Complete Guide To Reverse Proxies
A reverse proxy is an excellent tool that helps people protect their web servers from attacks. However, that doesn’t mean these reverse proxy setups are easy. It’s a complex configuration to make, but it can reap many benefits.
Better user experience and web infrastructure are all advantages of a good reverse proxy setup, but these can quickly go bad if the configuration is done poorly. If you want to improve reliability and performance, a reverse proxy is a great option. Learn more about reverse proxies and how to combat the challenges in our complete guide.
What Is a Reverse Proxy?
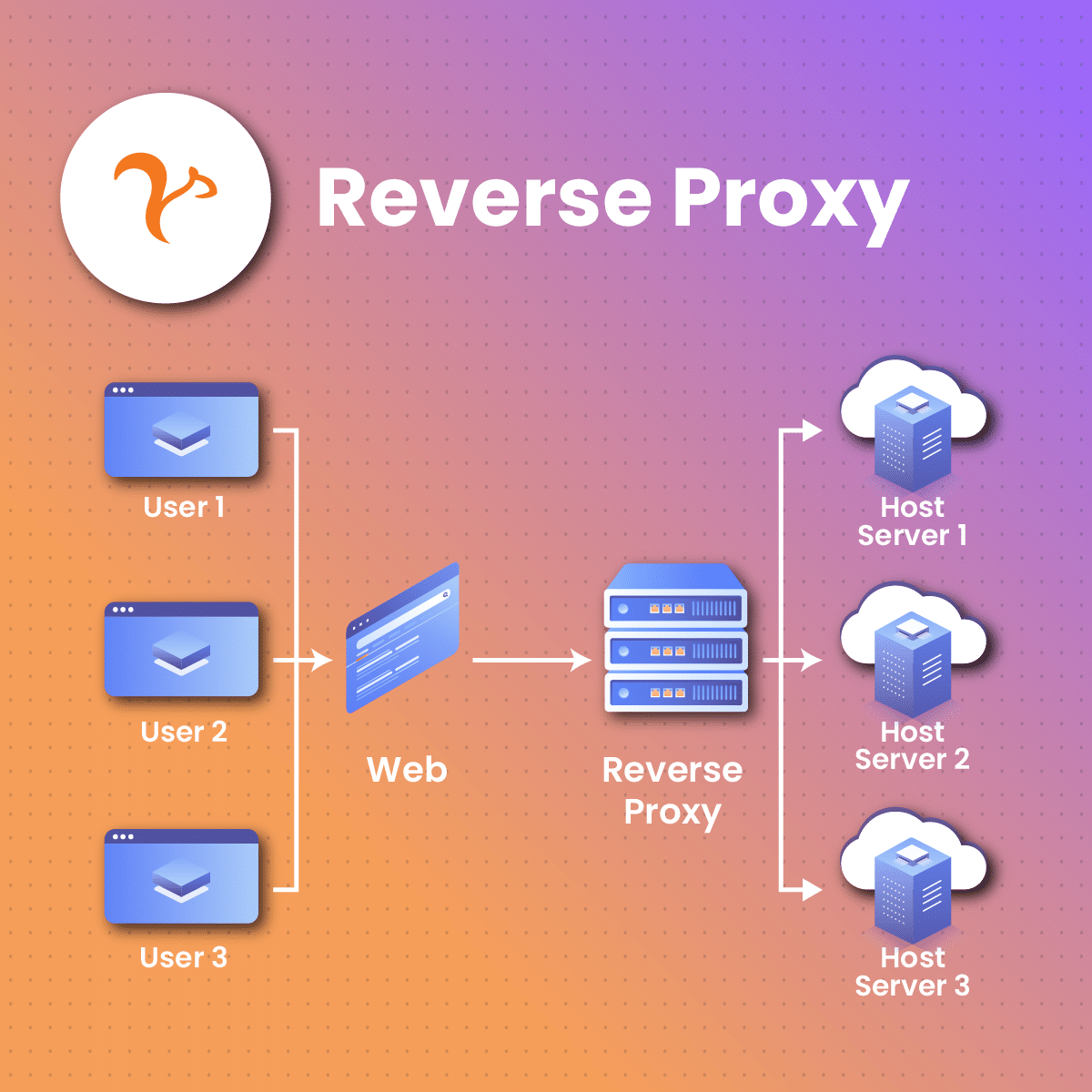
A reverse proxy is a server that sits between client devices and backend servers, acting as an intermediary to handle client requests and relay responses from the servers. Unlike a forward proxy, which serves the needs of clients seeking to anonymize their browsing or access restricted content, a reverse proxy is deployed on the server side to enhance performance, security, and manageability of web services. One of its primary functions is load balancing, which distributes incoming client requests across multiple backend servers to prevent any single server from being overwhelmed, thereby improving overall performance and reliability.
Instead of clients connecting directly to the server hosting the requested resources, they connect to the reverse proxy, which then forwards the requests to the appropriate server. This process enhances security, optimizes load distribution, and provides caching services. Reverse proxies are commonly used to protect sensitive backend servers, hide their IP addresses, and manage incoming traffic efficiently, especially for large websites or applications.
A reverse proxy enhances security by hiding the IP addresses and structure of backend servers, enforcing security policies, filtering malicious requests, and protecting against distributed denial-of-service (DDoS) attacks. It also provides caching capabilities, reducing the need to repeatedly fetch the same data and improving load times while reducing the workload on backend servers. Furthermore, a reverse proxy can handle SSL termination, offloading the resource-intensive task of SSL encryption and decryption from backend servers and simplifying the management of SSL certificates. By compressing inbound and outbound data, it accelerates web traffic, leading to faster load times and an improved user experience.
Finally, reverse proxies can manage centralized authentication for various backend servers, providing a single point of entry and simplifying access control management. These features make reverse proxies essential components in content delivery networks (CDNs), enterprise environments, and any scenario where multiple servers must be managed and optimized to deliver a seamless experience to end-users.
What Is a Proxy Server?
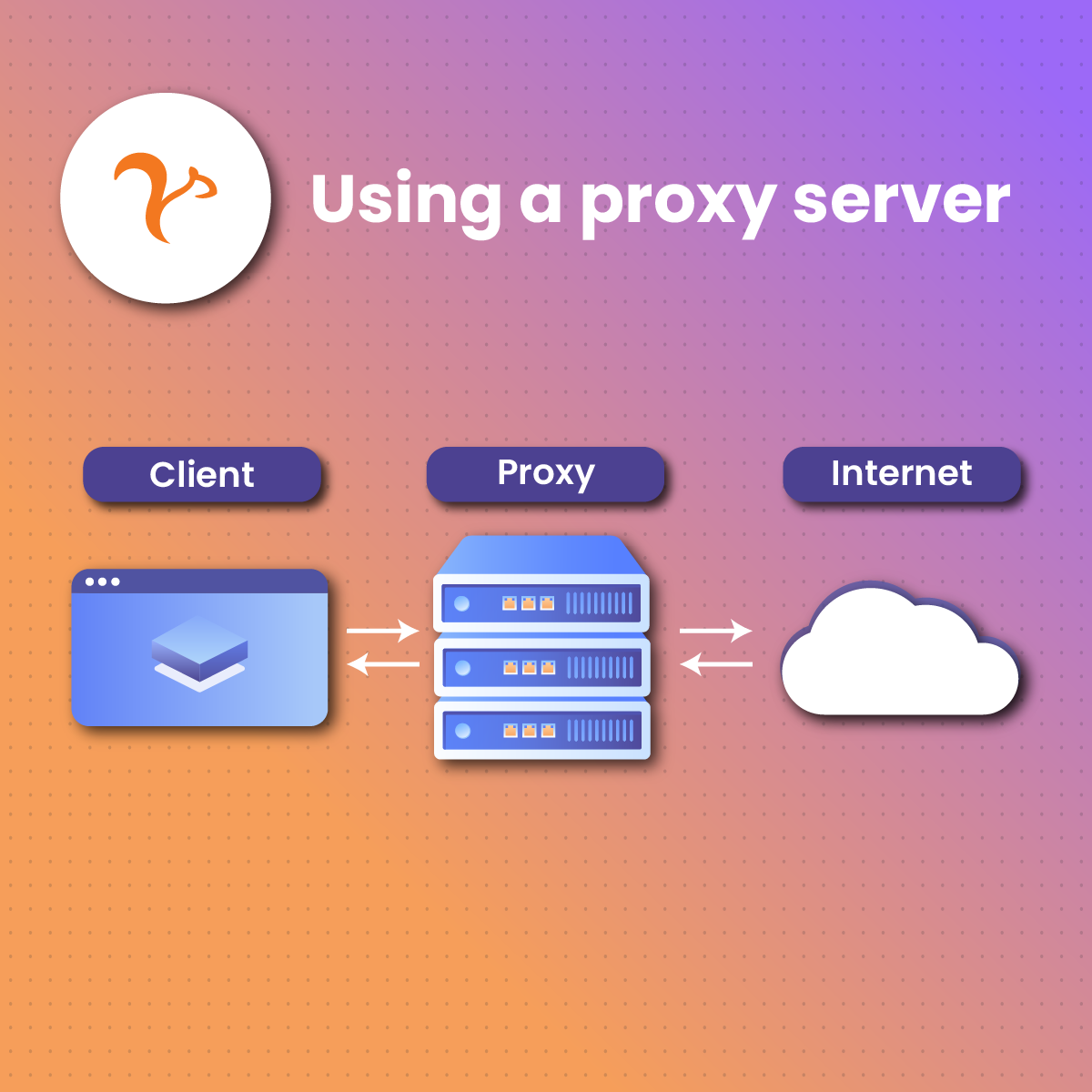
A proxy server (or forward proxy, proxy, web proxy) is a server that’s placed in front of client machines. The role of a proxy server is to intercept any requests made by these client machines. Acting like a middleman, these servers then communicate with web servers on behalf of these client machines.
Here’s a typical forward proxy communication where three computers are involved:
- “A” is a user’s home computer,
- “B” is the web proxy (or forward proxy server), and
- “C” is where the website data is stored (the website’s origin server).
Computer “A” would reach out to computer “C” directly in a standard internet communication. The client machine would be sending these requests, while the origin server would be responding to these client requests.
This isn’t the same communication scheme when a forward proxy is in place. Instead, computer “A” would send requests to “B,” which would pass on the request to “C.” “C” will then respond to “B,” which will be forwarded back to “A.”
How Does A Reverse Proxy Work?
A reverse proxy works by receiving client requests and forwarding them to the appropriate backend servers. When a client, such as a web browser, makes a request to access a website, the reverse proxy intercepts the request before it reaches the backend server. The proxy then determines the best server to handle the request, based on factors like current server load and availability.
When a user sends a request, it first reaches the reverse proxy, which decides which server should handle the request based on factors like load balancing or content delivery. Once the backend server processes the request, it sends the response back to the reverse proxy, which then relays it to the client. This setup not only improves performance and security but also helps prevent server overload by distributing traffic effectively.
Once the request is forwarded to the chosen server, the server processes it and sends the response back to the reverse proxy. The proxy then returns the response to the client. This process not only balances the load among multiple servers but also provides additional layers of security, caching, and SSL termination to optimize performance and protect the backend servers.
Reserve Proxy Vs. Forward Proxy: What’s the Difference?
A reverse proxy is a server that is placed in front of one or multiple web servers and is designed to intercept client machine requests. A forward proxy sits in front of the client’s machine rather than the user’s computer. This is where the two servers differ.
A reverse proxy and a forward proxy both act as intermediaries, but they serve different purposes. A forward proxy is used by clients (such as browsers) to access resources on the internet, hiding the client’s identity and location. In contrast, a reverse proxy is positioned between a client and a backend server, primarily to protect and optimize server operations. While forward proxies manage outbound traffic, reverse proxies handle inbound requests, improving security, load balancing, and server performance.
When using a reverse proxy, these client requests are sent to the origin server of the website, where the network edge from the reverse proxy sends requests to and receive responses from the origin server.
There’s a subtle difference between a reverse and forward proxy, but this difference is important.
A simplified way to look at this difference is:
- A forward proxy sits in front of a client computer and makes sure no origin server can directly communicate with the specific client server.
- A reverse proxy sits in front of an origin server and makes sure no client server can directly communicate with the origin server.
Why Would Someone Use a Reverse Proxy?
A reverse proxy is a great tool to use. A reverse proxy is used for several reasons, including enhancing security by hiding the identities of backend servers, protecting them from direct exposure to the internet. It also helps balance the load by distributing incoming traffic across multiple servers, preventing overload and ensuring consistent performance. Additionally, reverse proxies offer caching, which reduces server load and improves website speed. They also support SSL encryption, making it easier to manage secure communications across different servers.
Here are some reasons why someone might want to invest in a reverse proxy:
Load Balancing
A popular website may not be able to handle the incoming site traffic that the single server site experiences each day. The site can be distributed among many different servers when a reverse proxy is implemented.
This means that all these different servers can handle the requests for the same site. When a reverse proxy is used for this reason, the tool offers a load-balancing solution that distributes the incoming requests (traffic) evenly among the servers.
No single server is at risk of being overloaded when a reverse proxy is in place. Other servers are also available to step up and handle additional traffic if one server completely fails.
SSL Encryption
It can be expensive for an origin server to encrypt and decrypt SSL (or TLS) communications for every client request. A reverse proxy can be used to free up valuable resources on the origin server. That’s because it’s configured to decrypt all incoming client requests and encrypt the origin server’s outgoing responses.
Global Server Load Balancing
Load balancing that distributes a website on multiple servers across the world is known as global server load balancing (GSLB). When this GSLB configuration is set up, a reverse proxy will send client requests to the geographically closest servers. Load times can then be minimized because requests don’t need to travel long distances.
Protection from Malicious Attacks
A website or service isn’t required to reveal the origin server’s IP address when a reverse proxy is set up. It then becomes more challenging for attackers to cause any problems with the server, which prevents DDoS attacks from taking place.
The attackers can only target the reverse proxy, but these proxies are designed with tighter security and resources that fend off cyber attacks.
Caching
Another great ability of a reverse proxy is that it can cache content. This results in improved performance. An example of this would be a user in Paris visiting a reverse-proxied site where web servers are located in Los Angeles.
The user may be able to connect to a local reverse proxy server in Paris, which communicates with the “home” server in Los Angeles. This proxy server is then built to cache (temporarily save) any response information.
Any other Parisian users who decide to visit this same website will be able to access the locally cached version from the reverse proxy server in Paris. This makes the site performance a lot faster.
Better Protocol Adaptation
A reverse proxy can be used to convert incoming requests from one protocol to another. This allows clients who might use different versions or protocols to still be able to seamlessly interact with backend servers.
Reverse Proxy Challenges
Reverse proxies are great for website infrastructure. That’s because incoming traffic is easily distributed to backend servers. However, as with every type of technology, reverse proxies also come with a set of challenges.
Here are some of the common challenges associated with using a reverse proxy:
Security Risks
Security threats become likely if the reverse proxy isn’t properly updated or configured. Outdated software, misconfigured security policies, and mishandled user input can all lead to infrastructure being exposed to attacks like cross-site scripting (XSS), SQL injection, and more.
Bottlenecks in Performance
Reverse proxies are specifically designed to improve performance, but this technology can sometimes become a bottleneck. That’s if a reverse proxy isn’t properly optimized or configured.
Rather than making improvements to performance, inefficient load balancing, inadequate server resources, and improper caching settings often result in bottlenecked performance.
Complexity in Configuration
It’s complex to configure a reverse proxy, especially for more advanced reverse proxy setups. This configuration involves routing rules, caching, SSL/TLS termination, load-balancing algorithms, and other important features.
Installers are required to have a deep understanding of these technologies and the specific application needs. Without this knowledge, the configuration could become a costly failure.
Challenges Caching Website Content
We’ve already established that caching website content can significantly improve performance. However, this activity needs to be managed carefully. If the incorrect caching settings are put in place, outdated content can be presented to users visiting the website. This can potentially compromise the user experience.
Routing and DNS Challenges
Ensuring proper routing and DNS configurations can become problematic when multiple load balancers or reverse proxies are used. Any misconfigured routing rules or DNS records might cause traffic to be directed to incorrect locations.
Latency Issues
Issues with network latency can happen when reverse proxies are deployed in many different geographical locations. When this happens, users who are placed in locations far from the reverse proxy may experience slower response times. This is often because of the increased distance information needs to travel.
Benefits of Using A Reverse Proxy
A reverse proxy offers numerous benefits that enhance the performance, security, and manageability of web services. By distributing incoming traffic across multiple backend servers, it provides effective load balancing, ensuring no single server is overwhelmed, which improves reliability and performance. Reverse proxies enhance security by masking the identity and structure of backend servers, filtering out malicious requests, and protecting against distributed denial-of-service (DDoS) attacks.
By distributing incoming traffic across multiple servers, it improves load balancing and ensures that no single server is overwhelmed. Reverse proxies also enable caching, which speeds up response times and reduces the load on servers. Additionally, they simplify SSL encryption management, providing a streamlined process for handling secure communications across different servers. This results in better overall performance and scalability.
They also offer caching capabilities, which reduce load times and decrease the demand on backend servers by storing frequently accessed content. Additionally, reverse proxies handle SSL termination, offloading the resource-intensive task of encryption and decryption from backend servers, simplifying SSL certificate management. These features collectively improve the scalability, security, and efficiency of web applications, making reverse proxies a critical component in modern web infrastructures.
How Can You Address the Challenges of Reverse Proxies?
You need a combination of ongoing maintenance, technical expertise, and careful planning to effectively address the challenges of reverse proxies. Here are some ways you could tackle the challenges mentioned above:
Addressing the Security Risks
To properly address the security risks of reverse proxies, you want to regularly update your reverse proxy software. You also want to make sure you update the underlying operating system. This will help you patch any security vulnerabilities.
Addressing the Performance Bottlenecks
Regularly monitoring your server performance will help you identify any bottlenecks in your reverse proxy and help optimize your configurations. You also want to implement load-balancing algorithms to suit your specific application’s needs. Another great strategy would be to use compression and caching to reduce latency and server load.
Addressing the Configuration Complexities
You want to invest some time in understanding your reverse solution’s specific technologies. Once you have a good understanding of this, you can look at configuration management tools that can help you automate and standardize your reverse proxy setup.
Another important aspect you want to look out for is thoroughly documenting your configurations. By creating good documentation about your configurations, you can easily troubleshoot if issues do occur. Otherwise, you also have a good reference if you encounter future issues with your configuration.
Addressing the Caching Challenges
Caching issues are problematic because you don’t want to be giving users inaccurate or outdated information. Fine-tuning your caching settings can help prevent serving outdated content to your users.
You also want to create and implement cache invalidation strategies. These are tactics to ensure your caching continues serving your users with the most up-to-date content. Good cache invalidation strategies make sure that updated information is reflected in the cache.
Addressing the Routing and DNS Challenges
One of the most important things you want to do is ensure you have proper DNS configurations in place. From here, you also want to use DNS-based load balancing if your server needs it.
If you expect users will be accessing your server from other geographical locations, you want to have a global server load-balancing solution in place. This will ensure performance remains across different servers remains good for all users no matter their geographical location.
Addressing the Latency Issues
Latency issues happen when servers are distributed to different geographical locations. You want to implement content delivery networks (CDNs). This will help reduce any latency because your content will be stored closer to users.
While it’s good to implement content delivery networks, you can go a step further by optimizing network routes. You might want to also consider investing in Anycast. This will help route users to their nearest proxy server.
Is a Load Balancer a Reverse Proxy?
A load balancer isn’t a reverse proxy. These load balancers are used to help distribute traffic. This helps websites handle more traffic without crashing. Reverse proxies work as a “middleman” for origin servers and client machines when these communicate with one another.
Is CDN a Reverse Proxy?
CDN is a Content Delivery Network. This type of technology is designed to speed up the serving parts of any website. This is done from a location that’s closest to the visitor’s location.
Is an API Gateway a Reverse Proxy?
An API is specifically designed to let a user run commands on a platform. This is done without any need to log into a UI to manage the website. An example of this would be a customer being able to post a new blog post to their WordPress site without being required to sign into their WordPress dashboard.
Final Thoughts on Reverse Proxies
Reverse proxies can be defined as the traffic police of the internet. This technology is specifically designed to help distribute all incoming traffic to a site while making things faster and keeping all operations secure.
Like with any type of function, challenges are part of the journey. Your biggest strength in dealing with these challenges is creating a well-informed plan. By following the strategies we outlined above, you can help to mitigate these reverse proxy challenges.
A good reverse proxy setup lets you create a better user experience, contributes to a stronger security posture, and helps successfully deliver web services to users across the globe.
Clear documentation, comprehensive monitoring, regular updates, and careful configuration are all crucial factors in effectively implementing and maintaining a reverse proxy setup.
When done well, you can leverage the power that reverse proxies have to offer. However, inefficient management will stop you from creating a robust, secure, and efficient web infrastructure.