How Does a Proxy Firewall Protect You?
Having a proxy firewall is one of the best ways to protect your personal information from third parties online. Regardless of the type of business you own, investing in a proxy firewall is an excellent decision to ensure peace of mind in the long run. Proxy firewalls are also excellent for personal use.
You should always have a plan to protect your sensitive data, whether it’s your financial data, passwords, or personal information. However, there are different types of firewalls you can get today, so which one should you use?
This article will walk you through proxy firewalls, how they work, and why they’re different from other options on the market. If you’re looking for premium-quality proxy firewall solutions for your business, check out NetNut.
What’s a Proxy Firewall?
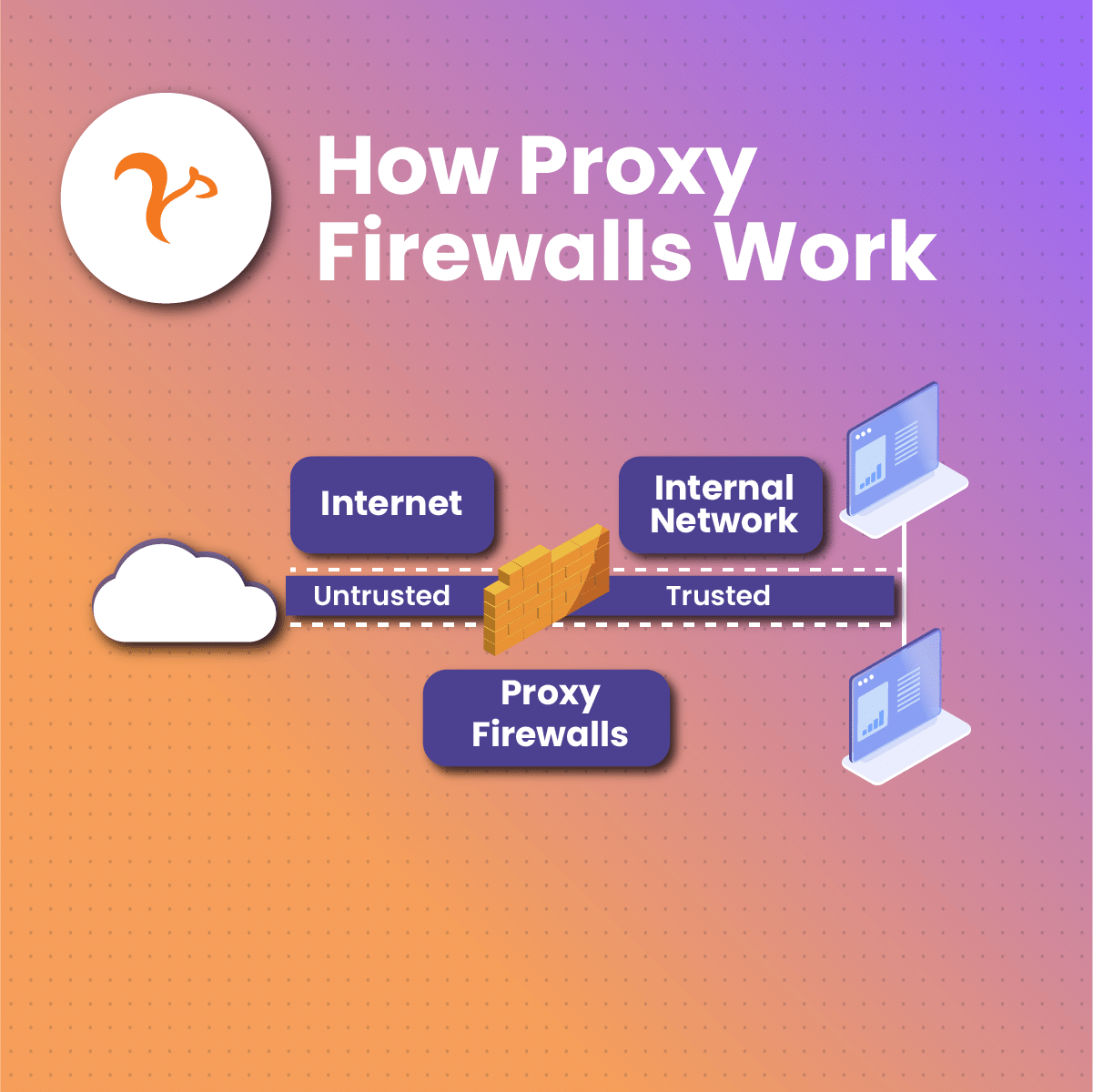
A proxy firewall is a security system that helps you protect your personal information and other resources by filtering everything going in and out of the network. It acts as an intermediary between the internet and your internal network.
How Does a Proxy Firewall Work?
In simple terms, if a computer or device in your internal network wants to make a connection with a website, it must communicate with the proxy firewall. The proxy firewall forwards the data from the network to the outside internet and then takes the data received from there to the internal network.
Your proxy firewall, in other words, inspects all internet traffic to detect any potential threats to your internal network.
Cybersecurity is a severe issue nowadays. According to the University of North Georgia, there’s a hacker attack at least every 39 seconds. This means you should make your network’s protection a priority.
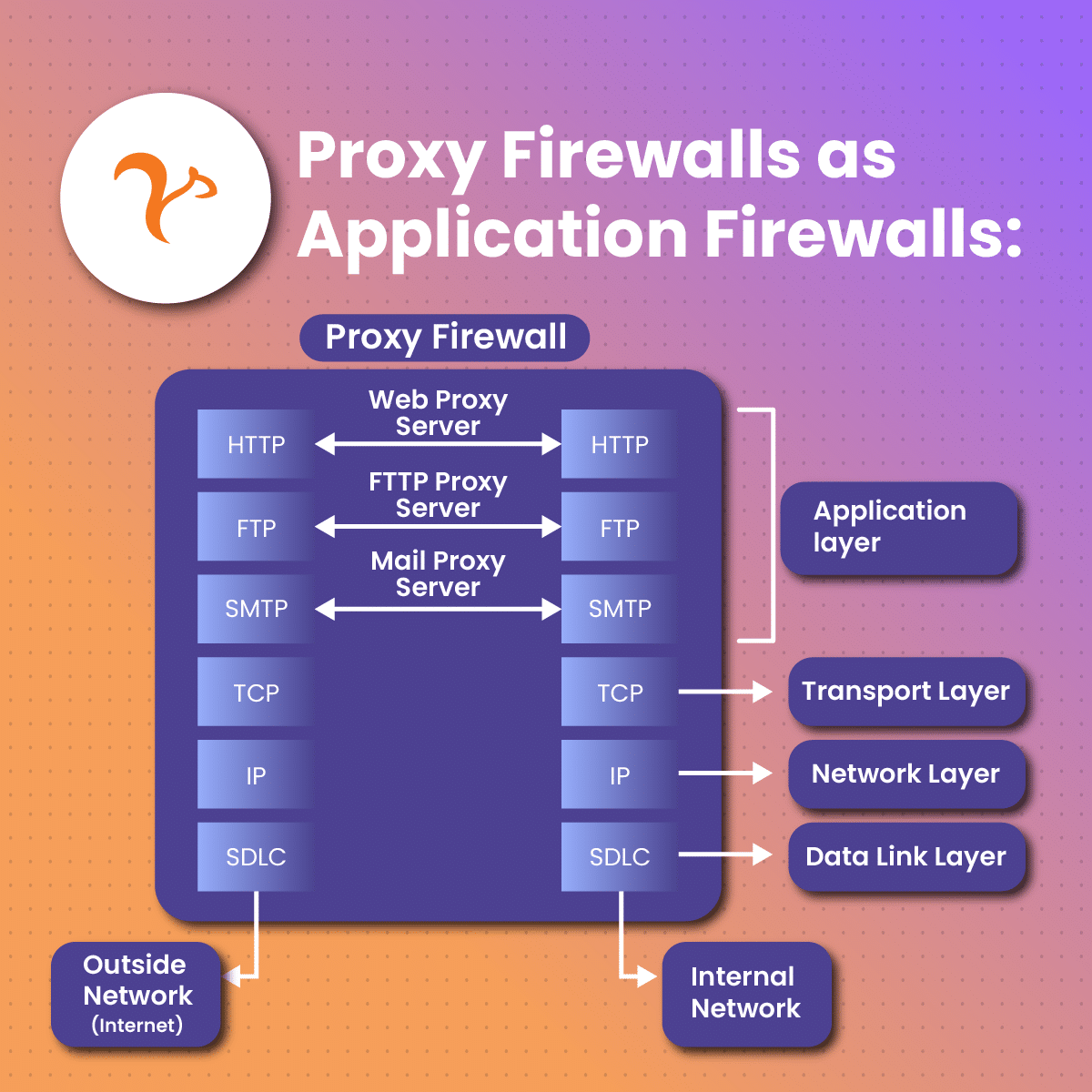
If your business aims to collect data from the internet seamlessly, you would also benefit from getting a proxy firewall. These firewalls filter your network traffic at the “application layer.” It’s the 7th layer of the Open Systems Interconnection Model.
What does this mean? Essentially, a proxy firewall will be your first line of defense. It ensures that an outside connection doesn’t receive packets directly from your internal network.
Proxy firewalls have a few extra benefits besides filtering unwanted packets on your internal network. You can also use a proxy firewall to restrict access to sensitive sites. Some businesses, for example, set up proxy firewalls so that employees don’t access their social media profiles during working hours.
To summarize, here’s what a proxy firewall can do for you:
- Restrict web access to certain sites based on your security policy.
- Inspect traffic at the application layer and detect suspicious/malicious intent.
- Cache website traffic to improve browsing performance.
What’s the Difference Between a Proxy Firewall and a Server?
Proxy firewalls are also called “proxy servers.” However, it’s important to note that not all proxy servers can be considered firewalls. There’s a slight difference you must keep in mind.
Both proxies are similar in the sense that they act as an intermediary between the outside internet and your internal servers. They can also cache web pages to reduce network congestion.
A regular proxy server will allow you to connect to blocked services or hide user information, ensuring more anonymity. However, that doesn’t mean that it will also inspect your traffic to protect your network against potential threats.
In other words, if you want a deeper level of protection while doing things like web scraping, a proxy firewall will be the better option.
What’s the Difference Between a Proxy and a VPN?
Proxy firewalls are also compared to VPNs. On paper, they look similar, but there are also a few differences between them. Both options will hide your device’s IP address and bypass geo-restrictions, but other than that, they differ in encryption and coverage.
- Encryption: Besides hiding your IP address, VPNs encrypt your entire web activity. Usually, a proxy firewall won’t encrypt your online activity.
- Coverage: A proxy firewall/server will only hide one website or app at a time, whereas a VPN will encrypt all web activity from a user.
Which one do you need? It depends. If you’re looking for a cost-effective solution to keep your data collection process secure, a proxy firewall will be the better option. Proxies promote anonymity, better performance, and easy access to geo-restricted content.
If you have the budget, you could get both options and have an additional layer of security. However, keep in mind that certain proxy firewalls can prevent VPNs from authenticating packets correctly.
What Makes a Proxy Firewall Different from a Traditional Firewall?
Essentially, a traditional firewall isn’t designed to mask your IP address or inspect incoming/outgoing traffic. While it still monitors your network traffic and offers protection, it won’t give you anonymity while browsing.
Additionally, traditional firewalls work on the transport and network layers, whereas a proxy firewall works on the application layer.
A proxy firewall will give you all of the benefits that come with a firewall plus the ability to hide your IP address. You could argue that a proxy firewall is a newer and more advanced version of the traditional firewall.
Why Would You Need a Proxy Firewall?
There are many reasons why a proxy firewall could benefit your business. Many companies use this service for market research since it helps them gather unbiased and meaningful information that helps them stay ahead of the competition.
However, proxy firewalls can protect your internal network regardless of what you want to do online. The main goal of the proxy firewall is to control what enters and leaves your network, keeping it free from viruses or cyber-attackers.
If you’re struggling to protect your internal network while collecting data online, a proxy firewall will likely be the most secure solution. Even though proxies aren’t “necessary” to perform those tasks, they prevent attackers from having access to your IP address.
Someone can use your IP address to infiltrate your computer or internal network, which can lead to a wide range of security breaches and data loss. With the help of a proxy firewall, you can be safe while browsing while enforcing corporate internet browsing policies.
Pros and Cons of Proxy Firewalls
Advantages of Having a Proxy Firewall
A proxy firewall will give you plenty of benefits, whether you’re using it for web scraping or to browse social media. Once you get your proxy firewall set up, you’ll be able to browse the internet and gather all the information you need without risking sensitive internal data.
Let’s look at the main benefits you can get from installing a proxy firewall:
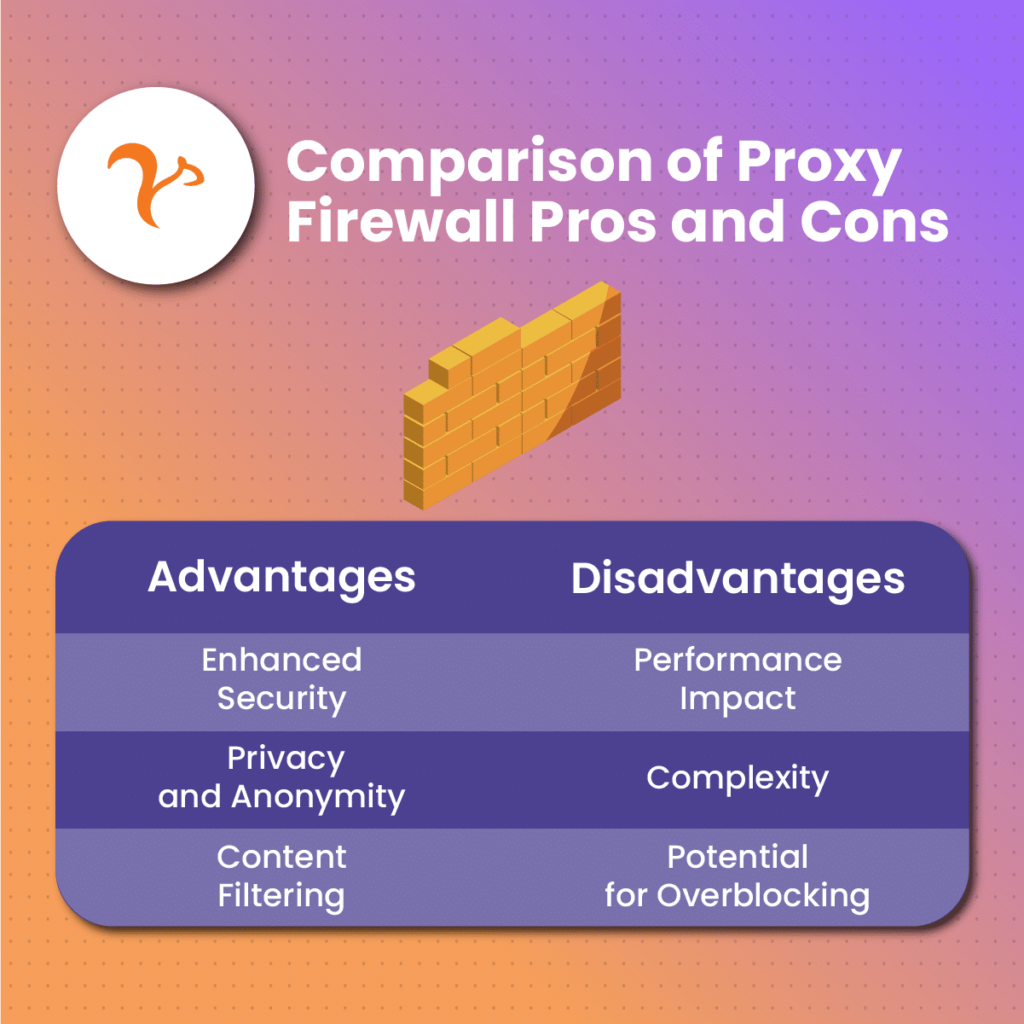
Logging: Proxy firewalls give clients better logging capabilities than other products. This is essential for security administrators who want to deal with security incidents smoothly. Thanks to the proxy firewall, you can examine the entire network instead of just the network address and port number.
Security: As mentioned previously, a proxy firewall is one of the most advanced security systems you can get for your business. Since your proxy will have a specific IP address, you will be able to prevent external networks from receiving packets from your internal network. In other words, you can prevent direct network contact with the outside internet.
Control: A great benefit of proxy firewalls is that they allow administrators to configure them to different levels of security. You can set up different security layers based on individual users or groups. If your provider offers it, you can also get access logs with all the information you need about past user activity.
Access: It’s common to be blocked from certain websites. This is something that can make the data collection process more difficult for your business. Thanks to proxy firewalls, you can enter websites with restricted access without exposing your IP. If you get a residential proxy, for example, you can set a specific location and browse the internet as if you were there. This is an excellent tool for those who want to bypass geo-restrictions.
Disadvantages of Having a Proxy Firewall
Even though proxy firewalls have plenty of benefits for individuals and businesses, there are still a few drawbacks to consider. We don’t think the disadvantages are enough to outweigh the advantages, but you should still keep them in mind before choosing your preferred proxy firewall service.
Performance: Proxy firewalls act as a third party between the outside network and the device in use. In other words, this is an additional connection for each outgoing/incoming packet, which could slow down connections in businesses with heavy traffic loads.
Learning Curve: Installing a proxy firewall isn’t easy. Most of the time, you need special knowledge and skills to be able to set up everything correctly. If you don’t have experience with proxy firewalls, it could take you a while before you learn how to set them up and not affect your network’s structure.
Single Point of Failure: A proxy firewall, if not installed correctly, can become a single point of failure (SPOF). In essence, a SPOF is a part of a system that can make the entire structure stop working if it fails. A poor-performing proxy firewall can become a bottleneck, which can slow down performance in your network and ultimately cause it to stop working.
Overblocking: Not setting up a proxy firewall correctly can lead to overblocking. This means that the proxy firewall could block necessary content by accident, causing issues when gathering data.
Compatibility: Proxy-based firewalls aren’t compatible with all protocols. You would need to reach out to your vendor and evaluate whether the option you got works for your network.
The best news here is that you can solve most of those issues by getting your proxy firewall from a reputable vendor. Our team at NetNut is committed to providing you with top-performing proxies in a wide range of locations. Feel free to reach out and discover all the options available.
How a Proxy Firewall Protects Your Connection | Overview
The devices in your internal network will use a main computer as a gateway, which will be the one connected to the internet. This allows the proxy firewall to cache information and documents requested by all users.
Once a user tries to enter an external site through a proxy firewall, this is what would happen:
- They request access to the outside network through a protocol. It could be an HTTP or an FTP protocol.
- The device creates a session between the user and the server. It sends a SYN message packet from their IP address to the server’s IP.
- The proxy firewall gets the request. If its policy allows it, it will send back a SYN-ACK message packet from the other server’s IP address.
- The user’s device will receive the SYN-ACK packet. It will send a final ACK packet to the outside server’s IP address. At this point, the user will be connected to the proxy firewall.
- The proxy firewall sends a SYN packet from its IP address to the external server. Once the server sends the SYN-ACK packet back, the proxy firewall replies with an ACK packet. Here, there’s a connection between the proxy firewall and the user’s device, as well as the proxy and the external server.
- Any requests made through these connections will be inspected to ensure they comply with corporate policies. This process goes on until any of the sides ends the connection.
Even though that may seem like a long process, it only takes a few seconds in real-time. All that work ensures that your proxy firewall inspects every packet coming in and out of your internal network, which will promote better security.
Most proxy firewalls work for core internet protocols, so they should be run against all supported applications. Some of the most common protocols include:
- FTP
- HTTP
- DNS
- ICMP
- SMTP
Usually, the proxy firewall will be deployed within a collection of trusted programs that also support a particular application protocol.
How Do You Get a Proxy Firewall?
There are plenty of ways to get a proxy firewall. First, you would need to evaluate which type of proxy you want. If you want an American IP for data extraction or any other purpose, for example, you would need to get a US proxy.
You would also need to check your computer’s proxy settings to determine which type of proxy you can set up. The process only takes a few seconds.
If you’re having trouble with that, you can seek assistance from our team.
Depending on the case, you could set up your proxy manually, automatically, or through a script. Windows computers, for example, will automatically check if your business has an automatic proxy firewall set up. If it does, it will give you a list of instructions to start your connection.
If you want to get started with NetNut, on the other hand, all you have to do is create an account and fill out the form requested by the team. Then, you’ll get access to a personalized dashboard where you can get started with your browsing.
Where Are Proxy Firewalls Deployed?
Generally, proxy firewalls are deployed on “bastion” hosts in your internal network. A bastion is a device in your network with a high attack potential. In other words, it’s a network computer that needs better protection against attacks.
Common Types of Proxy Firewalls
There are three main types of proxy firewalls you can get for your business. Even though the three of them will do a great job of protecting your network, you must know the difference so that you choose the one that better suits your needs:
Forward Proxy Firewall
The forward proxy is the most common deployment for a firewall. In this case, the proxy firewall will be between your local network and the internet.
All traffic has to pass through the proxy firewall server. Here, traffic can be cached, which helps manage heavier network loads.
Reverse Proxy Firewall
As the name implies, you can expect this proxy firewall to work “backward” compared to the option above. Here, the proxy firewall is located between the internet and web content servers. Once the packets leave content servers, they must go through the firewall before ending up in a private network.
Your business will be able to control the information that leaves your server and the one that your users receive. As with the previous option, it’s possible to cache data on the server, allowing everyone to access content faster.
Transparent Proxy Firewall
Also called “forced firewalls,” these are “invisible” to the user. You can set them up as either a forward or reverse firewall.
The main benefit of this type of proxy firewall is that it doesn’t change request/response formats, so your users will feel like they’re experiencing “regular traffic.” In essence, this proxy firewall is much harder to detect.
Companies set up transparent proxy firewalls to block content from external websites. They also use them to monitor user activity without risking detection.
Common Uses for Proxy Firewalls
There are dozens of uses you can consider for proxies. Generally speaking, a proxy firewall can help you gain a competitive edge, as it can help you collect data safely from other places on the internet.
If you want to do market research, for example, you could get a static residential proxy from the location you prefer and browse the internet as if you were from that area. The proxies offered at NetNut allow you to collect data at any moment of the day with 100% anonymity.
Companies that need a higher anonymity level and avoid potential blocks could get rotating residential proxies. These proxies can bypass anti-bot activities with ease, allowing you to gather as much information as you want while avoiding detection.
Since you’re using a “rotating” IP, you will get a new IP address every time you make a connection request. This provides an extra layer of protection to businesses that have heavy data scraping needs.
There are many more uses to consider for your proxies. These include:
- Email protection
- Social media management
- Website change monitoring
- Food delivery data
- Brand protection
- Review monitoring
- Web data extraction
- Cybersecurity
- Threat intelligence
- Price comparison
- Ad verification
Which Proxies Can You Get at NetNut?
At NetNut, we have over 52m premium rotating residential proxies. These proxies guarantee 24/7 uptime, 100% anonymity, and fast web data collection.
Due to the vast availability of proxies, you won’t run out of IP addresses, ensuring your business is always ready to keep gathering relevant data.
Something that makes NetNut stand out is its unmatched global coverage. It has proxies in dozens of different countries, allowing your business to gain the competitive edge it needs to succeed.
Both rotating and static residential proxies have a 99% success rate, whereas mobile IP requests have a 100% success rate. You can rest assured you’ll be able to perform any online tasks without any problems or interruptions. Even if you were to have any issues, our team is more than ready to assist you and let you get back on your feet.
We’re committed to giving people tailored solutions to problems. Not only do we offer a dedicated account manager, but we also have five different customer support channels available. If you’re having trouble finding the right option for your needs, feel free to reach out.
To summarize, here’s what you can get at NetNut:
- Static Residential Proxies
- Rotating Residential Proxies
- ISP Proxies
- Mobile Proxies
- Datacenter Proxies
On top of that, you’ll get the following benefits:
- Zero IP blocks
- Cost-effective solutions
- Lightning-fast data collection
- Real mobile phone Ips
- City-level targeting
- High grade of anonymity
- Personalized IP rotation
- Usage statistics
- Stability
Bottom Line
Everyone who goes online is at risk of getting attacked. With the recent improvements in technology, it has become harder to avoid cyberattacks completely. Businesses without the right security solutions risk losing sensitive data and getting blocked from certain websites while gathering data, which can make it harder for employees to reach their goals.
Thankfully, proxy firewalls provide the necessary protection users need while collecting valuable data. By getting the right solution, your business will be able to stay ahead of the competition and gather information faster than anyone.
Reach out to our team at NetNut if you’re interested in getting custom proxy firewall solutions for your browsing needs.
Frequently Asked Questions
How Does a Proxy Firewall Protect You?
A proxy firewall can limit the applications that an internal network supports. In other words, it inspects and processes incoming/outgoing packets between internal users and the internet.
Once installed, the firewall can block suspicious traffic, protecting your sensitive data. Additionally, the proxy can mask the user’s IP address, allowing them to browse restricted websites with ease.
How Do I Get Started with NetNut?
- Sign up and create an account.
- Choose a proxy plan according to your needs and goals. NetNut offers plans based on Bandwidth or Successful Requests.
Once you’re finished, the proxy network will transparently perform load balancing, connecting you to the websites you want. You can also integrate your proxies with your preferred tool.
Can a Firewall Act as a Proxy?
Not necessarily. A traditional firewall won’t offer the IP masking capabilities that a proxy has. However, if you get a proxy firewall, you’ll get both benefits within the same product.