How to Buy a Proxy: A Comprehensive Guide For Internet Users
A proxy plays a critical role in the virtual landscape. It empowers businesses and individuals to perform online activities such as data scraping, price monitoring, marketing, and accessing content restricted based on location.
Given these benefits, how then can you buy a proxy that aligns with your goals while being on a slim budget? With proxies, clients don’t have to worry about their identities or IP addresses being exposed.
Proxies provide vast levels of anonymity and security. In this article, we will explore proxy in its entirety, the types, use cases, and the steps required to buy a proxy.
What is a Proxy?
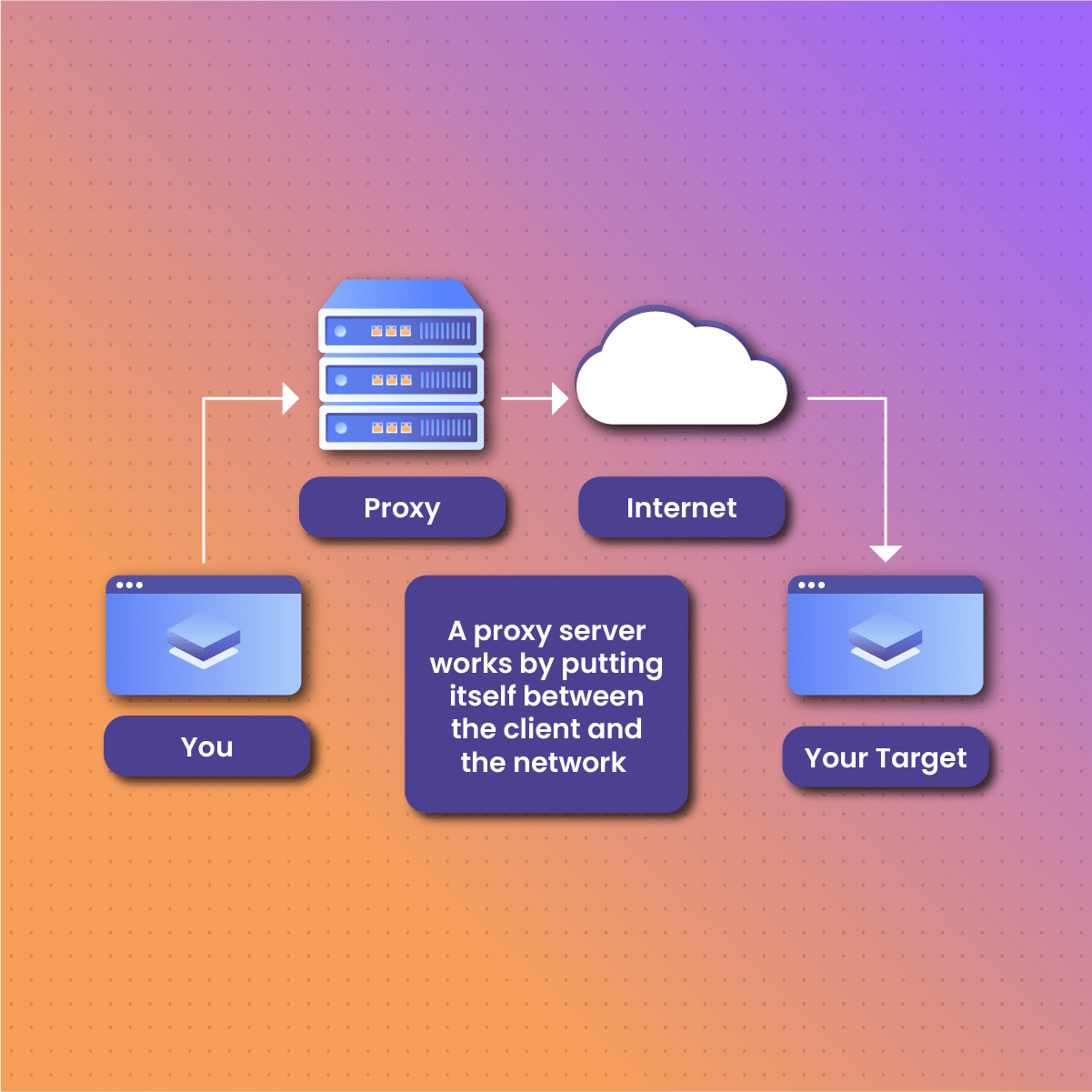
When an individual uses the internet, communication is direct without any form of anonymity and privacy. This essentially makes the user’s device vulnerable to targeted ads and cyberattacks such as malware.
With the introduction of proxies, communication between the end-user and the internet is enhanced by an intermediary – the proxy server. The traffic from the end-user goes through the proxy, filtering potentially harmful data to ensure the user stays secure and anonymous.
Besides enhancing anonymity and security, proxies allow users to bypass geo-blockers and other restrictive firewalls on the internet. Several web applications restrict individuals in locations different from where the application is meant to work from accessing the site. This is done by installing software on the website that detects people’s location from their IP addresses.
When a residential proxy is used, people can route their IP addresses to access several websites without their location being detected and blocked.
Proxies are of different types. Let’s explore them in the section below.
Types of Proxies
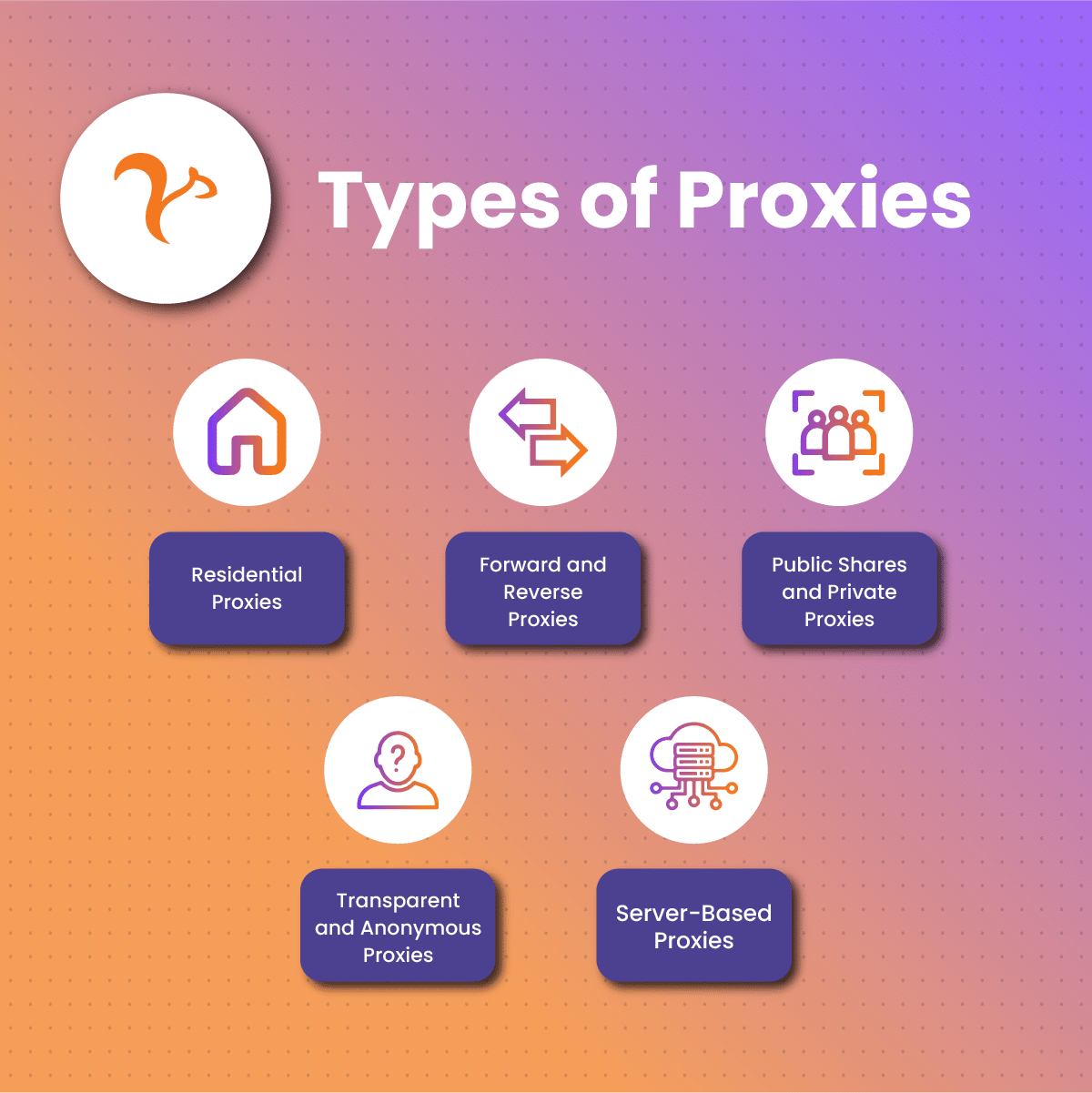
Below, we will explore the common proxy types out there.
Residential Proxy
Residential proxies contain a pool of IP addresses that are directly provided by internet service providers. The proxies are tied to homes and devices across several cities, making it almost impossible to track and block them.
Residential proxies use a rotating system to periodically route an end-user’s assigned IP addresses, enabling them to access several websites and applications, even those with location blockers. This further helps companies conduct activities such as web scraping, SEO research, and global price monitoring.
Residential proxies are pretty expensive compared to the regular ones as the IP addresses need to be bought from internet service providers (ISP proxies).
Two major types of residential proxies exist and they are static and rotation. With static residential proxies, a single IP address is assigned to the end-user. Rotation residential proxies give the end-user access to several IP addresses which are rotated periodically.
Essentially, rotation residential proxies are more expensive than static ones because the periodic routing makes them difficult to spot and block.
Forward and Reverse Proxies
We understand that proxies control data flow between a user and the internet. Based on the direction of data traffic flow, proxies are categorized into forward and reverse proxies.
With forward proxies, the end users mask their identities or set up an alternative IP address to gain access to a website that has a firewall or geo-blocker installed. Essentially forward proxies protect the client during internet activities.
Reverse proxies, on the other hand, help to protect servers. When an end-user makes an online request, it goes through a proxy that works to keep the web server safe.
While these proxies help to keep websites secure and prevent cases of hacking, they play important roles in load balancing. In this case, the proxy enhances even flow of traffic to prevent lagging or slow loading of results.
Public, Shared, and Private Proxies
Based on how an end-user gains access to an IP address, proxies are categorized into public, shared, and private proxies.
Public proxies are regular proxies that anyone can access, provided they have an internet connection. Generally, they can be found online.
Public proxies are usually free and can be used by many clients at the same time. Security is a major problem because moderators are anonymous and it can’t be deduced who has access to an end user’s browsing data. Additionally, they are easily detected by geo-blockers and flagged down.
Shared proxies, on the other hand, are used by a group of close-knit people who divide the fees among themselves. Unlike public ones, shared proxies come at a fee but are not expensive.
Shared proxies are more secure and users have access to customer support in case of a technical glitch. However, efficiency may be slow if all subscribers are signed in at the same time.
Private proxies are often considered dedicated proxies because they are used by just a single person. With private proxies, end users are less concerned about efficiency and security. Issues of lagging and slow loading are unlikely because it’s used by one person.
However, they’re expensive due to the security, efficiency, and reliability they provide.
Transparent and Anonymous Proxy
When proxies direct data flow, they do so using a header. Headers are used in close-knit organizations to monitor users’s (employees in this case) data traffic.
There are three types of proxies based on the header information forwarded by the proxy. They are either transparent, anonymous, or elite proxies.
Transparent proxies are the least anonymous proxies in the market. When an end user makes a search request, their IP address and the type of proxy being used are contained in the data flow.
These proxies don’t protect a user’s privacy. Rather they are used to enhance load balancing by limiting content or caching frequently visited websites.
Anonymous proxies conceal users’ identities by not including their IP addresses in the forward header. However, the requested information is still being relayed.
Anonymous proxies are common and are ideal for web activities such as data scraping, online gaming, price monitoring, and other activities that involve IP address rotation.
Finally, elite proxies direct secure traffic flow and prioritize the end-user’s anonymity. It does this by providing fake information or concealing the user’s real IP address. This makes it difficult for software to know if an IP address is tied to a proxy.
Server-Based Proxies
Besides those listed above, other proxies exist and are categorized based on the server. They include the following:
- SOCKS proxies
- HTTP
- HTTPS
- TCP
- FTP
- TOR
- DNS proxies
- Several others
Use Cases of Proxy Servers
Proxy servers have vast uses. Below, we’ll explore popular use cases of proxy servers.
-
Enhanced Anonymity
When an end-user interacts with the internet, the transfer of data isn’t direct. Rather, it goes to the proxy, masking the client’s IP address and keeping them anonymous. Websites wouldn’t leverage a client’s browsing history and data preferences, to show them targeted ads.
-
Data Scraping
This is the process of collecting large amounts of data from online sources. The process is complex and chances of IP addresses being blocked are high. However, rotation residential proxies allow clients to access any web page to scrape data interrupted.
-
Bypassing Geo-blockers
Several web pages and applications have unique IP identifiers, allowing only residents of a particular location to access their sites. With a proxy, end-users can access these applications without being in the required location. This is one of the most used cases of proxy servers.
-
Network testing
Cybersecurity analysts can use proxies to access the vulnerability of an online protocol. By accessing how and which proxies gain access to their sites, they can build unique proxies to safeguard and control their platforms. This restricts who has access to the site and how much time is spent there.
-
Professional Marketing
Strategies such as search engine optimization (SEO), social media management, and analytics are necessary for business growth and development. Managing multiple accounts, conducting keyword research, and analyzing them at the same time is difficult. But with proxies, joggling different accounts simultaneously is possible.
- Other use cases of proxies include:
- Online gaming
- Caching and load balancing
- Global price monitoring
Buy a Proxy – Factors to Consider
Proxies are vastly used in today’s digital space. We’ve explored the types and use cases of proxies. Unarguably, they go a long way to enhance anonymity and security and bypass web restrictions.
Several factors must be considered before investing in a proxy. Some of these factors are explored below.
-
Desired goals
Proxies are vast based on their functionality. You should know what you want to use a proxy for before choosing one. If you want to scrape data from the internet or monitor global prices, a rotation residential proxy could come in handy.
For activities that require you to bypass firewalls and access stuff like online video games, you will likely go for a SOCKS5 proxy. For enhanced anonymity and security, a dedicated proxy will serve you better. Ensure the proxy you choose aligns with your desired goals.
-
Technical support availability
Setting up and managing a proxy is a technical process. You may want to check if a company has a technical support team you can speak to at all times concerning the proxy. Some proxy service providers offer free trials while others do not. This way, you can see if it gives you the desired result.
-
Budget
The market value of proxies varies and your budget is an essential factor to consider when shopping for one. You can always get the best deals that align with your budget. However, quality should not be compromised
-
Provider’s IP pools
Knowing the number of IP pools a service provider has is important, especially if you plan to buy a rotation residential proxy or country-specific ones such as U.S. residential proxies. You have a greater chance of staying anonymous if a provider’s IP pool is vast. Some service providers boast over 52 million residential IP addresses in their pools, making them an ideal choice.
-
Reputation of the provider
Evaluating a proxy provider’s track record is important before patronage. But how would you do this?
The easiest way out is to check Trustpilot or the provider’s website for testimonials from those who have used the proxy before. This helps in making rational decisions.
Buy a Proxy – What are the Required Steps?
After selecting a provider, it’s time to purchase your desired proxy. Let’s highlight the steps below.
-
Set up an account with the provider
You may need to set up an account before purchasing a proxy. Once done you should have a dashboard that’s unique to you and can control your proxy’s activity. An email address or password may just be sufficient information to create an account.
-
Choosing a proxy plan
Providers have a range of proxy plans. It could be monthly, quarterly, or yearly subscriptions. All you need to do is to choose a plan that aligns with your budget and goals.
-
Read the terms and select a payment option
Reading the terms and conditions of service is essential. It lets you know about your privacy, possible data the provider may have about you, and best practices for using the proxy.
Once you consent to the terms, choosing a payment option follows. Card payments are the most common method. However, some providers accept Google and Apple Pay, or even cryptocurrencies such as Bitcoin, Ethereum, or stablecoins.
-
Instructions for configuration
Once payment is confirmed, you’ll have access to your proxy and supporting information such as IP address, port number, and authentication.
The provider will also provide you with step-by-step instructions on how to set up your proxy. Once installed, your online privacy is automatically enhanced and you will have access to sites with firewalls and geo-blockers.
Wrap Up
Proxies are essential in this digital dispensation, enhancing privacy and anonymity and facilitating access to restricted web content.
Several factors must be considered before you buy a proxy. These range from your budget, desired goals, technical support, and reputation of the provider.
We started this article by exploring the concept of proxies, their types, and possible use cases. We concluded by exploring the required steps to buy a proxy.
Frequently Asked Questions (FAQs)
Can I ask for a refund after purchasing a proxy?
Asking for a refund is dicey as most providers do not offer refund services. However, to be sure a proxy is good for you, leverage the free trials to see how well it works. You can opt out of the subscription once the free trial is over.
I need a proxy but don’t have any money. What can I do?
The best proxies in the market aren’t free. Dedicated and rotation residential proxies are the most expensive. However, public proxies are free and you can connect to them provided you have internet access. But note that you will be compromising on security and anonymity.
Can I unsubscribe from a proxy at any time?
Yes, you can unsubscribe from a proxy server at any time. Note that if it’s a paid service, you will not get a refund. However, it’s ideal to wait till your subscription expires.






