Introduction
It is no longer news that individuals and business owners make use of the internet for their daily activities. To restrict the level of information available to users, governments have set up a series of internet censorship. Internet censorship refers to the deliberate restriction or control of the content, access, or availability of information on the internet.
This censorship can take various forms, including government-imposed restrictions, institutional filters, and a proxy block by online platforms. While some argue that censorship is necessary for societal well-being, others emphasize the importance of a free and open internet as a fundamental right for individuals and a catalyst for the free flow of information.
A proxy block represents a key mechanism employed by authorities to enforce internet censorship. A proxy block involves preventing users from web scraping by intercepting their connection requests and redirecting them away from the desired destination.
In the subsequent sections, we will talk about the implementation of Proxy block, and various strategies for overcoming these barriers to ensure a more open and accessible internet for all.
About Proxy Block
Proxy block is a measure implemented to restrict or prevent access to specific websites or online content by interfering with the connection between users and the internet. The term “proxy” in this context refers to an intermediary server that acts as a bridge between a user and the internet.
When individuals attempt to use proxy servers to access restricted content, authorities or organizations deploy a proxy block to identify and block these attempts. This process disrupts the flow of information, limiting users’ ability to bypass imposed restrictions and access content that might be deemed objectionable or sensitive.
Common methods used to implement proxy block
Highlighted below are ways through which proxy block is implemented by certain authorities online:
- URL Filtering: One effective method of proxy blocking involves filtering specific URLs or web addresses. Authorities or organizations create a blacklist of URLs associated with proxy browsers, and when a user attempts to access these URLs, their connection is redirected or blocked, preventing access to the proxy server.
- Deep Packet Inspection (DPI): DPI is a sophisticated method where network traffic is analyzed at the packet level. Authorities can use DPI to identify patterns or signatures associated with known proxy connections, enabling them to block or reroute traffic attempting to use these proxies.
- DNS Filtering: DNS (Domain Name System) filtering involves preventing the resolution of domain names associated with proxy servers. By intercepting DNS requests and blocking the resolution of specific domains, authorities can effectively impede access to proxy servers.
- IP Blocking: This method involves blocking specific IP addresses associated with known proxy servers. Once an IP address is identified as a proxy, authorities can restrict access to any online content hosted on that address.
- SSL/TLS Inspection: Secure Socket Layer (SSL) and Transport Layer Security (TLS) encryption protocols are commonly used to secure internet communications. Some entities employ SSL/TLS inspection to decrypt and inspect encrypted traffic, allowing them to identify and block proxy connections.
Reasons behind the imposition of proxy block by authorities or organizations
Authorities implement a proxy block due to certain reasons. Some of these reasons are considered below:
- Control and Censorship: Governments and organizations often implement a proxy block to maintain control over the flow of information. By restricting access to specific content through proxies, they can censor information that goes against their policies, ideologies, or cultural norms.
- National Security Concerns: Authorities may impose a proxy block in the name of national security. By preventing access to certain websites or services, they aim to mitigate potential threats, such as the dissemination of extremist content or communication among dissenting groups.
- Regulation and Compliance: Organizations, particularly in educational or corporate settings, may impose a proxy block to enforce compliance with acceptable use policies. This helps in preventing employees or students from accessing content that is deemed inappropriate or unrelated to their responsibilities.
- Protection of Intellectual Property: A proxy block may be implemented to curb the unauthorized distribution or access to copyrighted material. This is particularly relevant in industries such as media and entertainment, where protecting intellectual property is a paramount concern.
Understanding the motivations and methods behind a proxy block is crucial for individuals seeking to navigate the web freely.
Consequences of Proxy Block
Without a doubt, a proxy block helps protect certain information online. However, it puts users at a disadvantage in some areas.
Impact on Freedom of Information
Proxy block subjects users to:
- Curtailment of Free Speech: A proxy block has a direct impact on freedom of expression and speech, as they restrict individuals from accessing and sharing information that may be critical of authorities or divergent from mainstream narratives. This curtailment undermines the democratic principles that rely on an open exchange of ideas.
- Limited Access to Diverse Perspectives: By blocking access to proxy servers, authorities limit the ability of individuals to explore diverse perspectives and alternative viewpoints. This restriction contributes to a homogenized information environment, hindering the development of well-informed opinions and critical thinking.
- Suppression of Investigative Journalism: Journalists often rely on unrestricted access to information for investigative reporting. Proxy block can impede journalists’ ability to access crucial sources, hindering their efforts to uncover and report on issues of public interest.
Challenges Faced by Individuals, Businesses, and Organizations
Individuals often suffer issues online due to a proxy block. This include:
- Personal Privacy Concerns: Users attempting to bypass Proxy block may resort to less secure methods, raising concerns about personal data privacy and security. The use of unverified proxies or virtual private networks (VPNs) can expose individuals to potential risks, such as data breaches or malicious activities.
- Impact on Business Operations: Businesses operating in regions with stringent internet censorship may face challenges in accessing essential online tools and resources. This can impede communication, collaboration, and the overall efficiency of business operations.
- Innovation and Research Limitations: Researchers and academics often require unrestricted access to global information sources. A proxy block can hinder their ability to access the latest research, collaborate with international peers, and stay updated on emerging trends.
Global Perspectives on Internet Censorship and Proxy block
- Varied Approaches to Internet Censorship: Different countries adopt diverse approaches to internet censorship based on cultural, political, and social factors. Some nations implement strict controls over online content, while others prioritize a more open and permissive internet environment.
- Impact on Global Information Flow: Internet censorship, including Proxy block, has implications beyond national borders. As information is increasingly interconnected on a global scale, restrictions in one region can affect the free flow of information worldwide, potentially limiting cross-cultural understanding and collaboration.
- Digital Divide: Internet censorship practices contribute to a digital divide, creating disparities in access to information and technological resources. Regions with extensive censorship measures may experience limited access to educational content, hindering their ability to participate fully in the global digital economy.
With users understanding the consequences of Proxy block, they can better advocate for an open internet and develop effective strategies to overcome such restrictions.
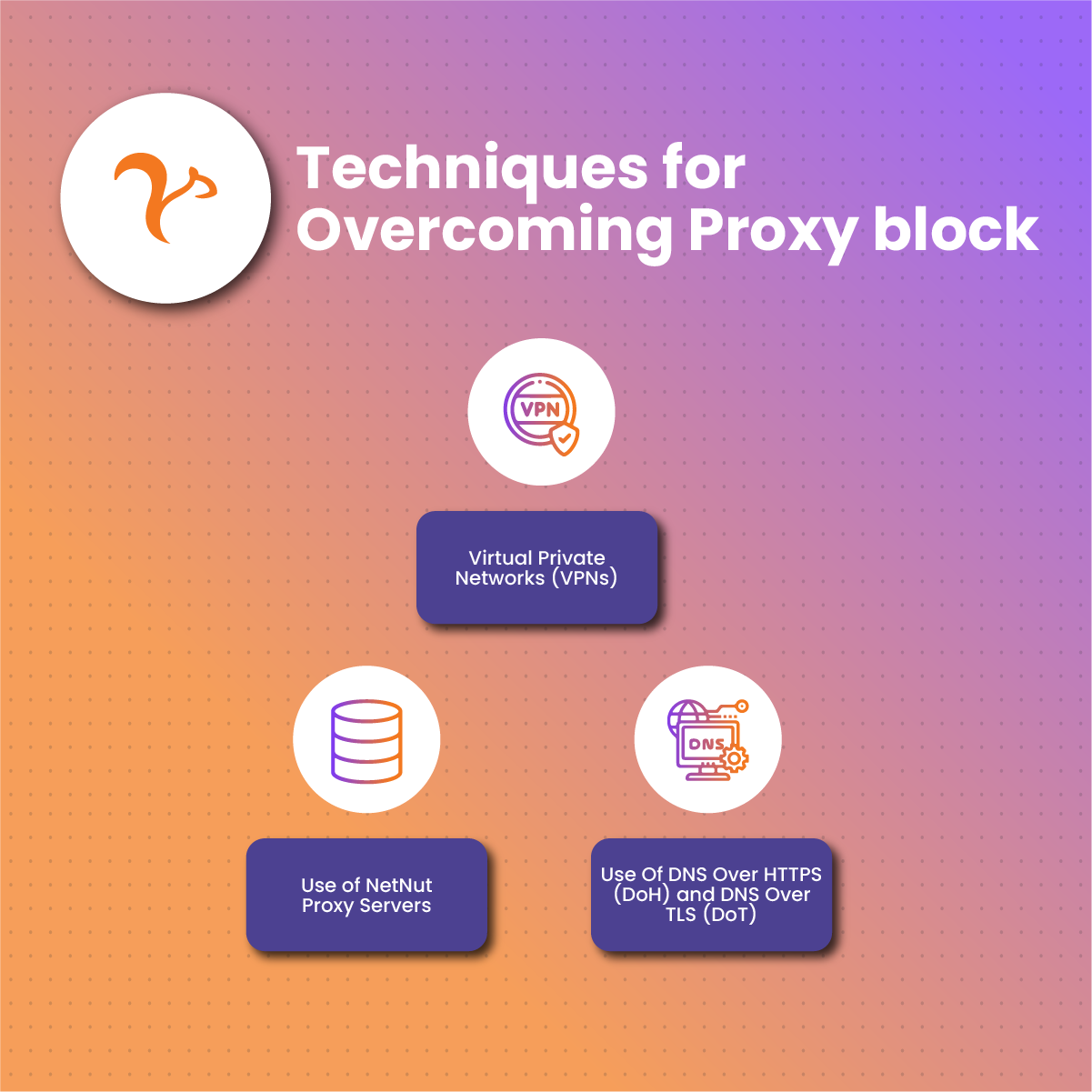
Techniques for Overcoming Proxy block
For individuals and business owners looking to bypass proxy block online, highlighted below are effective methods they can implement:
Virtual Private Networks (VPNs)
VPNs work by creating a secure, encrypted tunnel between the user’s device and a server located in a different geographical location. The user traffic is routed through this encrypted tunnel, making it difficult for ISPs or authorities to monitor or block specific content.
Use of NetNut Proxy Servers
For users looking to access content easily and overcome a proxy block, NetNut offers an innovative proxy solution. NetNut- a proxy service provider, plays a pivotal role in ensuring that users can access online content, irrespective of geographical restrictions or Proxy block. This is made possible through Dynamic IP Addresses.
NetNut’s use of dynamic IP addresses adds a layer of agility to its service. The constant rotation and updating of residential IPs ensure a dynamic and diverse range, reducing the risk of being flagged by websites implementing a proxy block. This dynamic approach significantly contributes to users’ ability to bypass restrictions effortlessly.
NetNut excels in overcoming a proxy block implemented by websites. The combination of its dynamic residential proxies, diverse geo-locations, and high-speed connectivity allows users to navigate the web without encountering the common roadblocks posed by proxy restrictions. Users can enjoy unrestricted access to region-specific or geo-restricted content, making NetNut an invaluable tool for those seeking a seamless online experience.
Use Of DNS Over HTTPS (DoH) and DNS Over TLS (DoT)
DNS translates human-readable domain names into IP addresses. Traditionally, this process occurs in plaintext. DNS encryption methods, such as DoH and DoT, add a layer of security by encrypting DNS queries.
How DoH and DoT Work:
- DNS Over HTTPS (DoH): Encrypts DNS queries using the HTTPS protocol, securing the communication between the user and the DNS resolver.
- DNS Over TLS (DoT): Secures DNS queries by tunneling them through a TLS-encrypted connection.
This method enhances privacy, protects against eavesdropping, and mitigation of DNS-based attacks.
Conclusion
In summary, in a world where the free flow of information is essential for individual empowerment, innovation, and global collaboration, overcoming a proxy block becomes paramount. Internet censorship, implemented through Proxy block, not only hampers the fundamental right to access information but also restricts free speech, limits the exchange of ideas, and limits cultural diversity.
Proxy servers serve as a vital tool in the fight against internet censorship. From traditional proxy servers to advanced VPN technologies and decentralized networks, proxies empower individuals to overcome barriers, access information, and express themselves freely.
However, it is imperative that users remain vigilant, informed, and proactive in adopting safe and ethical practices to navigate the web with resilience against censorship. Enjoy unrestricted internet access by overcoming a proxy block with use of NetNut Proxy servers.
Frequently Asked Questions And Answers
What is a proxy block, and how does it affect my internet experience?
A proxy block is a security measure implemented by websites to restrict access from proxy connections. It can impact your internet experience by preventing access to certain content, especially region-specific or geo-restricted material.
Can NetNut proxy service help me access region-restricted content from other countries?
Absolutely. NetNut’s diverse geo-locations and extensive network of servers allow users to choose specific regions, providing a reliable solution to access content restricted to certain geographic areas. It effectively bypasses region-based limitations, offering users the ability to access a global range of online content.
Does NetNut ensure online security and anonymity?
NetNut prioritizes user privacy by routing internet traffic through a residential IP network, making it more challenging to trace users’ online activities. The use of dynamic IP addresses and encryption protocols enhances security, providing users with a secure and anonymous browsing experience.