Introduction
It is no longer news that safeguarding online activities and ensuring privacy has become a paramount concern for individuals and businesses. One effective measure to enhance online security, especially for Linux users, is configuring proxy in Linux.
Linux, being an open-source operating system renowned for its robustness and security features, is a preferred choice for many users. However, users can benefit significantly from configuring proxy in Linux. Whether for personal use or within a corporate network, configuring proxy ensures a heightened level of security and control over internet traffic on your linux device
In this article, we will explore the step-by-step process of configuring proxy in Linux.
What To Know About Configuring Proxy in Linux
On matters of cybersecurity, configuring proxies on your Linux device is an indispensable tool for fortifying online security. A proxy is an intermediary server that acts as a gateway between a user’s device and the internet. The primary function of a proxy is to relay user requests and responses, effectively acting as a shield that adds layers of security and privacy to online activities.
However, before configuring a proxy on your Linux device, it is important to understand the type of proxy suitable for your device. There are different types of proxies available, each with its unique functionality. Let’s consider these proxies suitable for configuring proxy in Linux:
Different Types of Proxies Available for Linux Users
Linux users have the advantage of choosing from various types of proxies, each tailored to aid configuring proxy in Linux. Understanding these different types is crucial for selecting the most suitable proxy for Linux. Here are three common types of proxies available for configuring proxy in Linux:
- Web Proxies: Web proxies are designed primarily for handling HTTP proxy traffic. They act as intermediaries for web requests, making them suitable for users who want to utilize antidetect browser offers and anonymize their web browsing activities. Web proxies are commonly used for accessing blocked websites and preserving user anonymity.
- SOCKS Proxies: SOCKS (Socket Secure) proxies operate at a lower level than web proxies, supporting a broader range of applications and protocols for configuring proxy in Linux. They are versatile and can handle various types of traffic, including email, FTP, and online gaming. SOCKS proxies are preferred when users require a more comprehensive and flexible solution beyond simple web browsing and website scraping.
- Transparent Proxies: Transparent proxies, also known as intercepting or inline proxies, operate without the need for user configuration for proxies in Linux. They intercept and redirect traffic without requiring explicit user settings, making them seamless for users. Transparent proxies are often employed in corporate environments for content filtering and monitoring purposes.
Understanding the distinctions between these proxy types empowers Linux users to make informed decisions before configuring proxy in Linux.
Benefits of Configuring a Proxy in Linux
Configuring a proxy on your Linux device offers several benefits. These include:
- Configuring a proxy in Linux is a proactive step towards safeguarding personal information.
- In addition, it provides a formidable line of defense for users to filter out malicious content, preventing it from reaching the user’s device.
- Configuring a proxy server on your Linux device helps users to effectively bypass IPs with geo-restrictions.
Without doubts, these benefits of configuring proxy in Linux make it a safe and must-have option for all Linux users.
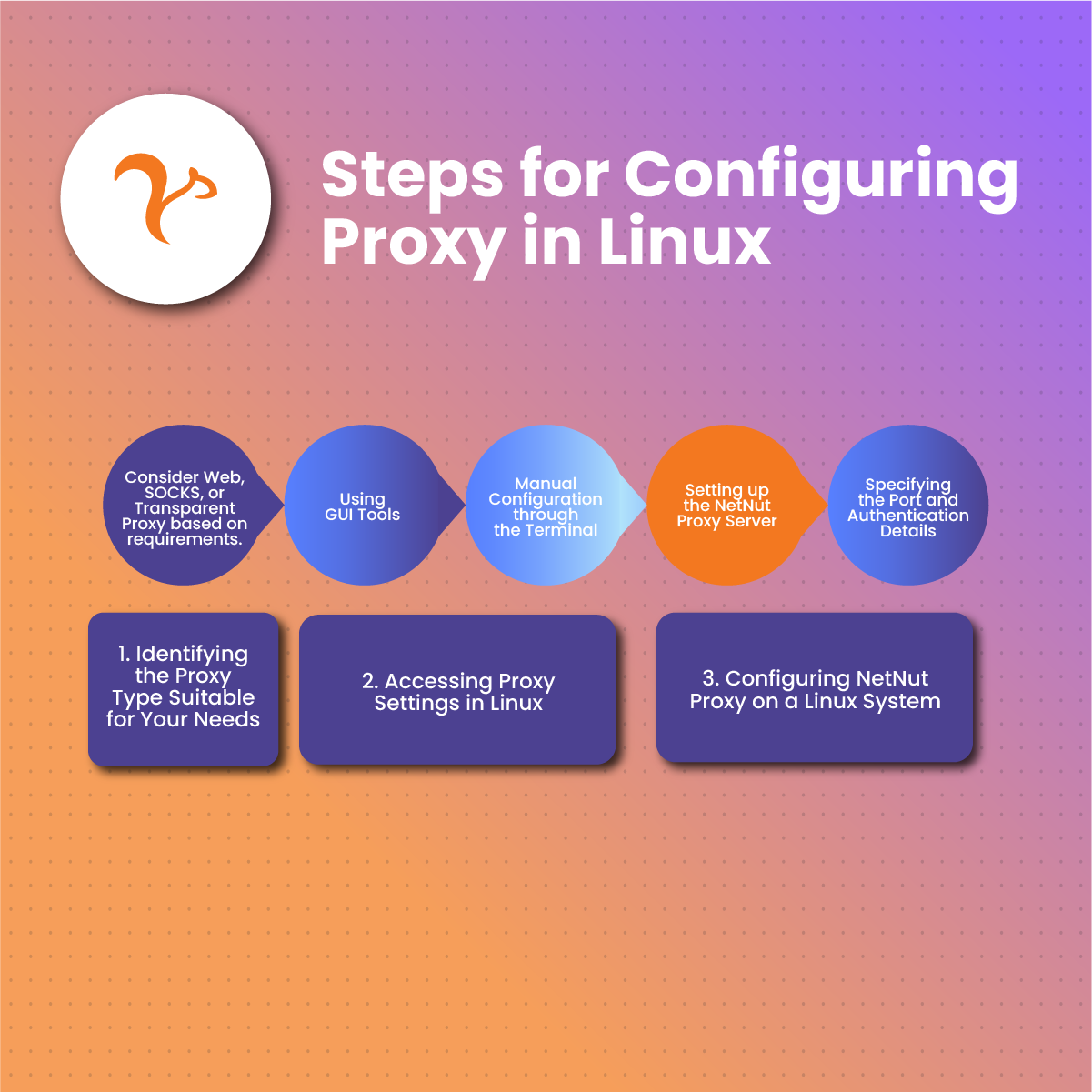
Steps For Configuring Proxy in Linux
Configuring a proxy in Linux involves several steps, and the process may vary slightly depending on your specific Linux distribution and desktop environment. Below are general steps that cover the basics of configuring proxy in Linux:
Identifying the Proxy Type Suitable for Your Needs
Before configuring proxy servers on your Linux device, you need to identify the type of proxy that aligns with your specific requirements. Consider whether a web proxy, SOCKS proxy, or transparent proxy is most suitable based on the intended use and desired features.
Accessing Proxy Settings in Linux
- Using GUI Tools: Linux distributions often provide graphical user interface (GUI) tools for configuring proxy in Linux. Access the system preferences or network settings to locate the proxy configuration options. This user-friendly approach is suitable for those who prefer a visual interface for configuring proxy in Linux.
- Manual Configuration through the Terminal: For users comfortable with the command line, manual configuration through the terminal offers a more hands-on approach for configuring proxy in Linux. Users can use commands to set up the proxy server, port, and authentication if required. This method provides greater control and flexibility for configuring proxy in Linux.
Configuring NetNut Proxy on a Linux System
Final step while configuring proxy in Linux is by integrating with a proxy service provider- NetNut. NetNut stands out by providing users with access to a vast pool of residential IPs. Unlike traditional datacenter IPs, these residential IPs are associated with real devices, adding an unprecedented level of authenticity to the proxy service.
- Setting up the NetNut Proxy Server: Begin configuring proxy in Linux by obtaining the necessary credentials and details from NetNut. Use the provided information to configure the NetNut proxy server on your Linux system. This typically involves specifying the proxy server address and port.
- Specifying the Port and Authentication Details: Once the NetNut proxy server is set up, specify the chosen port and any authentication details if required. This step ensures that your Linux system communicates effectively with the NetNut proxy service.
Configuring proxy in Linux by integrating NetNut proxy service enhances the proxy experience by tapping into the unique features and benefits offered by this service.
Conclusion
Configuring proxy in Linux might seem daunting at first, but with the right guidance, it becomes a straightforward process. By taking this step, you enhance your online security, protect your privacy, and gain more control over your internet experience. Whether you’re a Linux novice or an experienced user, the benefits of using a proxy are well worth the effort.
The importance of configuring proxy in Linux goes beyond basic anonymity; it provides a strong shield against cyber threats, content screening capabilities, and freedom from geo-restrictions. As demonstrated in the step-by-step process of configuring proxy in Linux, users have gained insights into a proxy solution that goes beyond standard options.
Now, users can gain maximum control of their online activities by configuring proxy in Linux. The internet is your oyster, explore it with ease!
Frequently Asked Questions And Answers
How does configuring proxy in Linux enhance security?
Configuring a proxy in Linux enhances security by acting as an intermediary between the user’s device and the internet. It masks the user’s IP address, adding a layer of anonymity, and filters out malicious content, protecting against potential cyber threats. This heightened security is especially beneficial when accessing the internet, particularly on public networks.
Is NetNut compatible with all Linux distributions?
Yes, NetNut proxy service is compatible with a wide range of Linux distributions. Whether you’re using Ubuntu, Fedora, CentOS, or any other popular distribution, NetNut provides seamless integration. Its compatibility ensures that Linux users across various distributions can leverage the benefits of NetNut’s proxy service.
What are the security measures when using NetNut on Linux?
NetNut employs encryption protocols to secure data transmitted between the user’s device and the proxy server. Additionally, users are encouraged to follow best practices for securing their proxy configurations, such as implementing strong authentication and regularly auditing proxy settings.