5 proxy. It works by routing your traffic through the proxy server so that the website does not identify your actual IP address.
Optimized performance
Using SOCKS proxies ensures you encounter fewer errors, which improves the overall performance. Some other types of proxies rewrite the headers on data packets, which increase the chance of mislabelling or misrouting the data. However, SOCKS5 proxies do not rewrite data packet headers, so this reduces the chances of errors. Subsequently, with fewer errors, the performance of the proxies significantly increases.
Faster and more secure connection
Another advantage of using SOCKS5 is that it is fast because it can use the UDP protocol. Unlike other proxy types that rely solely on TCP connections, it ensures a faster connection and efficient performance.
Thanks to the UDP protocol, the SOCKS5 proxy moves data very quickly while offering a reliable and secure connection. In addition, the SOCKS5 proxy server can cache data, which optimizes your internet experience speed. Another tip to ensure faster connection is to choose a SOCKS5 proxy server that is closer to your location.
HTTPS proxy vs SOCKS5: What is the Difference?
Regarding HTTPS proxy vs SOCKS5, they are both methods of changing your IP address and routing your network traffic through a server.
When using an HTTPS proxy, the server encrypts your traffic. In other words, the communication between your device and the target website is secure. However, the HTTPS proxy does not actively participate in the encryption and decryption- it passively transfers the encrypted data. Subsequently, the HTTPS proxy allows for the transfer of almost all TCP protocols. On the other hand, the SOCKS5 does not use encryption to protect data transmission but offers a superior security level.
SOCKS5 has a wider range of compatibility than HTTPS. Subsequently, the SOCKS5 proxy supports TCP, UDP and other protocols. In addition, the SOCKS5 protocol does not penetrate data, which means you can use it with any kind of connection, including POP3. On the other hand, HTTPS proxy only supports TCP data.
Another difference between HTTPS proxy and SOCKS5 is encryption. HTTPS proxy supports encryptions, but this could significantly reduce the speed. On the other hand, SOCKS5 lacks encryption, which makes it a faster alternative. Another factor that makes SOCKS5 faster is that it supports UDP and TCP transfer protocols. Therefore, it supports DHT, which maximizes the download speeds.
SOCKS5 is commonly used for P2P networking and remote DNS resolution- these activities require high speed and flexibility. Meanwhile, the HTTPS proxy is most commonly used for web browsing and API access, which require high data security. With SOCKS5, there is no transmission loss. However, there is some transmission loss when using an HTTPS proxy.
HTTPS proxy primarily uses certificates as a means of verification. On the other hand, SOCKS5 leverages username and password authentication.
HTTPS Proxy vs SOCKS5: Applications
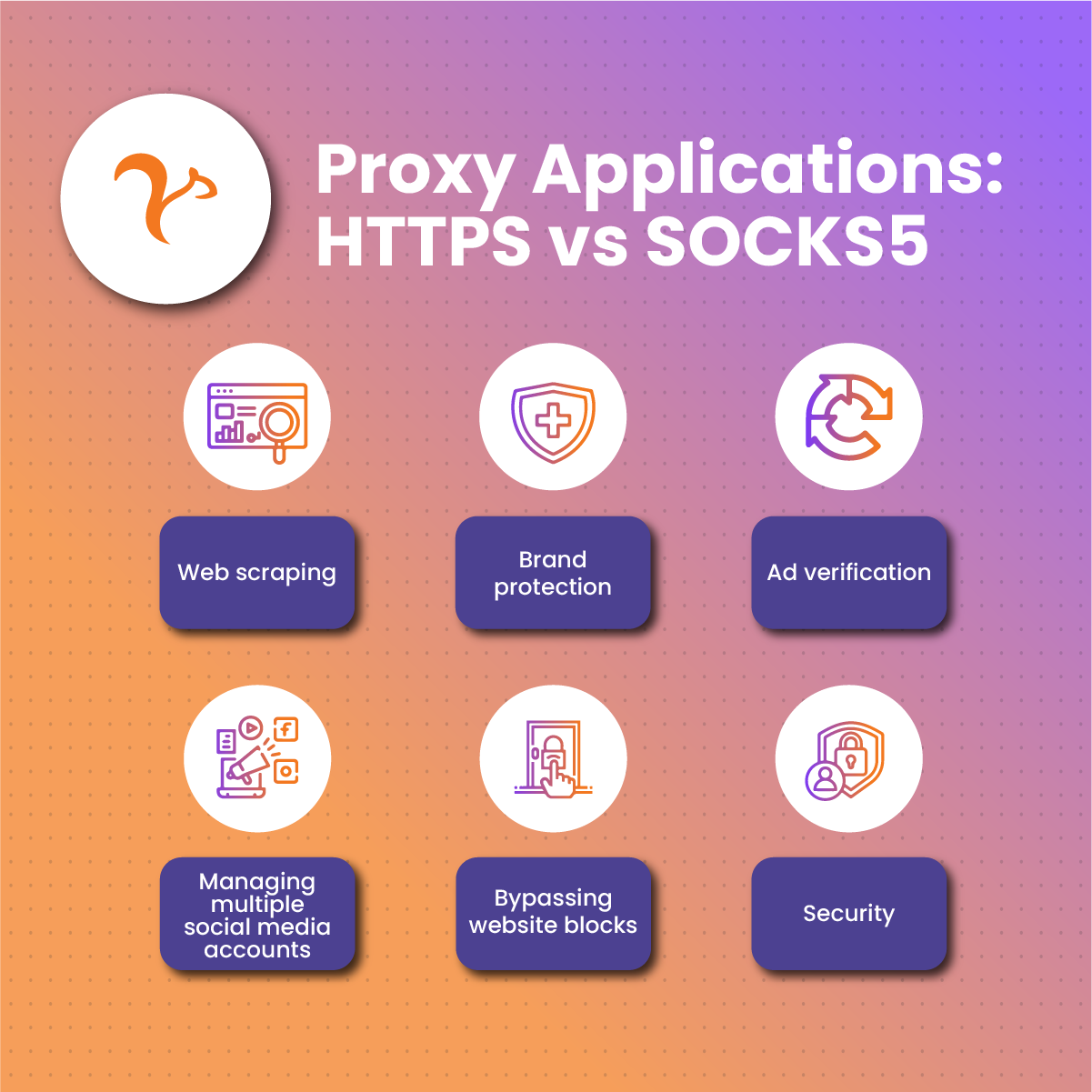
Proxies, whether HTTPS or SOCKS5, can be used for various purposes including:
Web scraping
Web scraping has become vital to many organizations. However, there are many challenges to extracting data from websites. Some of these challenges include CAPTCHAs and IP blocks, and they significantly hinder the process of web scraping. Therefore, using an HTTPS proxy or SOCKS5 allows for easy bypassing of these challenges, which allows them to collect the data they need to make critical decisions.
Brand protection
Another significant application of proxies is brand protection. As the world is going digital, more companies are taking their business online. However, this has opened up the door for counterfeiting, copyright infringement, and theft of intellectual property. Therefore, businesses can leverage proxies to establish a secure connection to monitor their brand reputation across various states and countries.
Ad verification
Using proxies provides an anonymous and secure environment for ad verification. Ad verification is important because it helps marketers track the efficacy of their campaigns. In addition, they can detect ad fraud and confirm if the ad is reaching the target audience. Subsequently, this activity becomes seamless with the use of proxies that route network traffic through the proxy server.
Managing multiple social media accounts
Social media managers may need proxies to manage their multiple social media accounts. However, they are prone to data leaks, which can become a serious problem. Therefore, it becomes crucial to use proxies as a way to provide security and anonymity for managing social media accounts.
Bypassing website blocks
Website blocks are not uncommon in this digital era. They are often largely geographical restrictions that prevent individuals from other countries from accessing a particular content. Using HTTPS proxy or SOCKS5 proxies provides an excellent solution to bypassing website blocks. Alternatively, NetNut website unblocker is efficient in helping you bypass website blocks.
Security
Using HTTPS proxy or SOCKS5 provides security when you are online. Data security has become an increasing concern for internet users, with an increase in cyber theft. Therefore, hiding your IP address becomes necessary to mask your digital footprint. Cybercriminals can use your IP address to track you.
Our Recommendation for HTTPS proxy or SOCKS5: NetNut
Whether you opt for HTTPS proxy or SOCKS5, you need a reputable proxy provider. The dangers of using free proxy services are that your data is not secure, and anonymity may be compromised. Therefore, it becomes critical to choose an industry-leading proxy server provider like NetNut.
NetNut has an extensive network of over 52 million rotating residential proxies in 200 countries and over 250,000 mobile IPS in over 100 countries, which helps them provide exceptional data collection services.
NetNut rotating residential proxies are your automated proxy solution that ensures you can access websites despite geographic restrictions. Therefore, you get access to real-time data from all over the world that optimizes decision-making.
NetNut offers various proxy solutions that support HTTPS and SOCKS5 protocols. In addition, the proxies promote privacy and security while extracting data from the web.
Alternatively, you can use our in-house solution- NetNut Scraper API, to access websites and collect data. Moreover, if you need customized web scraping solutions, you can use NetNut’s Mobile Proxy.
Conclusion
This guide has examined HTTPS proxy vs SOCKS5, what makes each unique and their differences. However, you must remember that making a choice depends on your particular needs. SOCKS5 proxy may be a suitable alternative when you need to download and transfer large volumes of data. On the other hand, an HTTPS proxy can be used to access restricted content and protect your online activities.
Ensure you consider the situation and various factors before buying a proxy. Feel free to contact us if you need help choosing the best proxy solution for you.
Frequently Asked Questions
Can you use HTTP instead of HTTPS proxy?
Yes, it is possible to use HTTP instead of HTTPS proxy. However, you need to understand that you will not get any encryption for optimized security. Subsequently, the HTTP proxy will forward the unencrypted HTTPS traffic between the client and server.
Can you get a free SOCKS5?
Yes, you can get a free SOCKS5. However, using a free proxy is not recommended if security and privacy are your priority. Free SOCKS5 often have poor performance due to several reasons- less support personnel, slower infrastructure, and more.
Since you are not paying for the SOCKS5, the provider can monitor your traffic and sell your data to third parties. Subsequently, these third parties use the data to display ads that they think you might find relevant.
What are the types of HTTPS proxies?
There are two types of HTTPS proxies, and they include:
- HTTPS Server Proxy
HTTPS server proxy allows connections from external web clients to internal web servers via the internet. In addition, it uses certificates which differentiate it from the HTTP server proxy. Using an HTTPS server proxy requires you to export the default certificate used by your web server to the proxy. Subsequently, the certificate allows the HTTPS server proxy to encrypt and decrypt the data.
- HTTPS Client Proxy
The HTTPS client proxy allows connections from a web client to the internet. Therefore, to use the HTTPS client proxy, you need to import a client certificate to use by the device you installed the proxy. Subsequently, this allows the proxies to encrypt and decrypt data like it was the originator of the request or terminator of the responses.