SOCKS5 Proxy: A Comprehensive Guide for Everyone
In the evolving world of technology where exclusivity should be enhanced, censorship is a major concern, impacting those restricted by location or those looking to simply access internet content. A firewall exists between a client and the Internet, preventing access to certain web pages or applications. This is where a SOCKS5 proxy can come into play.
But how can these firewalls be bypassed without negatively impacting the data security and privacy of a client? How can SOCKS5 proxies foster communication between a smaller server and a bigger one while masking a client’s IP address?
In this comprehensive guide, we explore the SOCKS5 proxy in its entirety, how it works, and how it can be set up and configured on different operating systems to bypass firewalls and give clients undeniable access to restricted sites, applications, and internet content without compromising on security.
What Is A SOCKS5 Proxy?
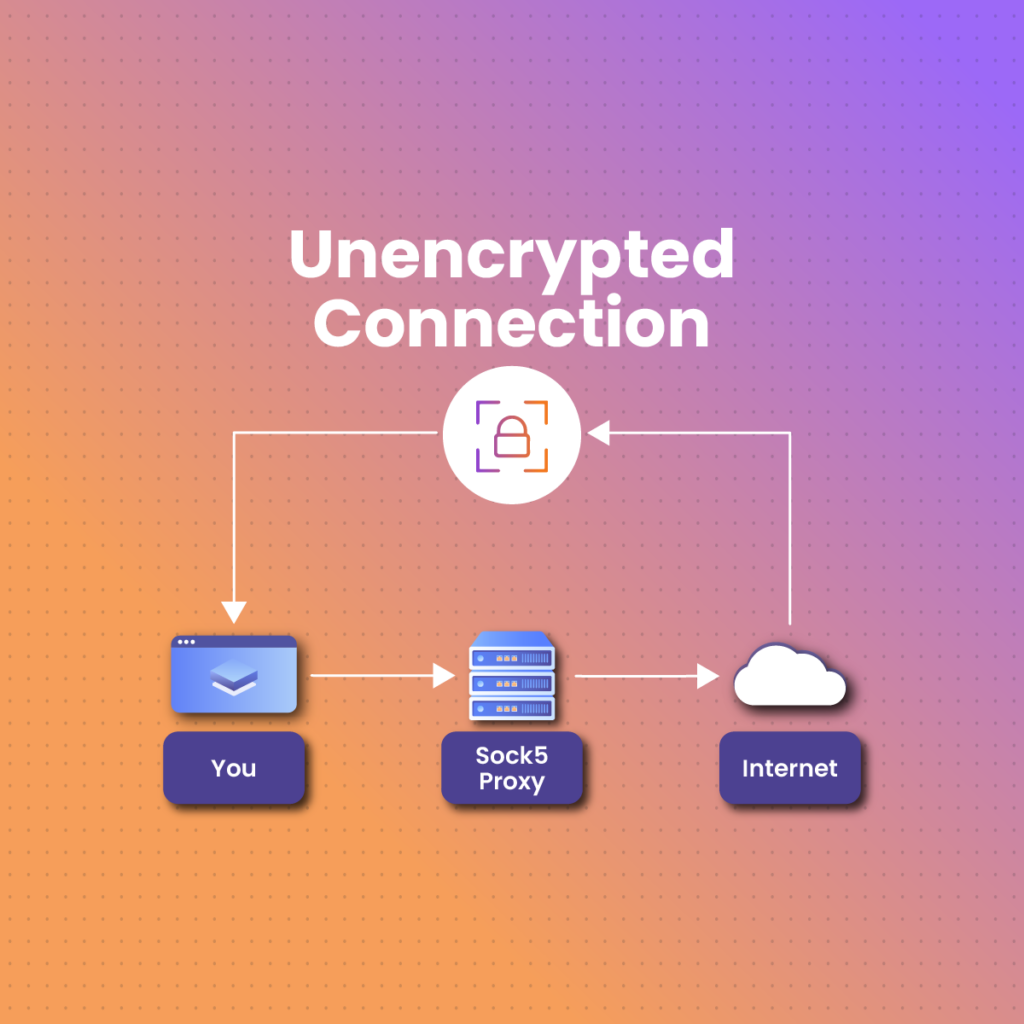
SOCKS5 proxy (socket secure – 5) is a fifth-layer proxy that enhances communication between two servers separated by a firewall on behalf of a client. For instance, if A wants to send a message to a bigger server B and the message is interrupted by a firewall, it won’t deliver. So the SOCKS5 proxy bypasses these firewalls on behalf of A so communication is possible. Basically, A pairs with SOCKS5 to send a message to server B.
A SOCKS5 proxy is a versatile and robust internet protocol that facilitates the routing of network traffic through a proxy server. Unlike its predecessors, SOCKS5 supports a wide range of protocols and types of traffic, including TCP and UDP, making it suitable for various applications such as web browsing, file transfers, and gaming. This protocol enhances privacy and security by masking the user’s IP address and ensuring data integrity with advanced authentication methods. Additionally, SOCKS5 proxies offer improved performance with lower latency, providing a more seamless and efficient browsing experience.
SOCKS5, in itself, is a framework for a General Proxy Protocol as it allows several application layer protocols such as HTTP, HTTPS, and FTP to relay data securely and transparently. Ideally, these application layer protocols require that a different proxy server be set up before data can be shared. But SOCKS5 changes the status quo.
Additionally, SOCKS5 enhances the free flow of traffic, bypassing internet content that has been blocked or filtered by governments, schools, workplaces, or country-specific applications. However, only authorized users can access a service with a SOCKS5 proxy.
Now, let’s go further to understand the purpose and benefits of the SOCKS5 proxy.
Purpose and Benefits of SOCKS5 Proxy
Earlier, we saw how the SOCKS5 proxy facilitates communication between two different servers separated by a firewall, giving authentic users access to filtered or blocked content on the internet.
Below, we will be exploring four main benefits of the SOCKS5 proxy which include access to cluster back-end services, easy setup, absence of third-party servers during deployment, and better performance.
Access to cluster back-end service
To cushion against security vulnerabilities, clusters are hosted in the cloud behind a firewall. Accessing backend services in a cluster could involve exposing backend services to the public and accepting the security risks or whitelisting a client or user’s IP address to drive traffic to the backend service. These strategies, however, are limited due to security risks and eventual changes in a user’s IP address.
A great alternative to this is a SOCKS 5 proxy with a dynamic port forwarding using SSH to access the backend cluster hosted behind a firewall to enhance monitoring, debugging, and administration from a public network while maintaining optimal security.
For instance, if you are working on a virtual private cloud (VPC), a bastion host with a SOCKS5 proxy can be deployed to securely access remote instances in the VPC while limiting exposure to the public.
Easy setup
Setting up the SOCKS5 proxy is pretty easy if you have access to an SSH in the edge node or cluster gateway. This will let administrators or developers access backend resources with an SSH tunnel, without the need for a virtual private network (VPN).
Absence of third parties during deployment
Using SSH tunneling, the SOCKS5 proxy can route any kind of TCP or UDP traffic to the respective service. As such, no layer 7 application-related special proxies are needed for each service to route application requests.
Better performance
SOCKS5 has fewer errors compared to other proxies. It doesn’t rewrite packets of data, rather it relays traffic between devices, making it less error-prone with optimal performance.
How Is A SOCKS5 Proxy Different Compared To Other Types of Proxies?
A SOCKS5 proxy stands out from other types of proxies due to its advanced capabilities and versatility. Unlike HTTP proxies, which only handle web traffic, SOCKS5 proxies can manage any type of traffic, making them suitable for diverse applications such as email, file transfers, and peer-to-peer networks. Additionally, SOCKS5 offers enhanced security features, including improved authentication methods, which provide an extra layer of protection compared to other proxies. This flexibility and security make SOCKS5 a preferred choice for users seeking robust and comprehensive proxy solutions.
Before we see the differences between SOCKS5 and other proxies, we must understand proxies are essential parts of the modern internet. In simple terms, they connect your laptops to the internet. We’ll be comparing SOCKS5 with other proxies such as HTTPS and HTTP based on several factors – security, speed, compatibility, and more.
Security and proxy level
By operating higher internet security, HTTPS is considered a high-level proxy. It strengthens the security layer between the client and the server. As such, suspicious data can be detected and denied. Irrespective of data sensitivity, HTTP proxies understand the transferability of data between a client and a server.
SOCKS, on the other hand, access connections outside the firewall, limiting a client’s access. HTTPS safeguards your data while using the internet through its robust encryption that secures and protects your information while engaging in activities such as torrenting and downloading large files.
While SOCKS proxies can be susceptible to man-in-the-middle attacks, SOCKS5 incorporates an SSH encryption tunneling method to increase security.
Speed
HTTPS has both private and public proxies that allow you to manage activities with ease or stress. Speed is a course for concern with public proxies. Similarly, the speed of HTTP proxies depends on whether it is private, shared, or general.
SOCKS5, on the other hand, has a faster speed compared to HTTP and HTTPS since it has fewer codes to run during computing.
Compatibility
While SOCKS is compatible with different environments and can handle all traffic types, HTTP uses the HTTP protocol to receive pieces of information through a web browser. While ports 80 and 443 connections (HTTPS and SSL) are only supported on HTTP, ports 1080 and 1081 are mainly reserved for SOCKS proxy, even though they support any other port. HTTP and HTTPS proxies can connect with various tools, unlike SOCKS which is highly limited.
The table below briefly outlines the major differences.
|
Proxy Type |
Security and Proxy Level |
Speed |
Compatibility |
|
SOCKS |
Susceptible to man-in-the-middle attacks. Incorporates SSH tunneling for encryption |
Faster in operation |
Compatible with different environments and can handle all track types |
|
HTTPS |
Robust encryption models |
Speed depends on whether the server is private or public |
Less compatibility range. Connects with several tools compared to SOCKS |
|
HTTP |
Less secure compared to SOCKS5 |
Speed depends on whether the server is private, shared, or general |
Supports only port 80 and 443 connections |
How SOCKS5 Proxies Works
We live in a dispensation where numerous content on the internet is filtered. A proxy such as SOCKS5 will be useful to get through such content. In this section, we’ll be exploring how SOCKS5 works.
A SOCKS5 proxy helps clients route network packets that exist between them and restrictions on the internet. This proxy works like an icebreaker to foster communication between a client and the internet by pulling down the blockades and enhancing access to web services.
Looking at it technically, SOCKS5, a fifth version of the SOCKS proxy, uses different proxy servers to create User Datagram Protocols (UDP) or Transmission Control Protocols (TCP) using arbitrary IP addresses. For instance, if a website is filtered to accept access from networks with 2.2.2.2 IP addresses, viewing the site will be challenging if yours is 1.1.1.1 or something different. To bypass this blocker, a SOCKS5 proxy will route your traffic to 2.2.2.2, making the destination server think your request is coming directly from the accepted IP address.
While your original IP address is masked and your location is hidden, it doesn’t mean your traffic will be absolutely secure.
To see what accessing an Endpoint protocol using a SOCKS5 proxy looks like, keep reading to see how this proxy can be set up and configured.
Now, let’s check out the structure of a SOCKS5 proxy and how it can be authenticated.
Structure and Authentication Methods of SOCKS5 Proxy
To understand the structure of the SOCKS5 proxy, let’s look at it from the client-server mechanism. The proxy acts as an intermediary, distributing traffic between the client and the server. The client has to connect with this proxy to send a message to the server. For the message to be relayed to the server, the proxy will analyze it and establish further connections with the server on behalf of the client. This way, a client’s real identity is shielded from the server.
In terms of authentication, SOCKS5 is quite flexible, offering several authentication methods. Some of these methods include”
- No authentication: Here, the proxy allows a user to connect without requesting any credentials.
- Generic Security Services Application Program Interface (GSS-API) authentication: This ensures whatever program you’re trying to access is not only secure but also compatible with the SOCKS5 proxy.
- Login credentials: To prove your identity, the proxy prompts you to fill in your username and password.
By handling traffic from both TCP and UDP, SOCKS5 is a major enhancement over SOCKS4 which mainly handles TCP traffic. This makes it a versatile and comprehensive approach in the proxy landscape.
Use Cases of SOCKS5 Proxy
Being versatile by itself, the SOCKS5 proxy has a variety of use cases for different goals. The most common use case is bypassing online firewall blocks. Others are general anonymization and website access. It’s what noting that some of these proxies require setup and configuration before usage. For others, you simply install the software and start using it directly.
Below, we explore the prominent use cases of the SOCKS5 proxy.
General Anonymization
A major use of SOCKS5 is to enhance online anonymity and privacy in general. With this proxy installed on your device, your identity remains unknown even if you’re using a public WiFi connection. The websites you visit, your IP address, and data traffic will be hidden. Additionally, you bypass firewalls, allowing you to access geographical-based applications that are unavailable in your location with your masked IP address.
Access to Websites
Globally, some websites or online content are geographically restricted. This means you may have limited or no access to these sites or content if you don’t reside in such locations. But you can bypass these blockers and have unlimited access to these websites or applications with a SOCKS5 Proxy whenever you want.
Bypassing Firewalls
Online restrictions have now taken center stage with many office and school networks having firewalls, choosing which websites or applications should have access to their network. With the SOCKS5 proxy, you bypass these blockers to access various sites for work such as video conferencing platforms and file-sharing tools. You may need to set up and configure the proxy to have access to these sites.
Other use cases for this proxy include:
- P2P file sharing
- Torrenting
- Online gaming
- Reduced latency
How to Setup and Configure SOCKS 5 Proxy
To effectively introduce and set up a SOCK5 proxy, it’s recommended that a client’s application, whether Windows, Google Chrome, Linux, or MacOS software, is compatible with the protocol. For instance, let’s see what the syntax on the SSH client of a Linux computer looks like and how it can be authenticated to the Edge node of a cluster hosted in the cloud behind a firewall.
<SSH -D 30001 root@EdgeNodeSSHserverIP -C -f -N (<password>))
After entering this command, the SOCKS5 server starts and is bound to port 30001. It then connects to the cluster that is hosted in the cloud (Edge Node) above the SSH tunnel.
Here’s how the chain of communication works:
- D 30001 directs SSH to create a SOCKS5 server and bind it to port 30001 on a client’s server.
- This data is now compressed by C and sent along
- While this doesn’t apply to SOCKS5, N denotes “Don’t implement a remote command.
- The SSH goes to the background just before execution, all thanks to F.
How To Set Up and Configure SOCKS5 For Windows
Setting up and configuring the SOCKS5 proxy for Windows starts with purchasing the proxy from a reputable service provider. Ensure to collect all pieces of information related to the proxy such as its IP address, port number, and authentication credentials if applicable. The main purpose of getting the proxy is to bypass firewalls while maintaining absolute privacy and anonymity.
Once this is done, you can follow the steps outlined below to set up and configure the proxy on your device:
- Access the proxy settings by opening the control panel when you click on the start menu. Next, you search and click on “Internet Options.”
- Configure the internet option by navigating to the “connections” tab in the “Internal properties Window.” Then click on the LAN settings buttons.
- Configure the LAN settings by selecting “use a proxy for LAN in the settings. Then, enter the SOCKS5 IP address and port number in the address field and port field respectively.
- If you were provided with authentication, you can configure advanced proxy settings by clicking “Advanced settings” on the LAN. Enter the proxy’s IP address and port number in the section tagged “Proxy Server.” Then, enter the authentication details in the “secure section.”
- Click “OK” to save and apply all changes. Clicking OK twice will close the LAN settings and internet properties windows.
- You may proceed to test the proxy by visiting websites that you wouldn’t have access to without the proxy.
You shouldn’t have a difficult time setting up and configuring your SOCKS5 on Windows. However, there may be slight variations depending on the model of Windows.
How To Set Up SOCKS5 Proxy On MacOS
Again, this process starts with getting a suitable SOCKS5 proxy from a reputable provider and getting all supporting information regarding the purpose.
Below, we explore the steps in setting up and configuring the proxy on your account.
- Click on the Apple menu at the top left corner of your screen to access Network preferences and then select “System Preferences.”
- Proceed to click on the network icon select “Active Network Connection” and then choose the network in use at the moment (WiFi or Ethernet)
- Click on “Advanced” which will appear at the bottom-right corner.
- Proceed to configure proxy settings by clicking the Proxies tab and ticking the box for SOCKS proxy.
- Enter the proxy server details, that’s the IP address and port number, in the required sections.
- If you were provided with authentication details, you can also configure that by entering the username and password in their respective fields.
- Save and apply all changes by clicking “OK.”
- Test the proxy by visiting a restricted website.
How To Set Up SOCKS5 Proxy For Chrome
If you use Google Chrome as your main browser and plan to use SOCKS5 for browsing activities alone, a Chrome-specific proxy that exists as an extension should come in handy. But how would you set up and configure a SOCKS5 proxy for your Chrome browser?
We’ll be exploring the steps below.
- Purchase and download the proxy software from a reputable service provider. Ensure to collect all authentication credentials.
- Navigate to the Chrome settings by opening the browser on your laptop and clicking on the menu at the top-right. From the dropdown menu, select “Settings.”
- Click on “Advanced Settings” and “Open Proxy Setting”
- From the “Systems” section, click “Open your Computer’s Proxy settings Link.” This will take you to either your Windows or MacOS Network settings.
- Continue the setup and configuration process using the steps involved in either the Windows or macOS setup. This, however, depends on your type of operating system.
Accessing Backend Services Using SOCKS5 Proxy
As stated earlier, the SOCKS5 proxy facilitates communication between a client and a backend service cluster hosted in a cloud behind a firewall. But how does this happen?
Let’s demonstrate this below!
Once you’ve set up and configured the proxy, you can use a simple URL command line to access an HTTPS application backend on port 8000 using the SOCKS5 proxy.
curl -x SOCKS5h://localhost:30001 -v -k -X GET
HTTPS://EdgeNodeSSgserver/P:8000
This command links to port 30001 on localhost and as the HTTP GET request is received on port 30001. The SSH client sends the same request to the SSH server.
The remote SSH server processes the request and sends it to the backend service on port 8000. Through the same SSH tunnel, the response is sent back to the client’s SOCKS5 which is further delivered to the UrL command.
Best Practices for Using SOCKS5 Proxy
While the SOCKS5 proxy works to give you unlimited access to online content, websites, and applications that have some form of restrictions, how do you make the best of it?
Below, we’ll be exploring five best practices that should be followed when using this proxy.
Opt for Reputable Providers
Before getting a SOCKS5 proxy, conducting thorough research on the vendor is essential. Check out the reviews, track records, and even ratings. You need unrestricted access but your data security shouldn’t be compromised.
Security and Privacy
While conducting any online activity, your security and privacy need to be at optimal levels. To further enhance anonymization your proxy should be encrypted or used in addition to tools such as virtual private networks (VPN).
Authentication credentials
Using a SOCKS5 proxy backed with an authenticator provides an extra layer of security for your data. If your vendor offers one, you should go for it.
Updating configuration status regularly
The configuration settings of a proxy are subject to change and SOCKS5 isn’t exempted. This makes it essential to regularly update your proxy settings including the IP address, port number, and authentication credentials as recommended by your vendor.
Choose the right server
Several SOCKS5 proxies exist. It’s, therefore, ideal to choose one that is compatible with your operating system, network,e, and location.
Frequently Asked Questions About SOCKS5
What are the main differences between SOCKS5 and SOCKS4 proxies?
Both SOCKS5 and SOCKS4 are socket-secure protocols. The main difference is that SOCKS4 is an older model that offers basic proxy functions and is limited in supporting advanced features such as UDP and authentication.
What is a VPN?
VPNs, also known as virtual private networks, are services that enhance your privacy while optimizing your internet connection. They are usually encrypted to protect your data online by hiding your IP address, even when using public WiFi hotspots.
Can VPNs work with a SOCKS5 proxy?
Yes, VPNs can work with SOCKS5. While SOCKS5 enables clients to bypass internet restrictions in a secure and private atmosphere. VPNs, on the other hand, can be manually configured and used with SOCKS5 to strengthen the encryption and provide more security and anonymity.