A Comprehensive Guide to Understanding Anonymous Proxies
Proxies are indelibly crucial to maintaining web privacy. Like a middle-man in a trade, they ensure a significant level of anonymity on the Internet. From prevention of identity theft, risk exposure, and online security, they are a sure bet to shielding your information online. Nonetheless, proxies exist in different types and not all can provide the level of anonymity you may need. This is where an anonymous proxy comes into play.
This is why it is advisable to get acquainted with the various types of proxies and their varying degrees to which they keep you out of sight and let you enjoy your time on the internet.
In this article, we will explore the details of anonymous proxies; their definition, functions, types, use cases, common pitfalls, as well as frequently asked questions and answers. Fasten your belts and let’s get right on to it!
What is an Anonymous Proxy?
An anonymous proxy simply refers to any type of proxy that focuses solely on keeping the activities of its users anonymous. By routing the user’s internet traffic through the proxy server, it masks the original IP address, making it appear as though the traffic originates from the proxy server’s IP. This provides a layer of privacy and anonymity, preventing websites and online services from tracking the user’s true location and identity.
The proxy server mediates the interaction between your device and the web the exact way a forward proxy does. However, anonymous proxies interact with the web in your interest by ensuring to conceal your device IP address and replace it with the proxy server. This way, your online-based activities cannot be linked directly to you as the proxy’s IP is what is displayed.
An anonymous proxy is more often than not, utilized by people or firms that aim to guard their user privacy and anonymity when surfing the web. Its major strength lies in its ability to grant you access to geographically limited content masking your IP location with theirs to make it seem like you are in the officially permitted zone.
Proxies such as residential proxies (whether rotating or static), ISP proxies, mobile proxies, or U.S. residential proxies can offer anonymity. It just depends on the client’s preference and the service provider’s package.
How do Anonymous Proxies Work?
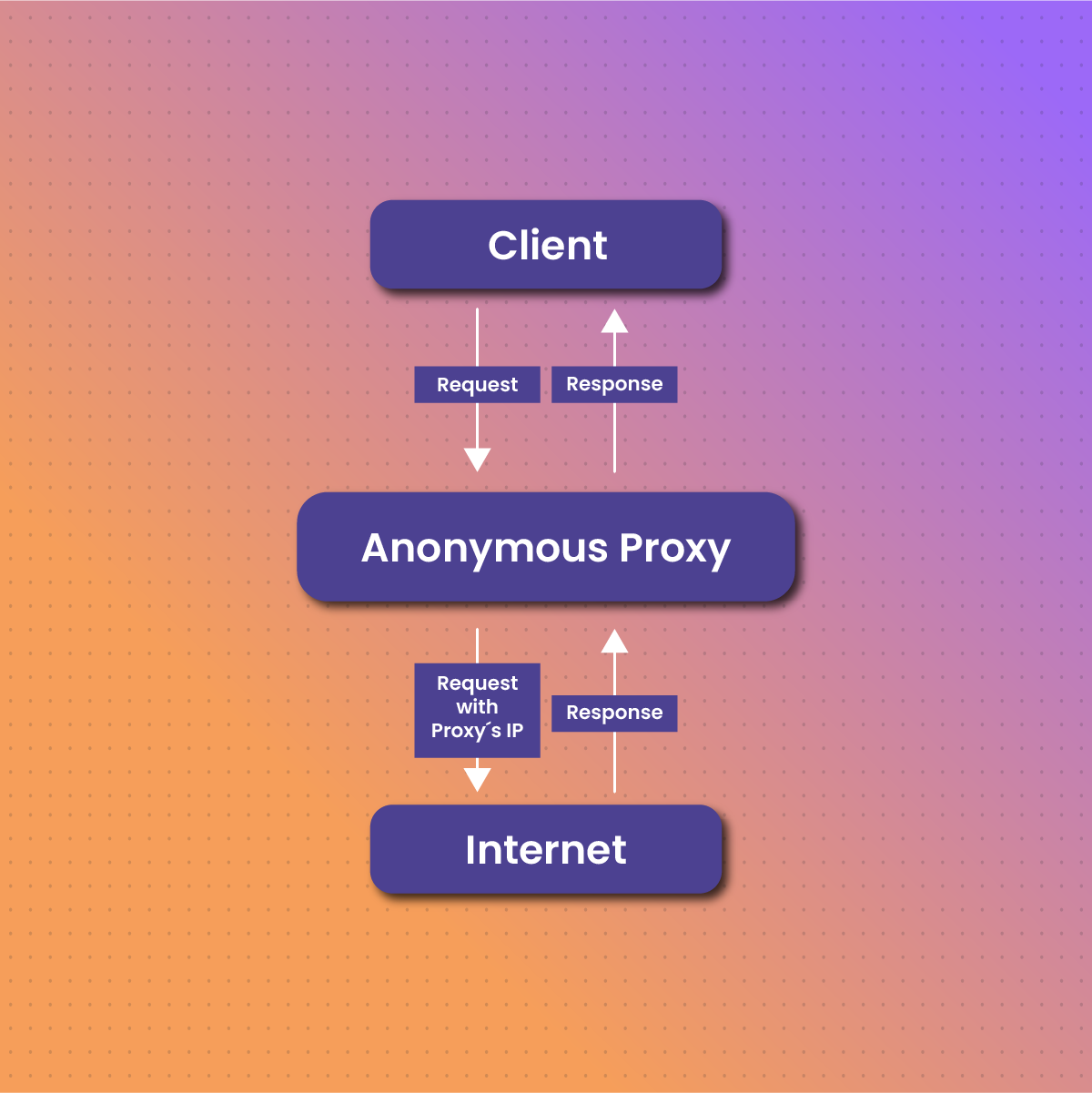
Anonymous proxies work by intercepting the user’s internet requests and forwarding them to the destination server on behalf of the user. When a user connects to a website through an anonymous proxy, the website only sees the IP address of the proxy server and not the user’s actual IP address. This process involves the proxy server receiving the user’s request, masking the original IP address, and sending the request to the target website. The website’s response is then relayed back through the proxy server to the user, maintaining anonymity throughout the process.
Anonymous proxies hide their user’s original identity by altering the network traffic as well as the hypertext transfer protocol caption. Although this procedure may sound a bit complicated, it is effortless and requires little to no extra configuration from the user.
The major procedures adopted by an anonymous proxy in effectively performing its functions are outlined in five (5) bullet points below:
- Once a user launches a request from their device seeking entry to a particular website or access to its specific content, the request is first transmitted initially to the proxy server, in this case, the anonymous proxy server. Like other requests, this request will contain the user’s details like their unique IP address, a chosen uniform resource locator (URL), and other relevant captions that could help to identify the user.
- The anonymous proxy server whose configuration has been made to effectively transmit and anonymize the user’s information then receives the request and immediately gets to work. It detaches all of the user’s identifiable data from the transmitted request, including the user’s IP address. This procedure is fundamental to bolstering the user’s anonymity.
- Afterward, the proxy quickly moves on to replace all detached information with its server-generated information. It conceals the user’s IP and replaces it with another IP address that is connected to the proxy’s server.
- Thereafter, the altered request is transmitted across the server to the specific website that the user desires to gain access to. The receiving server will then interpret this request to be directly from the proxy, without recognizing the existence of the user as the originator or source of the request.
- Finally, the receiving website transmits the feedback for the request. As soon as the anonymous proxy detects feedback sent from across it, it once again engages in crucial tasks like data caching and filtering before further transmitting the information from the website to the user.
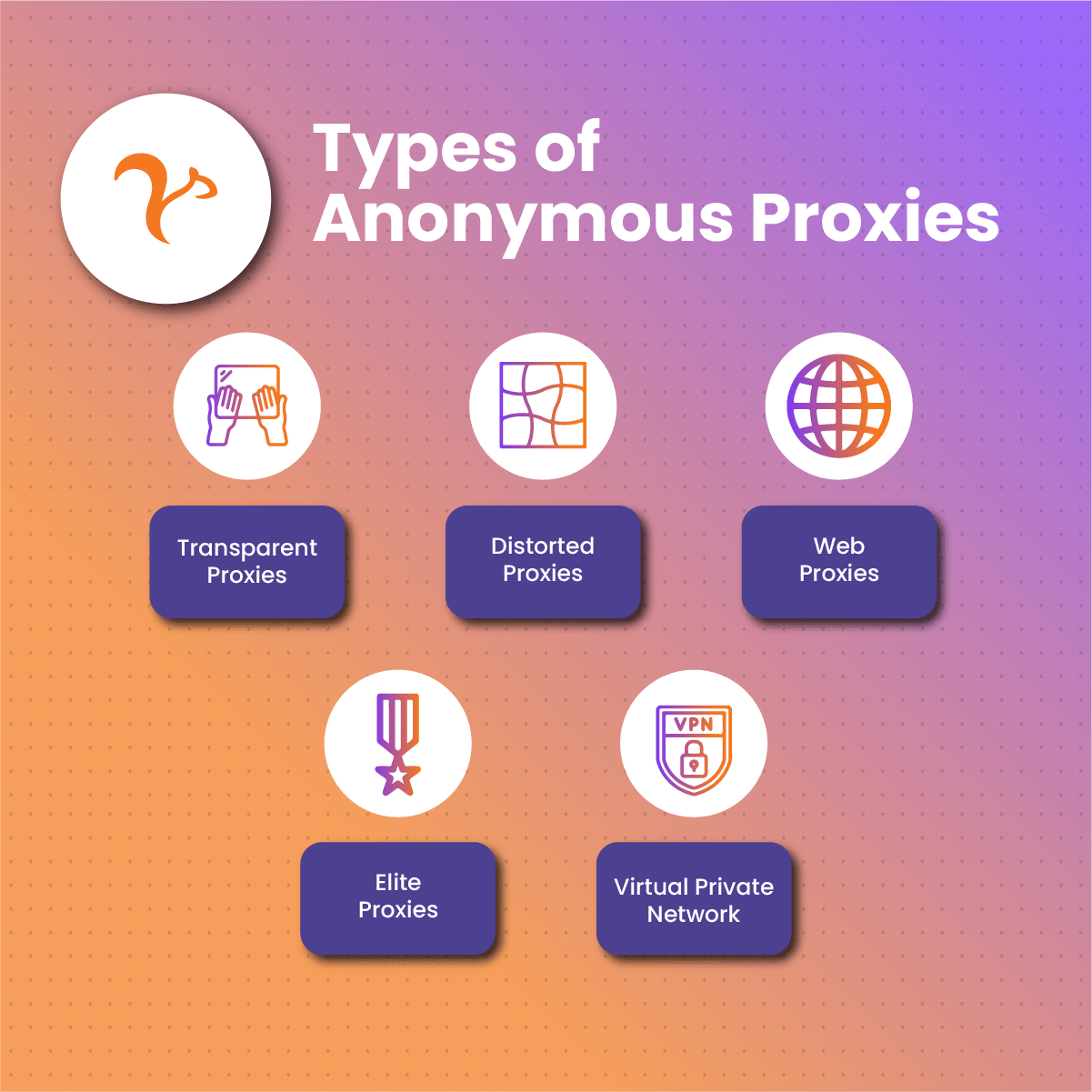
Types of Anonymous Proxies
Various types of anonymous proxies exist, all of which are classified according to the degree to which they can carry out their basic anonymity function. Some examples of them include;
Transparent Proxies
These kinds of proxies function as a mediator server between a client and sites on the internet. While they can transmit requests sent from the users or clients to a target website, they usually do so without concealing the client’s IP address from the target site server, earning them the name “transparent”. Transparent proxies do not attempt to alter the data that passes through them and they are very helpful in caching information.
Distorted Proxies
Unlike transparent proxies, a distorted proxy offers a much more limited degree of anonymity. They do these by shielding the client’s IP address and displaying its proxy server-linked IP as the original IP for the request being transmitted through them. With distorted proxies, the target websites cannot access the client’s original IP address but are still aware that a proxy is being used for the interaction.
Web Proxies
A web proxy is a type of proxy that is connected directly to an internet browser and requires no extra package setup or configuration to function. Clients who use web proxies are often required to open the search bar of the browser and enter a target website uniform resource locator (URL). The web proxy then helps to directly function as a mediator for the client and target website interaction. While a web proxy is easy to use, they have vast limitations in terms of operational capacity and may not fully be compatible to use when accessing some websites.
Elite Proxies
These are the categories of proxies that exhibit the initiative to provide a sufficient level of anonymity to their clients. You may ask how. Thecanto fully conceals a client’s IP address and easily replaces it with another to make the targeted website believe that the proxy server is the sole source of the request being transmitted. While the target website server is unaware of the existence of the client, it also cannot identify the use of a proxy. Elite proxies offer significantly increased anonymous features which makes them perfect for clients who usually handle sensitive data. With this type of proxy, the client’s original IP and their activities are fully private.
Virtual Private Network
Although a VPN in itself is not a proxy, it provides an excellent anonymous internet surfing experience with an assured secure connection. VPNs are configured to encode a client’s web traffic while it transmits it across to its destination. Also, they securely conceal your IP address for increased levels of privacy and help you obtain access to geo-restricted spaces on the internet.
Use Cases of Anonymous Proxies
Anonymous proxies offer several benefits, including enhanced privacy and security by masking the user’s IP address and preventing websites from tracking their online activities. They help bypass geo-restrictions, allowing users to access content that may be blocked in their region. Anonymous proxies also protect against cyber threats by concealing the user’s true IP address, reducing the risk of targeted attacks. Additionally, they can be used to avoid IP bans and restrictions, enabling users to engage in activities like web scraping or managing multiple accounts without detection. These advantages make anonymous proxies a valuable tool for maintaining online privacy and security.
Amongst a plethora of user- benefits of anonymous proxies, the ability to conceal IP addresses has made them invaluable for numerous functions. Some of these include:
Privacy maintenance
The online space does not possess the level of privacy that one may expect of it. However, the use of anonymous proxies can help to an extent provide a sense of user privacy. As it conceals your IP address, it takes you a step further from certain online intruders who may be looking for ways to intrude into your space.
Bypassing Geographical Internet Restrictions
One major reason why people opt to hide their IPs; utilizing either proxies, VPN, or TOR is to prevent information censoring or restriction. Because the internet is home to endless streams of content and information, some of this content is sometimes geo-restricted. This means people outside a specific geographical location are unable to access that content. However, Anonymous proxies can help conceal your personal IP geolocation and tag a new IP to your access requests, making it easy to boycott these restrictions. This makes them suitable for activities such as global price monitoring, SEO optimization, and online gaming.
Data Scraping Activities
Anonymous proxies are also employed to automatically extract data from the web. By employing numerous series of these types of proxies, you can easily circulate requests using proxy-generated IPs to carry on data scraping and other tasks while at the same time ensuring that these websites are unable to identify and restrict you.
Increasing the Level of Online Security
When you interact with the internet through an anonymous proxy, your requests are initially transmitted to the proxy server that serves as an intermediary for your device on the web. What this simply suggests is that you have an added layer of security on the web space as the server proxy will make sure to filter feedback data before they are sent and equally transmitted back to you.
Common Pitfalls of an Anonymous Proxy
Anonymous proxies are indeed vital to curbing certain issues we face when surfing the net. Regardless, like most things that have an advantage, it is bound to experience a setback from one or two factors. Below are some of the common pitfalls of utilizing an anonymous proxy.
Limited Speed
Since proxy servers stand in between your device and the online web, mediation is most likely to weaken the speed at which your internet network functions. Your network speed might slow down when compared to how it would function in the absence of a proxy.
Limited Dependability
Of course, anonymous proxies are extremely useful in maintaining anonymity, and increasing privacy levels. But on the other hand, not all anonymous proxies can efficiently function as expected. For instance, free anonymous proxies can offer limited experiences like slow connections, which may result in occasional disconnections. In such cases, your proxy will not always be available to mediate and keep your IP fully private when you surf the internet.
Security Risks
The use of anonymous proxies often increases our online security to a certain level. However, the process of obtaining these proxies sometimes from unreliable sources may inadvertently expose you to security risks. This is because proxy servers from unknown sources can observe your online activities and record some of your sensitive data. This is why you need to obtain your proxies from only reputable sources.
Absence of Encryption
Anonymous proxies also assist in concealing your IP address from being displayed on the web. While they perform this function, they do not employ encryption protocol while transmitting traffic. This implies that your data is transmitted in plain language that a hacker would understand if there is ever an incident where they intercept your network traffic. If you aim for better security and encryption of your network traffic, you may want to opt for a VPN rather than an anonymous proxy.’
Final Thoughts on Anonymous Proxies
It is important to note that anonymous proxies help in achieving a significant level of privacy and security on the internet, while still enjoying the benefits of its set-up. And while they are a great addition, not all of them can offer a desirable level of anonymity. This is why we sought to give a detailed guide to understanding them with some factors to consider before getting an anonymous proxy setup for your device.
Frequently Asked Questions and Answers
Is an anonymous proxy foolproof to ensure internet privacy?
Anonymous proxies are reasonably helpful in improving your internet privacy as they shield your original ISP-assigned IP address from being visible on the web but it does not guarantee a foolproof privacy experience. This is because other factors can threaten your security or privacy on the internet. You may want to know how secure your internet connection is, as well as the online sites you usually explore. Also, your proxy can significantly pose a risk to your privacy in cases where intruders attempt to tamper with it.
Are anonymous proxies more efficient than VPNs?
Both anonymous proxies and VPNs perform similar functions of masking your IP address with their server’s IP and they both have their relative downsides. However, as compared to a proxy, VPN intermediary processes between your device and the internet are more complicated and secure. This is because VPN encrypts your data in such a way that even an attacker intercepting your network will not successfully get a hold of your information.
How does a transparent proxy relate to an anonymous proxy?
Transparent proxies function as an intermediary between a client end and the internet, and so does an anonymous proxy and any other proxy. The major difference is that a transparent proxy will not conceal your IP address like an anonymous proxy would do to keep your data private.