How to Defend Against Reverse Proxy Phishing Kits
Multi-factor authentication (MFA) has become increasingly popular in recent years, with some regulatory watchdogs making it a requirement for certain industries. Financial services, for example, must have MFA for accessing online banking, making payments, and executing transactions. However, with the rise of enhanced security controls comes a dramatic surge in new cyberattacks that bypass MFA. One of the recent campaigns involved the use of a reverse proxy phishing tool known as EvilProxy.
In this article, we will explore the rise of EvilProxy attacks across the globe and how reverse proxy phishing tools work. Keep reading until the end, as we will go over how individuals and businesses can protect themselves from such cybersecurity attacks. Let’s get started!
What Is Reverse Proxy Phishing?
Reverse proxy phishing, also known as man-in-the-middle phishing, is a sophisticated cyber attack where a malicious actor sets up a reverse proxy server in between a user’s interactions with a legitimate website. This proxy intercepts and manipulates the traffic to and from the website, capturing sensitive information such as login credentials, personal data, and financial details without the user’s knowledge.
The attacker’s proxy server mimics the appearance and functions of the target website, making it exceptionally difficult for users to detect the deception. This technique is particularly dangerous because it can bypass traditional security measures and SSL certificates, leading users to believe their communications are secure and encrypted while, in reality, their data is being harvested by the attacker. Reverse proxy phishing is a growing threat in the digital world, emphasizing the need for robust security protocols and user awareness.
The Rise of EvilProxy Attacks
In the past year, there were over 120,000 phishing emails sent to more than a hundred organizations. This campaign targeted high-level officials at tech companies in a bid to steal their Microsoft 365 accounts.
The proxy phishing attack combined brand impersonation with bot detection evasion and open redirections to steal usernames, passwords, and other important information.
What Is an EvilProxy Attack With Reverse Proxy Phishing?
An EvilProxy kit uses reverse proxy phishing capabilities to steal a user’s credentials and bypass two-factor authentication.
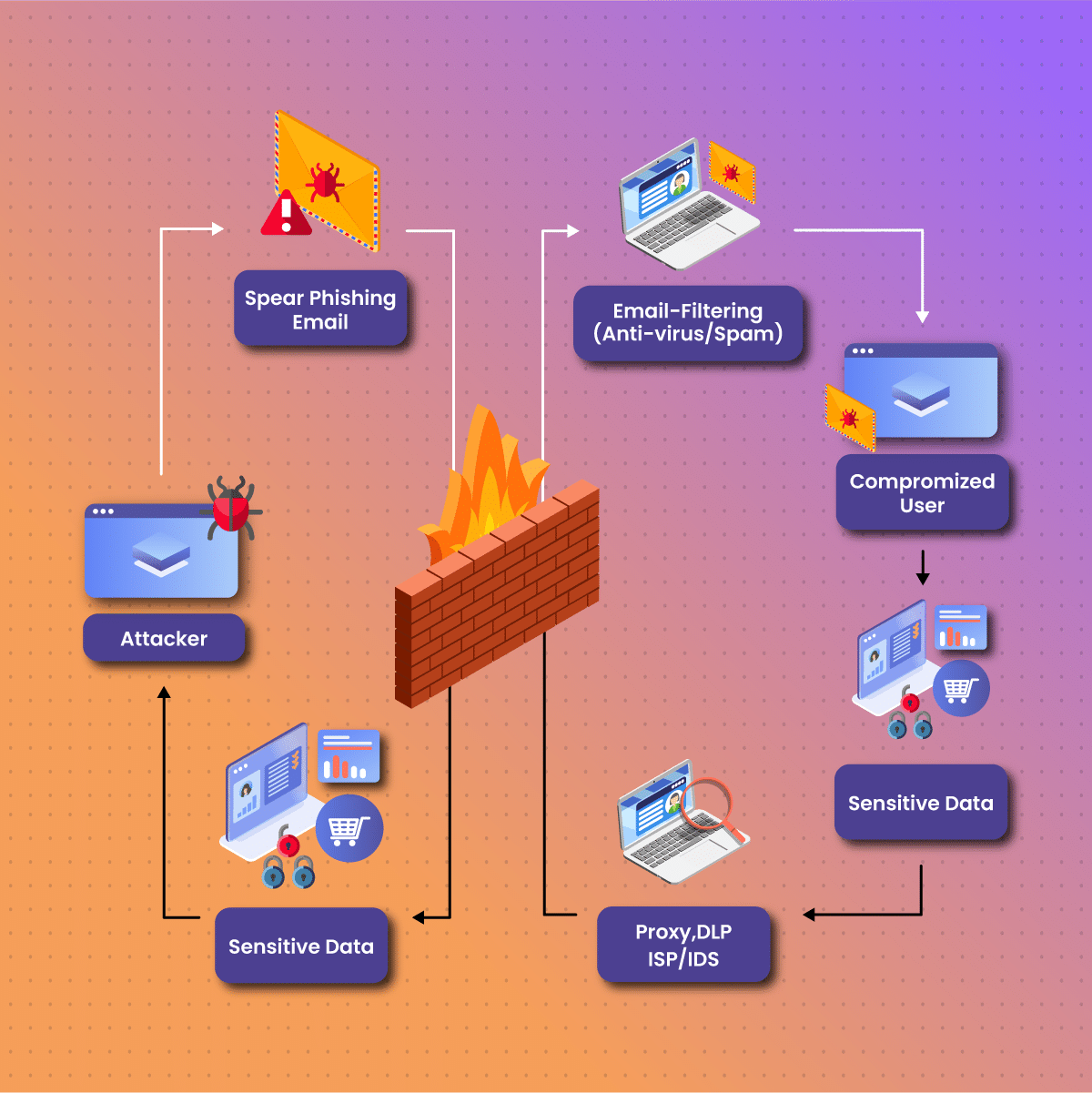
To cut through all of the technical jargon and help you understand how the EvilProxy attack works, here is the four-step process:
- The threat actor sets up a fake domain and reverse proxy before sending the victim a phishing link.
- The victim clicks on the phishing link, uses their credentials, and follows the MFA procedure to gain access to their account.
- The threat actor steps in, intercepts the request and sends the information to the real website. When the website responds, the threat actor intercepts and relays it forward to the victim. This allows them to collect session cookies.
- The threat actor authenticates the cookies by using them in the real domain.
Getting a hold of an EvilProxy kit is simple, and the user interface is easy to use, which makes it highly accessible to any cybercriminal. They can create new campaigns and have access to a ton of customizable options.
How Does a Reverse Proxy Phishing Attack Campaign Using EvilProxy Work?
To understand whether your cybersecurity is under a reverse proxy phishing attack, it’s essential to know how the attack campaign starts.
The EvilProxy campaign begins by sending the victims emails from trusted sources. However, unbeknownst to many, it contains a malicious link that redirects the internet user to a legitimate website.
To prevent discovery, the EvilProxy campaign uses a series of redirections. This covers the threat actor’s tracks and takes advantage of the cybersecurity system’s vulnerabilities.
Eventually, after multiple redirections, the individual lands on the phishing website, which functions as a reverse proxy.
The attacker decodes the victim’s email addresses before they land on the EvilProxy phishing page. They use special encoding on compromised legitimate websites.
It may be difficult to wrap your head around how EvilProxy works, which is why we’ll discuss how reverse proxy phishing tools attack users later on in this post.
When cybersecurity experts started to investigate the recent EvilProxy attack, they discovered that the phishing tool did not redirect users with Turkish IP addresses. It actively avoided Turkish users, suggesting that the threat actor may be residing in Turkey.
How Does EvilProxy Make Hacking More Accessible?
According to Resecurity, an American cybersecurity vendor for individuals and businesses, EvilProxy makes hacking more accessible for less experienced threat actors. It steals authentication tokens from a wide range of companies, including Microsoft, Apple, Twitter, Facebook, and Google.
Although reverse proxy phishing is a technical process, EvilProxy makes it extremely easy to carry out these types of cybersecurity attacks. When a threat actor purchases malicious software, it comes with a set of instruction videos to help them set up their campaigns.
EvilProxy also has an intuitive user interface that is simple to navigate. It even has templates of original websites that make it easy to steal credentials and authentication tokens.
Threat actors can purchase a 10-day EvilProxy subscription for as low as $150 or pay $450 for a monthly pass. Compared to other proxy phishing tools out there, EvilProxy is by no means a cheaper alternative.
However, it is a much more advanced phishing-as-a-service kit that allows less experienced threat actors to access valuable accounts that they can sell to others.
How Do Reverse Proxy Phishing Tools Work?
Traditional security methods involved the use of usernames and passwords for individuals to access their accounts. As the nature of the cyberattacks evolved, it became necessary for companies to introduce advanced protection, such as multi-factor authentication.
MFA became the new face of cybersecurity for a while until hackers developed an even more sophisticated solution to bypass most two-factor authentications.
Phishing attacks with reverse proxy capabilities use the adversary-in-the-middle technique to steal credentials and bypass MFA.
There are many different types of proxy phishing kits that actors can purchase on the market. Some are simple open-source kits, while others use a series of obfuscation layers to steal credentials (username and password), MFA tokens, credit card details, and other important information.
In recent years, Proofpoint, an American enterprise cybersecurity company, discovered a new type of proxy phishing kit that uses transparent reverse proxy. This highly advanced technique uses the actual website instead of replicating it, which enhances the illusion of safety during logins.
The reverse proxy phishing kit assists the threat actor in capturing the session cookies, which allows them to access targeted accounts without the need for the individual’s username, password, or MFA token.
These new generation phishing kits are not only smart by extracting username and password information during user logins, but it’s so advanced that they can bypass MFA.
As more and more companies adopt MFA to provide an increased level of cybersecurity to their users, experts are expecting a rise in the adoption of reverse proxy phishing kits by threat actors.
How to Protect Your MFA Against Reverse Proxy Phishing Tools?
Although MFA is great at tackling traditional methods of cyberattacks, the MFA tokens themselves fall short, as these are vulnerable to reverse proxy phishing tools.
To combat reverse proxy phishing tools, cybersecurity experts have come up with Deviceless MFA. Typically, a user needs a smartphone to access their account due to the two-factor authentication process, which comes with many constraints.
The Deviceless MFA meets the challenges of cybersecurity without compromising the user experience or ease of deployment. It allows users to authenticate and access their accounts on their browsers without the need for a physical key, smartphone, or other devices.
This cybersecurity solution relies on JavaScript, and it is the most reliable token to protect against reverse phishing proxy attacks. Currently, it is the only token that can block reverse proxy phishing attacks by verifying that the authentication attempt is legitimate.
Why Use Deviceless MFA?
Deviceless MFA ensures easy access to accounts without compromising on security. It simplifies the process for users and administrators, making it a valuable solution to tackle the cybersecurity challenges affecting the workplace.
There are many benefits of using Deviceless MFA, some of which include the following:
Frictionless Login
Since Deviceless MFA does not require an additional device for users to log in, this cybersecurity solution offers a seamless login experience. It has a highly transparent enrollment process and is a universal token that is available for everyone.
Advanced Protection Against Reverse Proxy Phishing Tools
Besides securing access from the browser, the Deviceless MFA is an advanced cybersecurity solution that is highly effective in warding off threats and actors using reverse proxy phishing tools.
Some reverse proxy phishing tools replicate original websites to the point where it becomes next to impossible for a user to distinguish between real and fake.
Deviceless MFA is a reliable token that can verify the URL users are attempting to log into. This ensures that the user accesses a legitimate website, preventing them from providing their credentials and session cookies through a fake URL.
Secure Multi-user Connections
One of the greatest advantages of the Deviceless MFA besides website authentication is multi-user access.
Multiple users can access a website on the same browser, and the Deviceless MFA will ensure that each of the users has their own authentication.
Shared computers can compromise one’s security, but the Deviceless MFA can provide an advanced level of cybersecurity while distinguishing access between the different users.
Tips for Business to Help Reduce the Risks of Cyberattacks
Cyberattacks can have a detrimental impact on a business and its relationship with its customers. It can also adversely affect the users by stealing their credentials and gaining access to their accounts.
Businesses must remain proactive by assessing their company’s cybersecurity needs and investing in tools to help eliminate the existing system’s vulnerabilities and ward off threats.
Below are some tips to help reduce the risk of reverse proxy phishing attacks for businesses:
Invest in Email Security Solutions
Most reverse proxy phishing attacks start with an email address, which is why it is essential to protect employees from malicious emails that take on the identity of trusted sources.
Businesses can invest in email security solutions to filter and block suspicious emails.
Provide Training to the Employees
Most individuals who receive emails from “trusted” sources are often tempted to click on the links, which can lead to multiple redirections. This makes it easy for the reverse proxy phishing attacker to steal personal and confidential information.
Businesses need to stay on top of cybersecurity developments. They must provide their employees with the necessary training to help them identify such attacks, thus reducing the risk of breaches or information theft.
Implement Network Security Solutions
By implementing advanced network security solutions, businesses can prevent most cybersecurity attacks. It’s important to invest in a product that can help detect phishing, malware, or other threats and prevent them from stealing personal and confidential data.
Having an MFA can prevent most of the threat actors from penetrating the business’s cybersecurity system. However, they must also take additional measures to ward off reverse proxy phishing attacks.
Businesses may consider investing in web filters that block employees from accessing malicious websites (duplicates made by threat actors).
Run Proxy Phishing Simulations
One of the best ways for businesses to protect their employees and be ready for cyberattacks is to carry out proxy phishing simulations.
If businesses prepare their employees by carrying out simulations, they’ll be better able to prevent proxy phishing attacks in the future.
Businesses Can Secure Themselves with Netnut Proxies!
Netnut offers companies a wide range of proxy solutions, including residential proxies, ISP proxies, mobile proxies, and much more. It helps businesses stay secure online while assisting them with gathering data and valuable insights.
With over 52 million rotating residential proxies, Netnut ensures seamless online browsing while protecting your business!
Final Thoughts on Reverse Proxy Phishing
Although cybersecurity systems are continuously evolving to protect individuals and businesses, it’s important to understand that the threat actors are also gearing up to combat such solutions.
As more and more businesses adopt MFA, it exposes them to threat actors using reverse proxy phishing tools. These kits have made it easier for less experienced hackers to gain access to a user’s credentials and authentication token.
Businesses must take several steps to ensure that their cybersecurity systems are strong against attackers. They must train their employees by creating awareness of the latest types of threats and invest in solutions, such as Netnut!
Frequently Asked Questions
Here, you’ll find answers to some of the most frequently asked questions about proxy phishing.
What Is a Rotating Residential Proxy?
A residential proxy uses a single, static IP address from a residential ISP for Internet connections. It remains constant unless you change it manually.
On the other hand, rotating residential proxies are a type of proxy server that uses a pool of residential IP addresses sourced from real Internet service providers (ISPs).
The key difference between the two is that a rotating residential proxy employs a dynamic pool of residential IP addresses, automatically switching between them at regular intervals. It can help protect against proxy phishing attacks by constantly changing the IP address used for browsing.
How Does a Proxy Protect Your Email from Phishing Attacks?
A proxy can protect your email from phishing attacks by acting as an intermediary server that filters and blocks suspicious email content. This prevents malicious links or attachments from reaching your inbox and potentially compromising your security.
What’s the Difference Between Phishing and Proxy Phishing?
While phishing involves deceptive emails or websites, proxy phishing leverages proxy servers to mask malicious activities, making it harder to detect and trace the source of the attack.