A 2023 study on the state of Bot Mitigation, it was discovered that about 83% of businesses complained that bad bots are very sophisticated, get past security measures, and only around 15% of these intruding bots get caught by their bot mitigation techniques, and even at that, these measures only last for about a year before the bots find a way around it.
Visiting a website can look straightforward to the average user, but catchy colors and buttons underneath those texts are complex codes and hidden elements. Bots make up part of these unseen substructures that a website runs with. Some of these bots are bad, while some are good.
We will discuss some aspects of bots, why they can pose a threat, and some bot mitigation techniques you can use to detect and fix your bot problems.
What Does Bots And Botnets Mean?
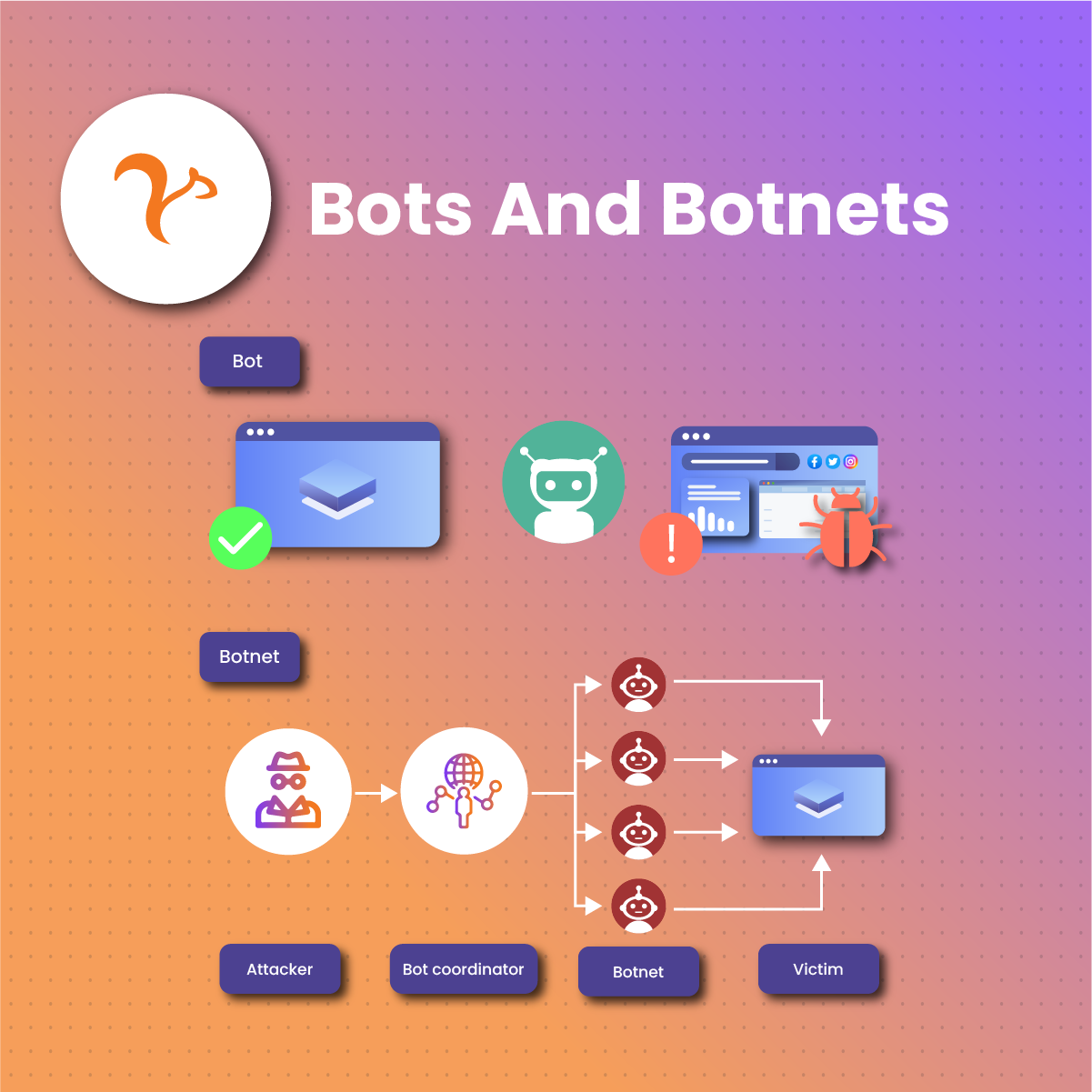
A bot is a software application that carries out different kinds of automated activities on the internet. Although the name may come off as some simple stuff, bots perform tasks that humans cannot. A bot is a tool whose use and benefits are tied to the assigned task or activity. Search engine crawlers, for instance, are examples of good bots. But a bot in the hands of a malicious attacker can be disastrous.
So, a bot can either be good or bad, depending on who uses it and for what purposes. Further in this article, we will explain the differences between harmful and beneficial bots, how to detect them, and the best bot mitigation techniques to adopt.
Before we explain the different types of bots, note that a botnet simply refers to a network of bots. In other words, several computers are interconnected to carry out specific tasks repetitively.
A 2020 study revealed that almost half of all web traffic came from bots.
Types Of Bots
This section is essential because many people have a negative mindset towards bots. Different kinds of bots serve excellent and bad purposes, as we will see soon. If you often use the internet, you must occasionally encounter the following types of bots.
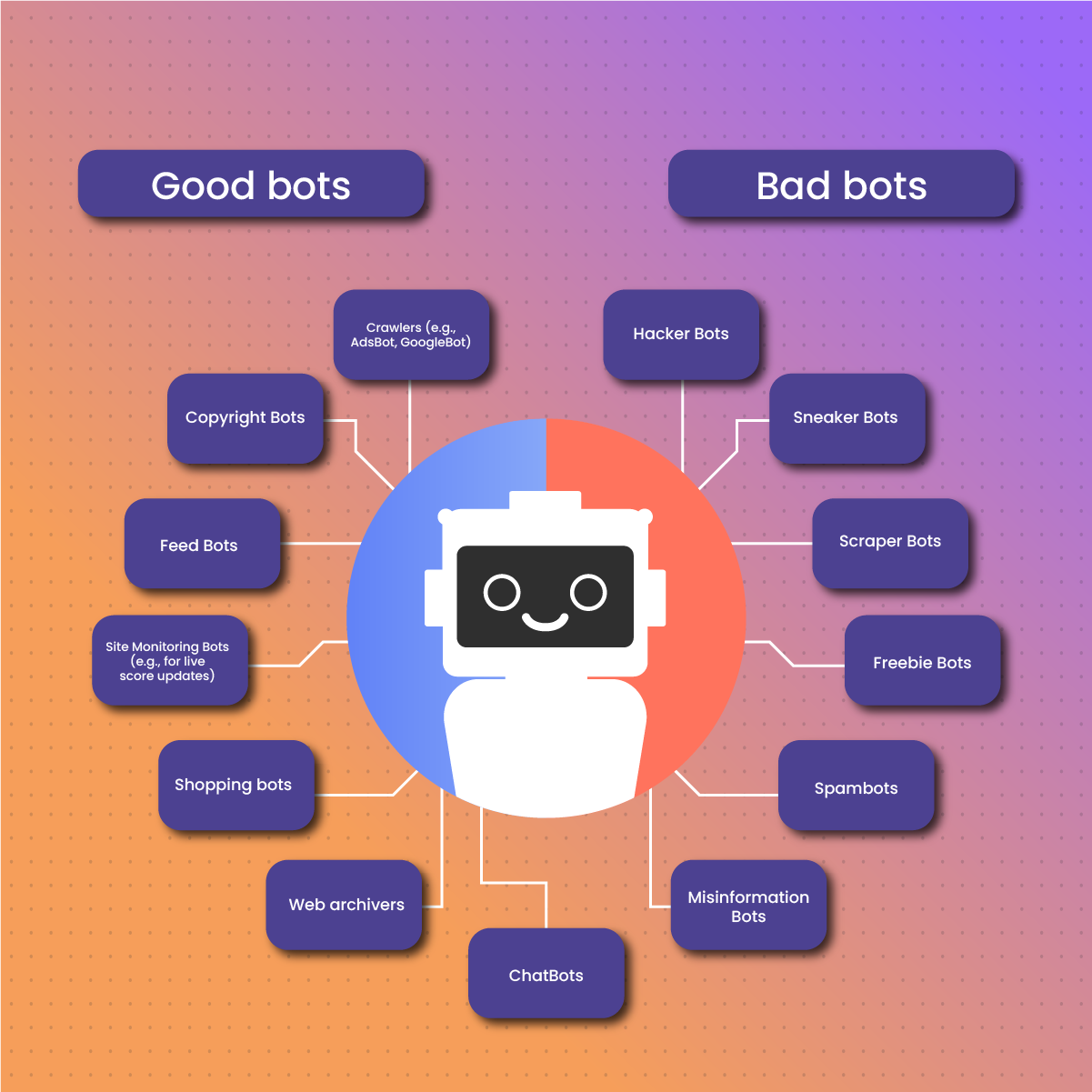
Good Bots
As the name suggests, these are valuable bots and carry out various essential tasks. These kinds of bots are safe to be permitted on your website.
Some examples of good bots are discussed below.
Crawlers
These are often called spider or robot bots. They are used to automatically obtain a website’s content by simply following a web link or URL. Some popular crawler bots are those by Google, such as AdsBot, StoreBot, GoogleBot, Googlebot News, etc.
Copyright Bots
Copyright bots crawl different sites and platforms for content that infringes on the established copyright laws of a geographical location or state.
Feed Bots
These types of content are used to scout through the internet, gathering as much news as possible. Social media networks and aggregators primarily use them to populate their platforms.
Site Monitoring Bots
If you are used to live score updates on football matches, you will realize that websites that cover the sport always have real-time live score updates from ongoing matches. These are the works of monitoring bots. They monitor metrics like page speed or uptime, among other activities.
Other good bots include:
- Shopping bots,
- Web archivers
- ChatBots, etc.
Bad Bots
To malicious people with bad intentions, bots can cause great havoc, from personal finances to state and nationwide elections. Over the years, most bot mitigation techniques have stopped working or become less effective. Attackers are developing more fierce ways to beat bot mitigation techniques and security measures.
Some bot communities even provide resources to these attackers to collaborate and create better ways to make bots unbeatable. Today, static measures like digital fingerprinting, IP blocking, or the use of CAPTCHAs barely stand up to the sophistication of modern bots.
The following are some examples of bad bots.
Hacker Bots
As their name suggests, hacker bots hack. They deceive people, attack websites, and introduce malware. They often achieve this by finding their way into the personal computers of unsuspecting victims with an exposed or weak security system. They then insert a line of code that breaches the computer or network. Most hacker bots are used for financial crimes, leaving the victims to pay a hefty sum to get the bot off their system.
Sneaker Bots
These bots were designed to discover the latest limited sneaker editions with a speed no human can match. As they can scan the internet, they also flood the target website with requests, creating an unfair advantage to the bot owner over real people. These bots now resell the sold-out goods at a high price. The use of sneaker bots is widespread in the e-commerce market. Botters buy products with high demand but limited quantity to resell at a higher price and make massive gains.
Scraper Bots
Don’t get it mixed up. Scraping bots are good but can also be used for malicious purposes. Attackers are fond of turning around good tools to serve their selfish needs. Fraudsters use scraper bots to steal data from websites and create counterfeit sites to deceive naive web visitors.
Freebie Bots
These bots are made from a blend of sneaker and scraper bots. They are often used to take advantage of the errors of online businesses. Freebie bots monitor websites to find products that have the wrong prices. When they find such products, they checkout at the speed of light before the seller realizes the price error. Freebie bots can lead to poor user experience, revenue losses, and increased cost of operation.
Spambots
This is a popular bot we are familiar with. They are used to send fake comments all over social media, promising ridiculous offers to lure victims to a phishing website.
Misinformation Bots
These bots influence public opinion and post politically controversial content on social media. Most times, misinformation bots carry wrong information backed by ulterior political agendas. These bots often compromise the free and fair democratic processes by injecting false information into the mainstream media.
What Are Bot Mitigation Techniques?
Bot mitigation techniques are solutions businesses or websites adopt to detect and prevent lousy bot activities on their website or platforms. For bot mitigation techniques to be failproof, they must leverage machine learning and artificial intelligence for continuous learning to keep pace with the ever-evolving landscape of bot attacks.
Why Should Businesses Use Bot Mitigation Techniques?
If you have a business online and get a decent amount of traffic, chances are bad bots will come for you. They will flood your website and strain your infrastructure, which may lead to slow site performance, making you spend more to increase your site’s speed without sacrificing resources. The destructive nature of bots on your site begins when your site efficiency is drastically reduced. A targeted bot attack on your website can ruin your reputation, lead to financial loss, and minimize customer trust.
Some malicious bots fill login fields with shady details as cybercriminals try to get access to your users’ accounts by all means. Others even make purchases using fake or stolen credit cards to bookmark active future accounts to perpetrate fraud.
Also, bad bots can scrape off intellectual properties and product information to gain an upper hand in the industry.
It messes up your business analytics when you need help differentiating between bot activities and human traffic. Wrong analytics can lead to miscalculated trends that can cost you much money to recover from. Effective bot mitigation techniques help prevent bots from introducing these adverse effects that traumatize your business.
Bot mitigation techniques try to fix a whole class of threats that often lead to significant business loss.
How Does Bot Mitigation Techniques Work?
Bot mitigation techniques go through these three steps to quell the activities of bad bots.
Bot Traffic Identification
This is the first step of bot mitigation techniques employed before applying the required measures. They cannot work effectively if the bots evade them. Bot mitigation techniques must differentiate between a bot and a non-bot web traffic.
Bot Nature Assessment
This is where bot mitigation techniques separate good bots from bad bots. This step is crucial because flagging a good bot as bad can lead to several issues depending on the specific blocklisted bot.
Harmful Bot Blocking
This is bot mitigation techniques’ last phase. This is the stage where bot mitigation techniques stop bad bots from gaining access to your site and causing damage. This process must be revisited occasionally as bot owners often upgrade their techniques with the latest bot mitigation techniques and evasion tools.
Explaining Some Bot Mitigation Techniques
There are several bot mitigation techniques. They are often grouped depending on the kind of attack you usually face. To ensure long-lasting safety against bots, upgrade your channels to be too expensive for an attack.
Note that botters are moved by money. If you can remove this source of motivation from them by making any attack too expensive, they will move on to other less costly sites.
Here are some bot mitigation techniques you can adopt for your business.
Fake Data
These bot mitigation techniques are excellent ways to waste attackers’ time. If you identify a bot in your computer, you can start supplying them with fake data, making them think their attack is in effect. When the botter realizes at the end of the attack that what he got is useless and he has just wasted time and money, he may not want to relaunch an attack on your system as there is a likelihood they’re going to end up with fake data.
Invisible Challenge
Successful bot mitigation techniques will go unnoticed by real people rather than create friction for clients with solutions that are more difficult for people than bots. Your techniques should only be shown to bots and be extremely expensive to complete, squandering attackers’ resources by making their bots answer increasingly more complex difficulties.
Rate Limiting
These bot mitigation techniques restrict how frequently a bot or user can carry out specific tasks within a specified timeframe. These bot mitigation techniques help to forestall bot activities such as multiple login attempts. However, this method is not foolproof. More sophisticated bots can now mimic human behavior and mask under IP addresses or proxies to avoid being detected.
Static Approach
These bot mitigation techniques involve the use of static analysis tools to identify header information and web requests that match that of bad bots. This is a passive way to detect bot activity and initiate a blocking protocol. This is more of a bot detection mechanism than a bot mitigation technique. However, there would be no need for bot mitigation techniques if the static approach is successful.
Behavioral Approach
These kinds of bot mitigation techniques monitor the behavioral signature of every visitor and check if they are what they claim. Behavioral bot mitigation techniques create a standard of acceptable natural behavior for user agents like Chrome and keep checking if the current user deviates from this expected behavior. In other cases, past behavioral signatures of bad bots can be compared with those of existing users to identify which is a bot. Again, this is more like a bot detection mechanism than a mitigation technique, but we have it here because if this is done well, there may be no reason for bot mitigation techniques. Why troubleshoot when there are no problems?
Web Application Firewall (WAF)
Bot mitigation techniques that use the WAF system can fill up vulnerabilities and block bot traffic from unfamiliar user agents, whole countries, and IPs. However, WAF does not have the technology to detect sophisticated botters that mimic human behaviors. WAF bot mitigation techniques must be maintained daily to keep up with the ever-evolving landscape of botters, or else they will always stay caught up after much damage has been done. This means you must use specialized software alongside WAF for better performance.
Multi-Factor Authentication (MFA)
The MFA is one of the most sophisticated bot mitigation techniques. MFA introduces an extra layer that makes the attack process difficult for botters. However, the choice of activating MFA is entirely up to the user. Telling users to activate MFA on every site they have a profile on can be challenging. Most users think that this is something other than a reliable bot mitigation technique.
Deploy CAPTCHA
This is one of the most common bot mitigation techniques today. It uses a challenge-based technique to detect humans and bots. Although big companies like Forbes have praised CAPTCHA for reducing bot activities by 88%, several companies stopped using it because it often fails.
On the bright side, the latest Captcha v3 from Google has introduced the idea of risk scores, which means rejecting or accepting traffic won’t be solely based on the result of a challenge.
Bot Mitigation Techniques FAQ
Can Residential Proxies Pass As Part Of Bot Mitigation Techniques?
A residential proxy is a network of linked IPs that masks a user’s IP address, enhances their online privacy and anonymity, and provides some form of security and speed to their overall browsing experience. Using residential proxies from trusted companies like NetNut, you can enjoy protection from scam ads, spam bots, malicious bots, and other threats, and so can pass off as part of bot mitigation techniques. Even if you mistakenly install malicious software, residential, ISP, or static proxies, NetNut can detect these bad bots and alert you before the installation begins.
What Are The Best Bot Mitigation Techniques?
The bot mitigation techniques must have several layers of protection like WAF, MFA, bot mitigation software, etc. They must also be updated regularly to keep up with the latest tech and industry trends and standards.
In most cases, the best bot mitigation techniques to adopt for your business will depend on the threats you usually face. Contacting a bot mitigation company is also an excellent way to pool resources to specific threat areas rather than randomly trying different bot mitigation techniques.
Do Bots Have Any Legal Implications?
Although bad bots are illegal because of their exploitative tendencies on the internet, their nefarious activities have raised concerns for good bots, the thriving concern being that they are capable of subtle deception.
A typical example is when customers interact with live chat agents who many think are humans but are indeed bots. This act in itself is deceptive.
Final Thoughts On Bot Mitigation Techniques
As we conclude this article, we cannot fail to reiterate the adverse effects bots can have on your website and business, that is, bad bots. The bot mitigation techniques discussed above give us an overview of how to handle these malicious hackers.
As repeatedly mentioned, not all of these bot mitigation techniques are foolproof, so ensure you regularly use the expert services of a bot mitigation company or keep your techniques up-to-date with current trends.
NetNut offers a robust proxy service that can be a great way to combat bad bots. We have seen how effective residential and other proxies can be to prevent bot attacks. You should use our proxy service to gain access to fully comprehensive and accurate data, with no IP blocks.