Proxy Chaining: How It Works and Why You Should Use It
There’s a common school of thought that the internet is at its best when it’s open, free, and freely accessible. While such a pipe dream sounds great, this is not the reality of the world which is why many individuals will start researching proxy chains and proxy chaining.
You will find censorship, online restrictions, and security concerns at almost every turn. This leaves many to consider what they can do to access the internet in the way they wish.
One option that people may turn to is VPNs, and this is often because that is the avenue known to assist with this kind of thing. Be that as it may, it’s not the only route you can go, and it’s not necessarily the best one either.
In fact, some of the providers out there that are advertising VPNs are not necessarily offering them to their customers in their truest sense. Instead, they are selling proxies as a service.
On that note, we’ll segue into what we’re here to talk about, which is the idea of proxy chaining. Before we get there, we’ll cover proxies at a high level, just to ensure you’re familiar with all that is going on. Following that, we’ll talk about the chaining, advantages, disadvantages, benefits, and even comparisons to the VPNs.
The Unprotected Work Problem
This is the core of why you would even need one of these services in the first place. It comes from the way the internet is used and how people access resources. Whether it’s playing a game on the Internet, visiting a social network, engaging in e-commerce, or downloading files, whatever device you use will be sending requests over the internet.
That’s to be expected, but it also carries a level of risk. That’s because information such as your actual public IP address is being sent over the air, and this process creates the possibility of your personal information falling into the hands of unscrupulous and malicious parties. One challenge that creates is such entities being able to connect to your machine.
In doing so, it becomes possible to steal your personal information for annoyances, such as spam, all the way up to serious issues such as identity theft. Alternatively, your device itself can be crippled through the sending of malware. It may even be used as a node for the illegal activities that these parties want to carry out.
Bear in mind that these are only a few of the more popular challenges that come with the way the internet is accessed, which is unprotected to a large extent by default. The idea behind a standard proxy setup is to minimize these kinds of risks, and this is why the idea of proxy training comes to the fore to stack the benefits.
What Is Proxy Chaining?
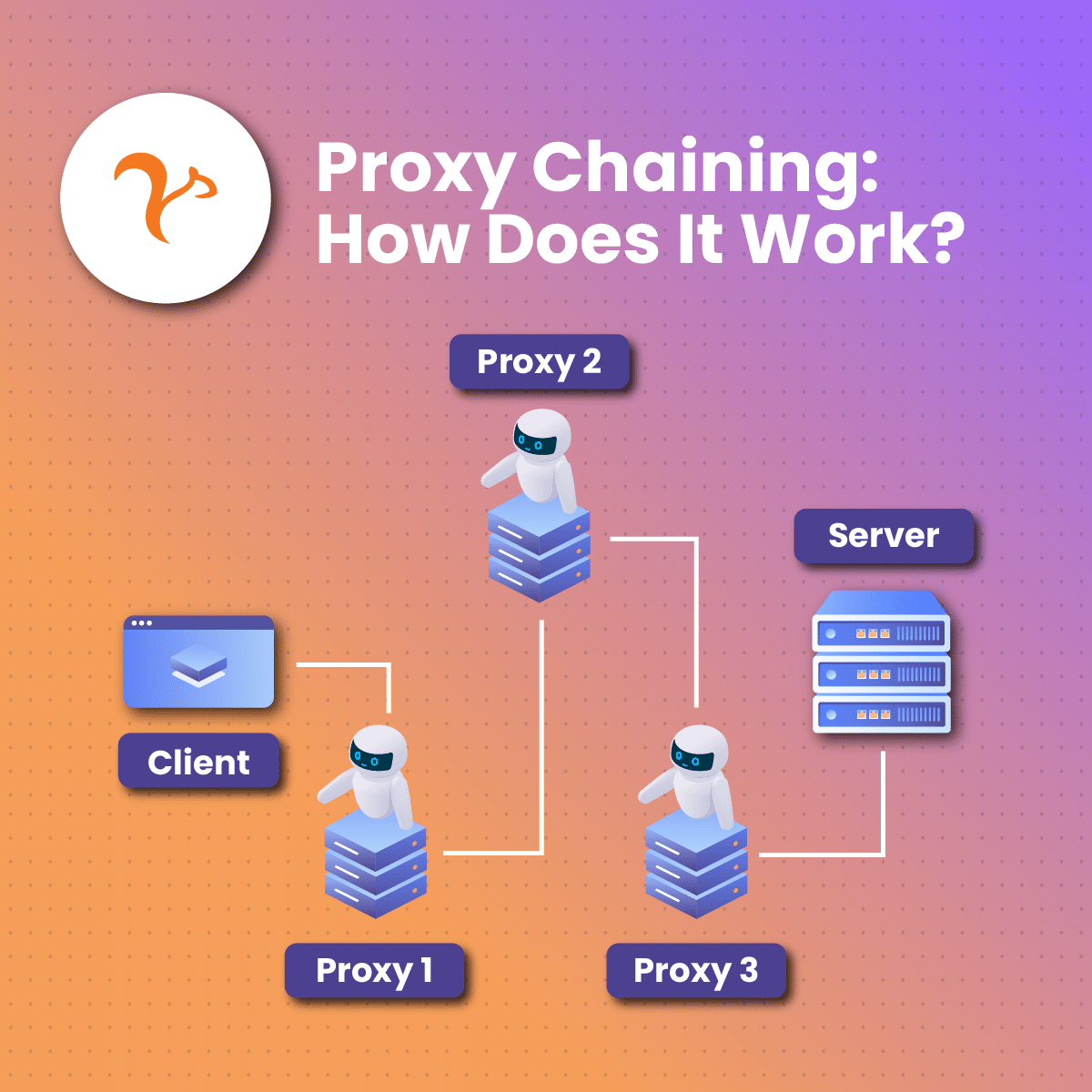
Now that we’ve covered proxies extensively, it’s time to turn our attention to the idea of proxy chaining. Unlike simply having a proxy server which is a bit more on the simpler side, proxy chaining is a more involved process that masks a proxy server behind another proxy server as many times as desired.
Recall that the implementation we covered before was simply using a single proxy server as an intermediary with the actual node behind it. Now, there is the node, a proxy server, another proxy server, and possibly even more, which will offer multiple layers of packet processing and masking, ensuring greater anonymity.
Remember that the idea of proxies is to keep the actual addresses and devices behind them anonymous while allowing for the bypassing of internet blockages that may be based on criteria such as geography.
It’s the same kind of topology as a standard proxy implementation, with the number of middlemen being increased. As you can imagine, with more proxies in the mix, it’s a lot more difficult for firewalls you may run into to be able to identify your proxy and implement any kind of blockage.
Therefore, circumventing censorship becomes that much easier. While a single proxy certainly provides a great level of security, tracking and cracking it is a lot easier when there is one than when there are four, five, or even six. Be that as it may, bear in mind that it’s still not necessarily impossible.
Key Features of Proxy Chains
A few of the top features of the proxy chaining approach that you would be looking to take advantage of are:
- Application agnostic: Once the desired application uses a TCP/IP stack, it becomes possible to apply this kind of approach. Therefore, you’re getting a universal level of usefulness out of any such implementation.
- Multiple proxy support: This is the core of a chaining setup, and leveraging a series of servers is important for that added layer of security.
- Versatility: A range of online activities are supported including network scanning, data transfer, web browsing, etc.
Exploring the Importance of the Approach
Proxy chaining is important to achieve a few key objectives, which are as follows:
- Security: There’s a reason why cybersecurity enthusiasts and experts will use chaining themselves to help with avoiding detection and tracking. This is particularly useful in penetration testing and ethical hacking exercises. Put simply, as the path between source and destination becomes more complex, investigators or cyber criminals have a harder time tracing activity.
- Anonymity: Masking your IP address allows you to maintain the privacy of your online activities, which is an essential function in a digital world that is becoming progressively more unsecure.
- Bypassing restrictions: Online services are not always openly accessible. With a series of proxies featuring different locations around the world, bypassing restrictions such as geographical ones becomes possible, meaning you can gain access to what would previously be blocked content.
Best Practices for the Use of Proxy Chaining?
As is the case with just about anything in the world of technology, you’ll want to implement best practices to ensure the setup is optimal and achieves the desired function. Here are three things you will want to do as a part of your proxy chaining exercise:
- Proxy server verification: There are a lot of proxy server providers out there, and the onus is on you to ensure you’ve chosen the right one. Stick to reputable and reliable options if you want to maximize the amount of security you have.
- Header configuration: This will depend on if the chain is being set up manually. If so, you want to ensure that your headers are properly set up for identification and tracking purposes. Headers such as your X-Forwarded-For are important here.
- Testing: This should go without saying, but there is still value in mentioning it. You’ll likely be using your proxy chain for critical tasks. Before you start doing this, it’s critical to ensure that this setup is working as intended. Start things off with a couple of test exercises.
Benefits of Proxy Chaining
As is the case with just about anything, chaining comes with a series of advantages and disadvantages. Let’s start by looking at the upsides:
- Security – This ties into what has been said before. A greater number of proxy servers means a harder trucking path, meaning it’s easier to maintain your anonymity on the web. Each proxy server in turn offers a level of masking to the one before it, all the way to the actual node.
- Speed – With more proxy servers in the mix, there is a greater operational capacity of each one for four packet processing before sending them back to the user. There’s a reason why these chains are known for being a speedy restriction bypass option.
- Caching – Caching is simply the storage of data on domains previously visited. Instead of sending the whole request again, the stored data will be used to facilitate quick access, even going as far as to remember website preferences. Of course, on the server side, the use case is more along the lines of storing pages to be served upon request. More proxies mean better caching, leading to greater efficiency and speed.
Drawbacks of Proxy Chaining
- Points of failure: Usually, in a technological implementation with multiples of any one thing, the idea is to create redundancy, removing single points of failure. Proxies are not used in a load-balanced manner for chaining. Since all of them are in turn being used for a single effort, every part of the chain needs to be operational for it all to work. This creates high dependence on each server, in turn, requiring reconfiguration if one stops working.
- More complex proxy chaining designs require more servers, meaning there will be a greater cost to factor in. Remember there is server maintenance and bandwidth to think about.
Understanding Proxies
In simple terms, a proxy allows for the hiding of client public IP addresses, which grants a level of anonymity. This is achieved because the address revealed is that of the proxy, which is an intermediary node standing between your device and those on the internet, which requests are being sent to.
Being the middleman, the proxy server will simply forward any requests you send and act on your behalf as you carry out whatever tasks you need to on the communication network.
This function is not necessarily only available on your side of the fence. Depending on the setup and application, there may be concerns with people being able to directly reach the server that is being used to provide certain services on the internet. Proxies will then be used to prevent that kind of direct communication.
Apart from hiding IP addresses, there are other benefits such as caching that this allows for. The proxy on the server side will cache the data and use these cached pages to handle incoming requests. This reduces the potential for server crowding and also lowers the response time for the service being provided.
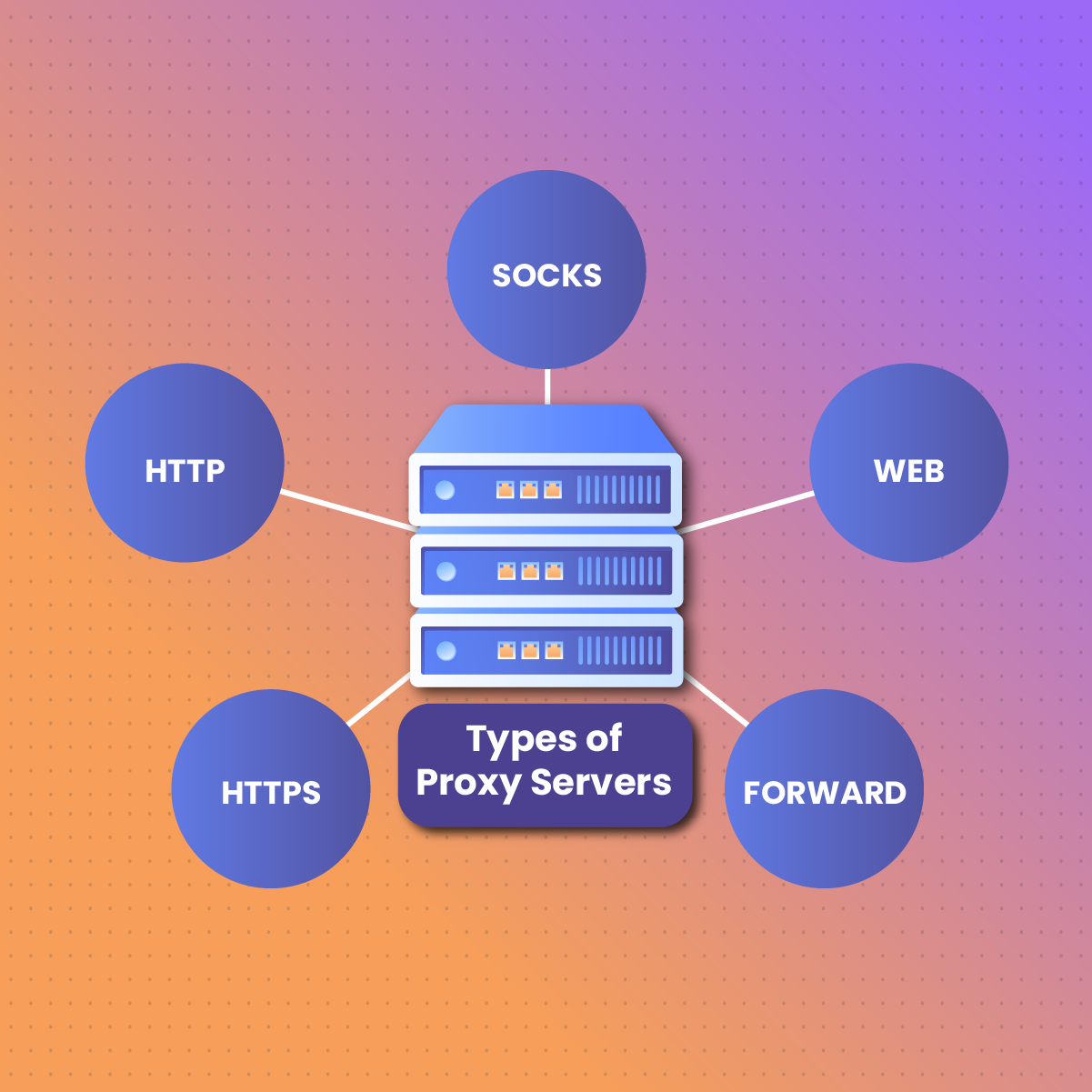
Types of Proxies
Depending on the design specifications and purposes being served, you will find different kinds of proxies out there. Here’s a look at them in the context of anonymous navigation:
HTTP/HTTPS
As the name implies, this is what you would use to adequately filter information over both the HTTP and the more secure HTTPS protocol. These are the easiest proxies to find, and they are arguably the most popular too. You’ll find that these are highly responsive, but they are also restricted to their protocol.
SOCKS4
If you go this route instead of opting for an HTTP/HTTPS proxy, you gain the ability to reroute TCP data, which is largely beneficial. In other words, not only can you filter World Wide Web services on a TCP basis, but you also get the ability to do so on any protocol that supports that kind of service. There is also a SOCKS4 variant you may find.
SOCKS5
This is not too far removed from the previous iteration, but it adds the ability of UDP data rerouting, which presents another layer of safety. Additionally, there is IPv6 support and the ability for proxy owners to set up internal authentication systems. Any kind of software using an internet connection allows for the use of these proxies. Examples include P2P programs, chat, mail, and more.
Web (GCI)
These are actual websites and require no particular tools or configuration on the computer. Therefore, direct navigation anonymously becomes possible. There are dozens of these to be found online.
Standard Proxy Products
When the desire is to have robust security and effortless web navigation, different options are available as you delve into proxy products. Here’s a quick look at them.
Rotating Residential Proxies
This is a dynamic rotating service, which will offer a slew of residential IPs that come from real worldwide end-user devices. Because the pool is so massive, it becomes possible to access websites and services in just about any country.
Some of the benefits to this kind of service when implemented well include the lack of intermediaries needed for better scalability and uptime, optimal IP management, faster web scraping through residential ISP connections, and the preservation of anonymity by avoiding the use of US peer proxies.
Static Residential Proxies
In a different approach to the rotating option discussed above, this variant will provide you with static residential IPs for as long as needed. There are real users behind prefixes, fast one-hop proxy connectivity, and 24/7 availability of tons of static IPs when such a service is designed well.
The idea is to provide reliable, fast, and completely anonymous access to a worldwide ISP proxy network that should be able to satisfy just about any use case.
Mobile IPs
Mobile proxies are next on the list, and these are meant to be unblockable. Again, a good design necessitates numerous mobile IPs across numerous countries being available. Additionally, 3G, 4G, 5G, and LTE mobile proxies should be supported, and there should also be a near-perfect success rate.
The service allows for leveraging of country-level targeted locations, meaning there should be an optimal IP pool regardless of where you are. Of course, uninterrupted connectivity is to be expected.
Datacenter Proxies
A data center proxy network is intended to be highly scalable since the intention would be to provide peak performance to both individuals and businesses. Some of the desirables include easy proxy management, concurrent connections with numerous domains, high levels of uptime, and a great pool of capability.
The idea is to deliver high levels of stability, quality, speed, and support.
How Does Proxy Chaining Stack Up Against a VPN?
It’s not uncommon to see the conversation come up surrounding how a proxy chain stands up against a VPN, since both are technically used for browsing anonymously and providing a higher level of security than you would have by default.
Which of the two you use is going to depend on your unique requirements. For example, it’s much easier to get a standard VPN application going than it is to set up a proxy chain. Similarly, the VPN’s maintenance requirements are lower.
Therefore, if you were looking to go whichever route is easiest, then a standard VPN subscription is what you would go with.
However, if the privacy and anonymity elements are most important to you, then you may want to consider choosing a proxy chain instead, considering all the route complexity that the process yields.
Sometimes, you may find that your VPN doesn’t do as well as you’d like with bypassing internet censorship. In fact, a standard proxy setup may run into the same problem. In these cases, a proxy chain is going to be your best bet.
Finally, consider the fact that proxy chaining allows you to take advantage of concurrent use of multiple instances, and with extensions in the mix, you can even change your proxy server on the fly as required. This kind of involved configuration is not usually possible with a VPN.
Considerations When Choosing Your Provider
Choosing your provider for any critical internet service is always a process that should come with much-involved thought. As far as anything proxy-related goes, you are putting the fate of your security into the hands of third parties. It stands to reason that you would want to do some important due diligence first.
The first order of business is the reputation side of things. What do ratings and reviews look like? You’ll want to understand where the provider sits as far as casual and expert opinions go. Experiences are always unique, but at least you can look for certain patterns to help you get a feel for what yours may be.
Next, consider the offerings being presented and the extent to which these align with your needs. For example, some service providers have a broader reach than others. This means that there will be more locations and IP addresses available. The principle “the more, the merrier” applies here.
Performance guarantees are also essential. What does the uptime look like? What kind of references are being made to speed? Are you being offered a scalable service? You likely have specific applications and use cases that drove you to look at proxy chaining in the first place. Keep these in mind as you are making your selections.
Finally, there is the matter of pricing. This does not necessarily fit into the capability piece of the puzzle, but thinking about your budget is always essential. What you should be trying to achieve is getting the best value. Therefore, you’re not necessarily looking for the most expensive service, and you’re not looking for the cheapest one either. What you want is the best match of price and functionality.
Wrapping Up
It’s not uncommon to use proxies to add a layer of encapsulation to traffic as you browse the internet and use the services you need. As proven as that approach is, there is great value in going the proxy chaining route, using multiple servers in succession for greater anonymity and security, since the packet travel process now becomes more obscure.
Not only do you now have a better understanding of how chaining works, but you can also consider when to use one versus a VPN, and you even know the upsides and downsides of the implementation. Remember to carefully consider what providers offer before making any final decisions.
Frequently Asked Questions About Proxy Chains
Is Proxy Chaining a Better Option Than Using a VPN?
It’s not a good idea to think of a proxy chain or a VPN as being objectively better than the other. Instead, think about the use case to decide. A standard VPN subscription that offers encapsulation at the application layer is going to be easier to manage and get started with than a proxy chain.
However, you are going to get greater anonymity and security from the chain than if you were to opt for the VPN.
Do Proxy Chains Grant Full Anonymity?
While proxy chaining definitely makes you harder to track, it’s still not impossible.
Is There a Limit to the Number of Proxies That Can Be in a Proxy Chain?
While there isn’t a limit, if you want to avoid diminishing marginal returns and too much complexity on your end, you’re not typically advised to go over four proxy servers.